What is Fileless Malware & How to Detect Them
What is Fileless Malware?
Fileless malware is a sophisticated type of cyber threat that operates entirely in memory, without writing files to the disk. Unlike traditional malware, which relies on executable files stored on a system, fileless malware exploits legitimate system tools and processes to carry out its attacks.
Key differences:
- Resides in RAM instead of on disk
- Leverages legitimate system tools (e.g., PowerShell, WMI)
- Leaves minimal traces on the system
- Often uses social engineering tactics for initial infection
Growing Threat of Fileless Malware
The prevalence of fileless malware attacks has been steadily increasing over the past few years, posing a significant threat to organizations worldwide.
Fileless Malware represents 3/4ths of all Malware Incidents in 2023 & it grew at a staggering 72% over a period of 5 years
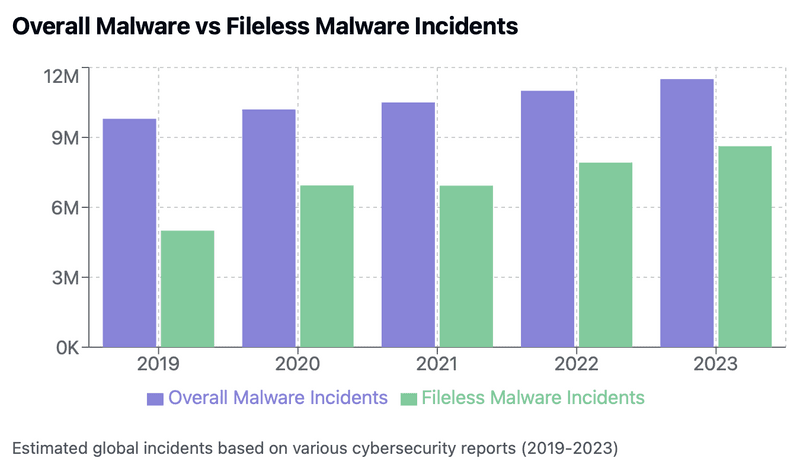
The rapid growth in Fileless Malware incidents compared to the slower growth of overall incidents indicates a clear shift in attacker preferences and techniques.
Key statistics from Security Vendors:
- The 2022 CrowdStrike Global Threat Report noted a 30% increase in fileless malware attacks compared to the previous year.
- The 2023 Verizon DBIR reported that fileless malware was involved in 52% of all system intrusion incidents globally.
- Over 60% of ransomware attacks now involve some form of fileless component (Sophos 2023 Threat Report).
- 68% of organizations say their traditional security solutions are ineffective against fileless attacks (Ponemon Institute, 2023).
Types of Fileless Malware
- Memory-only malware: Operates entirely in RAM without touching the disk
- Fileless persistence malware: Uses registry keys or scheduled tasks to maintain presence after reboots.
- Hybrid fileless malware: Combines fileless techniques with traditional malware components.
- Living-off-the-land attacks: Exploits built-in system tools for malicious purposes.
Why Fileless Malware is Effective
- Legitimate tools abused: PowerShell, WMI, regsvr32.exe, and even Node.js are all legitimate tools that are weaponized in these attacks.
- Living off the land: These malware examples "live off the land" by using built-in system utilities, making them harder to distinguish from normal system operations.
- Cross-platform threat: While Windows is a common target, fileless techniques are also applicable to other operating systems like Linux.
- Evasion techniques: By operating in memory and abusing legitimate processes, these malware examples are adept at evading traditional file-based detection methods.
- Complexity of attacks: Many of these examples involve multi-stage attack chains, demonstrating the sophistication of fileless malware campaigns.
Case Studies
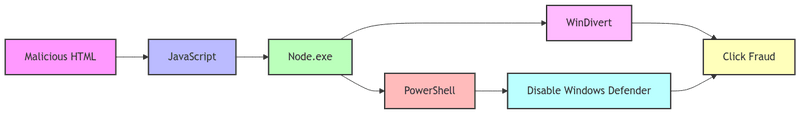
Nodersok/Divergent (2019)
This fileless malware campaign exploited several legitimate Windows tools in its attack chain:
- Exploited Node.exe, a legitimate Windows component, to run malicious JavaScript.
- Used WinDivert, a legitimate packet capture driver, for network traffic manipulation.
- Leveraged PowerShell to disable Windows Defender and other security tools.
- The entire attack chain operated in memory, leaving minimal traces on the disk.
Emotet (2018-2021)
While Emotet has a file-based component, its infection and propagation methods heavily rely on fileless techniques:
- Initial infection often occurs through malicious macros in Office documents.
- Uses PowerShell scripts to download and execute payloads directly in memory.
- Leverages Windows Management Instrumentation (WMI) for lateral movement within networks.
- Exploits the legitimate Windows component regsvr32.exe to run malicious DLLs without registration.
HiddenWasp (2019)
This Linux-based fileless malware demonstrates that fileless techniques aren't limited to Windows:
- Exploited LD_PRELOAD, a legitimate Linux feature, to inject malicious code into processes.
