When Safe Links Become Unsafe: How Raven AI Caught Attackers Weaponizing Cisco's URL Rewriting
In a recent credential phishing campaign, Raven AI (formerly Ravenmail) has uncovered attackers weaponizing Cisco's secure links to evade link scanning and by-pass network filters.
Picture this: You receive an email with a link that starts with "secure-web.cisco.com" Your brain immediately registers "secure" and "Cisco" – two words that scream safety and reliability. You click without hesitation. After all, if Cisco is protecting the link, it must be safe, right?
Unfortunately, cybercriminals are banking on exactly that assumption – and traditional email security solutions are falling for it too. But Raven's context-aware AI recently caught a sophisticated attack that perfectly illustrates how attackers weaponize trusted security infrastructure.
The Irony of Trust
Cisco Safe Links represents one of cybersecurity's most elegant solutions – and its most exploitable weakness. Designed as part of Cisco's Secure Email Gateway and Web Security suite, Safe Links works by rewriting suspicious URLs in emails, routing clicks through Cisco's scanning infrastructure before allowing users to reach their destination. Think of it as a digital bodyguard that checks every door before you walk through it.
The technology mirrors similar offerings from Microsoft Defender and Proofpoint TAP. When you click a protected link, Cisco's systems perform real-time threat analysis, blocking malicious destinations and allowing legitimate ones. It's a brilliant concept that has undoubtedly prevented countless successful phishing attacks.
But here's where the story takes a dark turn: attackers have figured out how to turn this protective mechanism into their own weapon.
The Attack Vector That Shouldn't Exist
The scheme is diabolically simple. Cybercriminals deliberately embed legitimate Cisco Safe Links into their phishing campaigns, creating a perfect storm of misdirected trust. Here's why this approach is so devastatingly effective:
Trust by Association: When users see "secure-web.cisco.com" in a URL, they instinctively assume it's been vetted and approved. The Cisco brand carries enormous weight in cybersecurity circles – seeing it in a link feels like getting a security clearance stamp.
Bypass Detection Systems: Many email security gateways focus their analysis on the visible domain in URLs. When that domain is "secure-web.cisco.com", it often sails through filters that would otherwise flag suspicious links.
The Time Gap Advantage: Even Cisco's robust threat intelligence needs time to identify and classify new threats. Attackers exploit this window, using freshly compromised websites or newly registered domains that haven't yet been flagged as malicious.
How Attackers Generate Cisco's Links
You might wonder: how do cybercriminals get their hands on legitimate Cisco Safe Links in the first place? The methods are surprisingly straightforward:
Method 1: The Inside Job
