Government & Regulatory Impersonation: An Overlooked Threat Vector in Email Security
[Author's Note: The following narrative illustrates real cyber threats facing Indian corporations. While the specific scenarios are fictional, they represent genuine risks encountered by businesses across India.]
In the bustling heart of Mumbai's financial district, Vikram Desai's phone buzzed urgently. As the Chief Information Security Officer (CISO) of a leading IT firm, he was used to early morning alerts. But this one was different.
"Sir, Finance is about to send out our quarterly projections to what they think is SEBI," his deputy reported, voice tense.
Across town, Priya Sharma, Head of Corporate Banking at a major bank, stared at her screen. An email, seemingly from the Reserve Bank of India, warned of suspicious activities on their corporate accounts. A countdown timer urged immediate action
As Vikram and Priya grappled with these situations, they stood at the forefront of a growing threat facing Indian businesses: sophisticated cyberattacks impersonating government authorities.
Case Study: Regulatory Impersonation
These weren't isolated incidents. Across India, companies were falling victim to a new wave of cyberattacks. The perpetrators, masquerading as trusted government bodies, were exploiting the very foundations of trust in regulatory communications.
Vikram's team discovered the SEBI email was a masterful fake – perfect letterhead, flawless signatures, and an email address off by just one character. Meanwhile, Priya's instincts saved her bank from a sophisticated phishing attempt mimicking the RBI's official website.
Let's deep dive into the case
Case 1: The SEBI Disclosure Deception (2022)
The Attack
In mid-2022, a group of cybercriminals launched a meticulously planned phishing campaign impersonating SEBI, India's securities market regulator. The attackers sent official-looking emails to a wide range of listed companies, claiming to be from SEBI's disclosure department.
The Tactics
- Spoofed Email Addresses: The attackers used email addresses that closely resembled official SEBI domains, often differing by just one character.
- Official Letterheads and Signatures: Emails contained perfect replicas of SEBI letterheads and forged signatures of high-ranking SEBI officials.
- Urgent Requests: The emails claimed that immediate disclosure of sensitive financial information was required due to regulatory changes or ongoing investigations.
The Target Information
The phishing emails requested various types of sensitive data, including:
- Unreleased financial statements
- Details of upcoming mergers or acquisitions
- Information on major shareholders and their trading activities
- Confidential board meeting minutes
The Near Misses
Several high-profile companies nearly fell victim to this scam:
- A major IT firm was on the verge of sending detailed financial projections before a vigilant compliance officer spotted irregularities in the email header.
- A pharmaceutical company almost disclosed information about an upcoming drug patent, which could have had severe market implications if released.
The Resolution
SEBI became aware of the scam after receiving inquiries from suspicious companies. They quickly issued an official warning to all listed entities, detailing the fraudulent campaign and providing guidelines to verify authentic SEBI communications.
Case 2: The RBI Fraud Alert Scam (2023)
The Attack
In early 2023, a sophisticated phishing operation targeted corporate banking customers by impersonating the Reserve Bank of India (RBI), India's central banking institution.
The Tactics
- Mass Email Campaign: Thousands of corporate email accounts received alerts purportedly from RBI's fraud prevention department.
- Psychological Manipulation: The emails claimed that the recipient's corporate account had been flagged for suspicious activities, creating a sense of urgency and fear.
- Fake RBI Website: Recipients were directed to a meticulously crafted fake RBI website to "verify" their account details.
The Mechanics of the Scam
- Initial Contact: Emails warned of potential account freezes due to suspected fraudulent activities.
- Call to Action: Recipients were urged to log in to their corporate banking accounts through a provided link to verify their identity and account status.
- Data Harvesting: The fake RBI website captured login credentials, potentially giving attackers access to corporate bank accounts.
The Scope and Impact
- Over 500 companies across various sectors received these phishing emails.
- At least 30 companies reported attempting to log in through the fake website.
- Three mid-sized companies suffered significant financial losses before the scam was uncovered.
The Aftermath
- RBI issued an emergency advisory to all banks and corporate customers.
- Several banks implemented additional authentication steps for large transactions.
- The incident sparked a nationwide conversation about the need for better corporate cybersecurity training, especially regarding government communications.
Why Regulator Impersonation if Effective
Impersonation of government bodies poses a particularly significant risk & is effective, Here's why:
- Regulatory Landscape: India's complex regulatory environment, with bodies like SEBI, RBI, and various sector-specific regulators, provides ample opportunity for impersonation attempts.
- Digital India Initiative: The push for digital transformation in governance has led to increased electronic communication between government bodies and businesses, creating more opportunities for cybercriminals to exploit.
- GST-Related Scams: The implementation of the Goods and Services Tax (GST) has been exploited by scammers posing as tax authorities, targeting businesses with fraudulent notices and demands.
- Aadhaar-Linked Services: As more corporate services become linked with Aadhaar, India's biometric ID system, attackers have impersonated the Unique Identification Authority of India (UIDAI) to phish for sensitive data.
Organizations, especially those in highly regulated sectors like Banking, Financial Services, and Insurance (BFSI), frequently interact with government bodies. Regulators such as the Securities and Exchange Commission (SEC), the Financial Industry Regulatory Authority (FINRA), or industry-specific bodies regularly send notifications and directives. These communications typically command high attention and click-through rates due to their perceived importance and authority.