- Used shared libraries to maintain persistence without writing to disk.
- Leveraged built-in Linux utilities like cron for scheduling tasks.
- Operated primarily in memory, making it difficult to detect with traditional antivirus solutions.
How to Detect a Fileless Malware?
Here's a quick breakdown of how detections methods vary between a Normal Malware & Fileless Malware
Detection Method | Normal Malware | Fileless Malware |
|---|---|---|
Signature-based Detection | Effective | Limited |
File Scanning | Primary method | Ineffective |
Behavioural Analysis | Secondary method | Primary method |
Memory Scanning | Sometimes | Critical |
Whitelisting | Effective | Limited |
Heuristics | Secondary method | Critical |
Understanding the differences in detail
- Signature-based Detection:
- Normal Malware: Highly effective. Antivirus software can identify known malware by matching file signatures against a database.
- Fileless Malware: Limited effectiveness. With no files to scan, traditional signature-based methods struggle to detect fileless threats.
- File Scanning:
- Normal Malware: This is the primary method. Antivirus software scans files on disk for malicious code.
- Fileless Malware: Ineffective. Fileless malware doesn't write to disk, leaving nothing for file scanners to detect.
- Behaviour Analysis:
- Normal Malware: Often used as a supplementary method to catch unknown variants.
- Fileless Malware: This becomes the primary method. Security solutions must monitor system behavior to detect unusual activities associated with fileless attacks.
- Memory Scanning:
- Normal Malware: Sometimes used, especially for packed or obfuscated malware.
- Fileless Malware: Critical. Since fileless malware operates in memory, scanning RAM becomes essential for detection.
- Whitelisting:
- Normal Malware: Effective in preventing unauthorized executables from running.
- Fileless Malware: Limited effectiveness. Fileless malware often abuses whitelisted system tools, bypassing this protection.
- Heuristic Analysis:
- Normal Malware: Used as a supplementary method to detect new or unknown threats.
- Fileless Malware: Critical. Advanced heuristics are needed to identify suspicious patterns in memory usage, API calls, and system behavior.
Challenges Posed to SOC Teams
Fileless malware presents a significant challenge to traditional security measures & SoC Operations. It necessitates a shift from file-centric to behavior-centric security approaches, requiring more advanced, real-time monitoring and analysis capabilities.
Key challenges are
- Speed of Evolution:
- Normal Malware: Evolves relatively slowly. Signature updates can often keep pace.
- Fileless Malware: Evolves rapidly. New techniques can quickly render existing detection methods obsolete.
- False Positives:
- Normal Malware: Lower rate of false positives with signature-based detection.
- Fileless Malware: Higher risk of false positives due to reliance on behavior analysis, which can sometimes flag legitimate activities.
- Resource Intensity:
- Normal Malware: File scanning can be resource-intensive but is typically scheduled.
- Fileless Malware: Constant behavior monitoring and memory analysis can be more resource-intensive.
- Forensic Analysis:
- Normal Malware: Leaves artifacts on disk, facilitating post-incident forensics.
- Fileless Malware: Minimal artifacts, making forensic analysis challenging.
- Prevention vs. Detection:
- Normal Malware: Prevention (blocking malicious files) is often possible.
- Fileless Malware: Focus shifts more to rapid detection and response, as prevention is more challenging.
Way Forward for Organizations
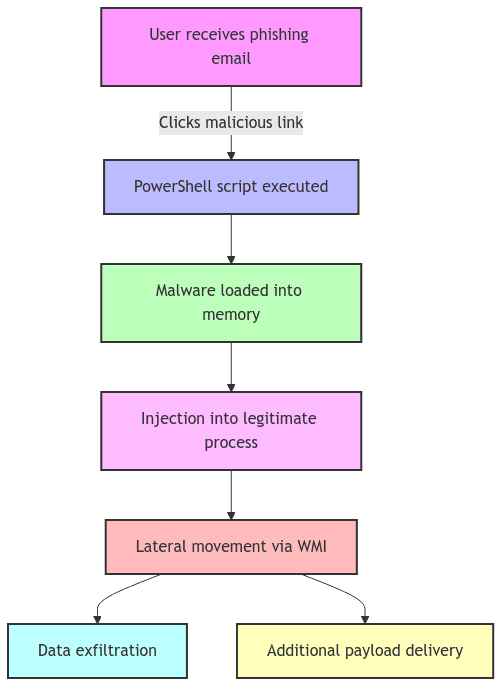
Phishing emails often serve as the initial vector for fileless attacks. Advanced email filtering, sandboxing, and user education are vital components of a comprehensive defense strategy. Traditional, file-centric security measures fall short against these sophisticated, memory-resident threats. Organizations must evolve towards behavior-based detection, advanced memory analysis, and real-time system monitoring
By moving beyond outdated signature-based methods to adopt a multi-layered, proactive approach encompassing both system and email security, organizations can better shield themselves against the elusive threat of fileless malware in today's dynamic threat landscape.


Comments
Your comment has been submitted