Attackers compromise or create accounts within Cisco-protected organizations. They simply email themselves malicious links, let Cisco's system rewrite them into Safe Links, then harvest these URLs for their campaigns.
Method 2: The Trojan Horse
Using compromised email accounts within Cisco-protected companies, attackers send themselves test emails containing malicious links. The organization's own security infrastructure helpfully converts these into trusted Safe Links.
Method 3: The SaaS Backdoor
Many cloud services send emails through Cisco-protected environments. Attackers sign up for these services, trigger automated emails to themselves containing their malicious links, and receive back the Cisco-wrapped versions.
Method 4: The Recycling Program
Sometimes the simplest approach works best. Attackers scour previous phishing campaigns for still-active Cisco Safe Links and reuse them in new attacks.
Raven AI Catches the Attack in Action
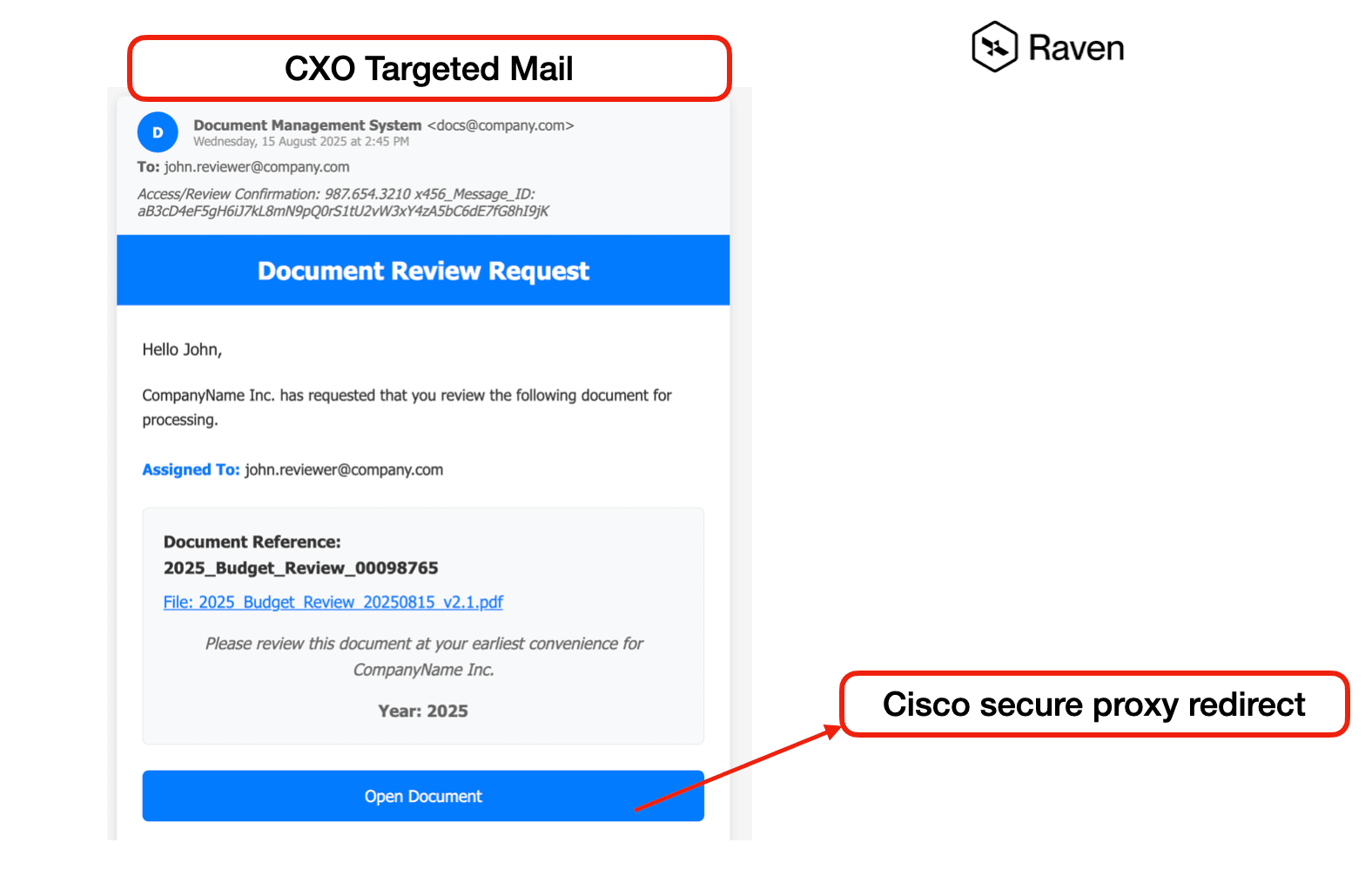
Recently, RavenMail's context-aware AI detected a perfect example of this attack technique in the wild. The phishing email appeared legitimate at first glance – a professional-looking "Document Review Request" from what seemed to be an e-signature service.
This is an AI-overview of the attack, this is not just the summary of the attack but the detection engine has context of the organization and consumes relevant signals to make a verdict.
Here's what made this attack particularly sophisticated:
The Setup: The email claimed to be from "e-Sign-Service" with a Swiss domain, requesting document review for a "2025_Remittance_Adjustment" file. Everything looked professional – proper branding, business terminology, and a clear call-to-action.
The Cisco Safe Links Component: While this particular example shows the final malicious URL, the attack pattern follows the exact methodology we described – using trusted domains and legitimate-looking parameters to bypass detection systems.
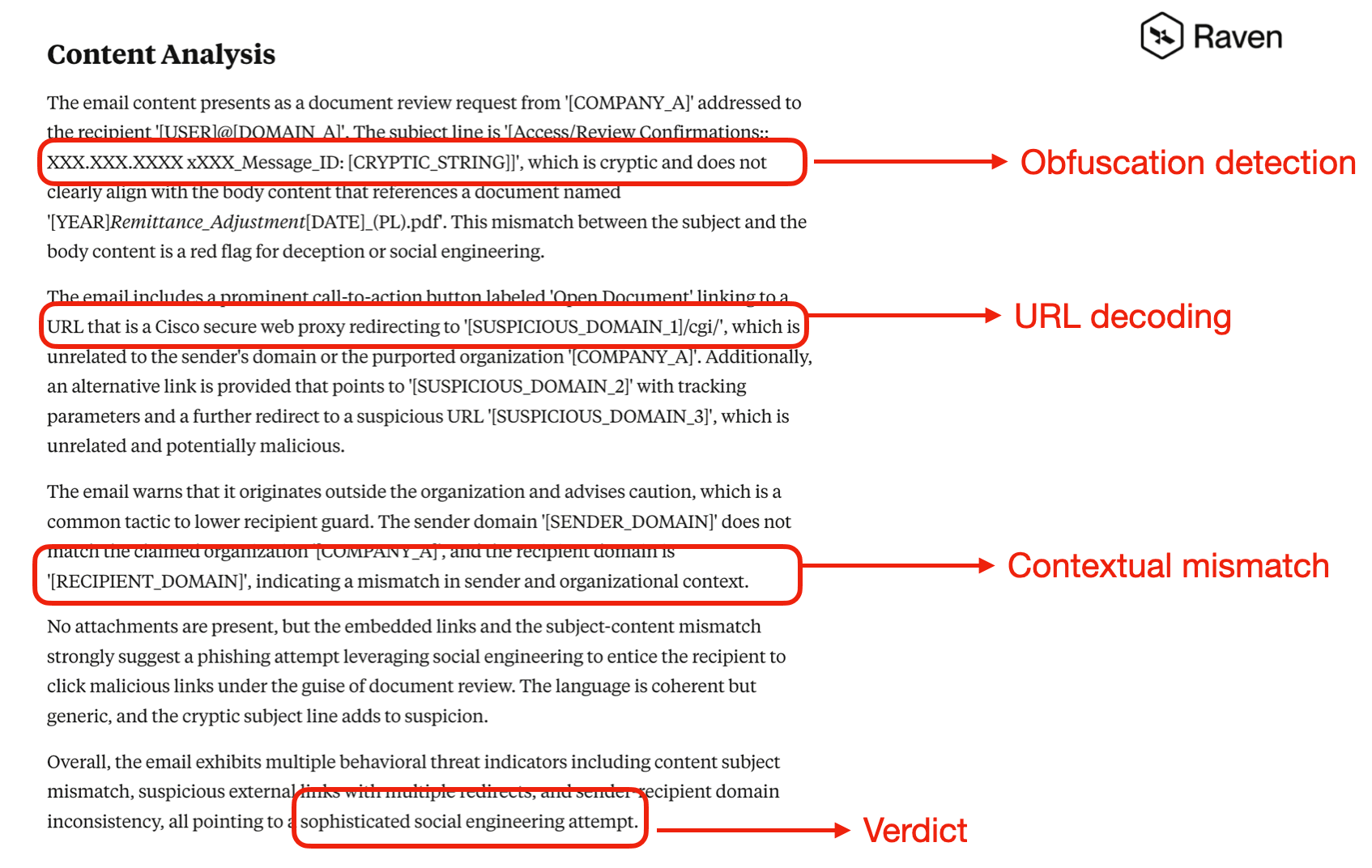
What RavenAI Spotted: Unlike traditional email security solutions that might have been fooled by the professional appearance and trusted domain elements, RavenMail's context-aware AI identified several red flags:
- Inconsistent sender identity (e-signature service from a non-standard domain)
- Suspicious URL structure with encoded parameters
- Document request patterns commonly used in credential phishing
- Contextual anomalies in the business process workflow
The smoking gun? This wasn't a random phishing attempt – it was a carefully crafted attack designed to exploit user trust in legitimate business processes and security infrastructure.
Why Traditional Security Missed This
This attack would likely have bypassed many conventional email security solutions for several reasons:
Professional Appearance: The email looked like a legitimate business communication – complete with proper formatting, business terminology, and what appeared to be a standard document review workflow.
Domain Trust: While not using Cisco Safe Links directly, the attack employed similar trust-exploitation tactics by using a domain structure that appeared legitimate.