This creates a perfect storm for cybercriminals targeting corporate environments. By impersonating these trusted entities, attackers can exploit the natural tendency of employees to respond quickly to governmental communications, potentially bypassing usual security precautions.
The Scale of Regulatory Impersonation
15% of all Phishing attacks are now some form of government agency impersonation
The impersonation of government bodies is not a new tactic, but it's one that's gaining traction. According to a report by the Anti-Phishing Working Group (APWG), phishing attacks impersonating government agencies increased by 110% in Q2 2021 compared to the previous quarter.
This trend has continued, with government impersonation now accounting for approximately 15% of all phishing attacks & INR 15K Cr is the impact of the attacks.
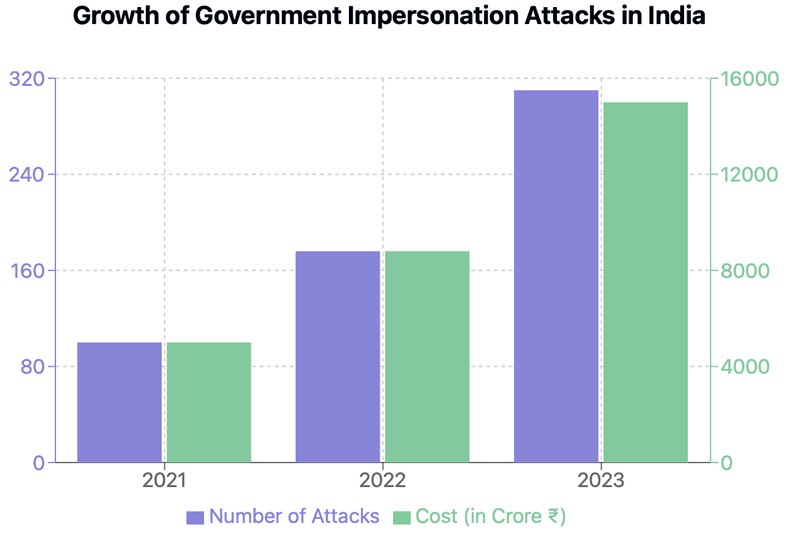
The numbers tell a stark story:
- The Indian Computer Emergency Response Team (CERT-In) reported a 61% increase in phishing attacksin 2022 & 36% in 2023 compared to the previous year, with government impersonation being a significant contributor[1]
- A report by a prominent Email Security vendor in 2022 found that 69% of organizations experienced at least one attack that impersonated a trusted entity, including government bodies.
- Another study in 2023 revealed that 35% of social engineering attacks impersonated government agencies or other trusted entities in emails targeting businesses.
- A survey by a leading Indian cybersecurity firm in 2023 found that 42% of Indian businesses reported at least one instance of a government impersonation attempt in their corporate email systems over the past year.
Impact of Regulatory Impersonation
The consequences of a successful government impersonation attack can be severe:
- Data Breaches: Attackers may trick employees into sharing sensitive information, believing they're complying with a regulatory request.
- Financial Losses: Fake fines or mandatory "security upgrades" can lead to significant financial damage.
- Malware Infiltration: Seemingly official documents may contain malware, providing a foothold in the organization's network.
- Reputational Damage: Falling for such an attack can erode trust with customers and partners.
Conclusion: Email Security Products Lack Indian Context
"Our top-tier email security system didn't flag the fake SEBI email"
As companies scrambled to defend themselves, most email security products weren't equipped to handle these India-specific threats effectively.
"Our top-tier email security system didn't flag the fake SEBI email," Vikram explained to his board. "It's great at catching generic phishing attempts, but it stumbled on this sophisticated impersonation of an Indian regulatory body."
The problem? Most email security solutions are designed with a global, one-size-fits-all approach. They lack the nuanced understanding of India's unique regulatory landscape, government communication styles, and cultural context.
Consider these challenges:
- Regulatory Complexity: India's multi-layered regulatory environment, with bodies like SEBI, RBI, IRDAI, and various sector-specific regulators, creates a complex web that global security products struggle to navigate.
- Language Nuances: Many government communications in India use a mix of English and regional languages or specific bureaucratic phrasings that international security tools might not recognize as official.
- Evolving Digital Governance: Initiatives like Digital India have changed how government bodies communicate electronically, but global security products haven't kept pace with these India-specific changes.
- Local Domain Knowledge: Attackers often use slightly misspelled government domains or obscure official-looking email addresses that generic security tools fail to flag as suspicious.
This gap in protection leaves Indian businesses vulnerable. While global threats are well-covered, the unique challenges of the Indian corporate and regulatory environment create blind spots that attackers are quick to exploit.
References
[1] CERT-In Annual Report 2022: https://www.cert-in.org.in/ [2] RBI Financial Stability Report, June 2023: https://www.rbi.org.in/Scripts/PublicationReportDetails.aspx?UrlPage=&ID=1203 [3] DSCI Cybersecurity Survey 2023: https://www.dsci.in/content/cyber-security-report [4] PwC's Global Economic Crime and Fraud Survey 2022 - India Insights: https://www.pwc.in/consulting/risk-consulting/forensic-services/global-economic-crime-and-fraud-survey.html[5] EY Global Information Security Survey 2021: https://www.ey.com/en_in/cybersecurity

Comments
Your comment has been submitted