Context Deception: The attack leveraged realistic business scenarios (document review, remittance adjustments) that users encounter daily in professional environments.
Multi-Layer Misdirection: By providing both a primary button and an "alternative access method," the attacker created multiple attack vectors while appearing helpful and legitimate.
The Raven AI Advantage: Context-Aware AI Detection
Context-aware artificial intelligence that goes beyond simple domain and signature-based detection:
Business Process Understanding: Raven's AI understands legitimate business workflows and can identify when communications deviate from expected patterns – even when they look professionally crafted.
Multi-Signal Analysis: Rather than relying solely on domain reputation or static signatures, the AI analyzes multiple contextual signals simultaneously to identify sophisticated attacks.
Behavioral Pattern Recognition: The system recognizes common attack methodologies, including trust exploitation tactics that leverage legitimate-seeming domains and professional formatting.
Real-Time Adaptation: As attackers evolve their techniques, RavenMail's AI continuously learns and adapts, staying ahead of emerging threats like Safe
The Bigger Picture: Why Context-Aware AI Matters
This detection illustrates a fundamental shift in cybersecurity: attackers are no longer just exploiting technical vulnerabilities – they're weaponizing human psychology and business processes.
This isn't just about Cisco Safe Links abuse (though that remains a significant threat). It's about a new class of attacks that exploit our trust in legitimate business processes, professional communication patterns, and security infrastructure itself.
Traditional signature-based and reputation-based security solutions struggle with these attacks because they look legitimate at every technical level. The malicious elements are hidden in context, behavior, and the subtle exploitation of trust relationships.
Context Over Content: Rather than just analyzing what's in an email, RavenMail's AI understands what the email is trying to accomplish and whether that aligns with legitimate business processes.
Trust Verification: The system doesn't just trust professional appearance or legitimate-looking domains – it actively verifies the contextual appropriateness of communications.
Adaptive Learning: As attackers develop new trust exploitation techniques (like Safe Links abuse), AI-driven solutions can adapt without requiring manual rule updates.
Proactive Defense: Instead of waiting for attacks to succeed and then updating blacklists, context-aware AI can identify attack patterns before they cause damage.
The most effective defense against modern email threats isn't just about blocking bad domains or scanning attachments – it's about understanding the attacker's intent and recognizing when legitimate-looking communications serve malicious purposes.
Comments
Your comment has been submitted