Phishing using Salesforce: How Raven AI detected attacks from compromised Salesforce Tenants
2025 marked an unprecedented surge in Salesforce-related phishing attacks to deliver sophisticated phishing attacks impersonating Meta Business Portal and fake Salesforce account suspensions, which bypassed traditional email security because they originated from legitimate Salesforce servers and passed all authentication checks (SPF, DKIM, DMARC). While conventional solutions like Microsoft 365 failed to detect these attacks due to their reliance on sender reputation, Raven's AI-powered detection succeeded by analyzing the context and mismatch between sender infrastructure and email content, catching brand impersonation and social engineering patterns that others missed—demonstrating that modern email security must go beyond authentication protocols to understand content-sender relationships in an era where trusted platforms are increasingly weaponized against their own users.
The 2025 Salesforce Email Attack Wave: A New Paradigm
The Scale of the Problem
- Phishing attacks leveraging Salesforce increased 109% year-over-year
- Over 12,000 Meta-branded phishing emails were sent globally using Salesforce's infrastructure
- Multiple sophisticated campaigns exploited different Salesforce features, from Marketing Cloud to basic email infrastructure
Attack Pattern 1: The Meta Business Portal Masquerade
Between August 2025, attackers leveraged legitimate Salesforce Marketing Cloud infrastructure to deliver convincing emails impersonating Meta's Business Messaging Partner Portal.
Example Email Characteristics:
- From: Kevin W. (spoofed display name)
- Subject: "Verify Your BM Partner Portal Profile to Maintain Full Access"
- Content: Professional-looking email with Meta branding claiming account issues
- Infrastructure: Sent via Salesforce's legitimate email servers
The email shown in the first image demonstrates the sophistication of this attack:
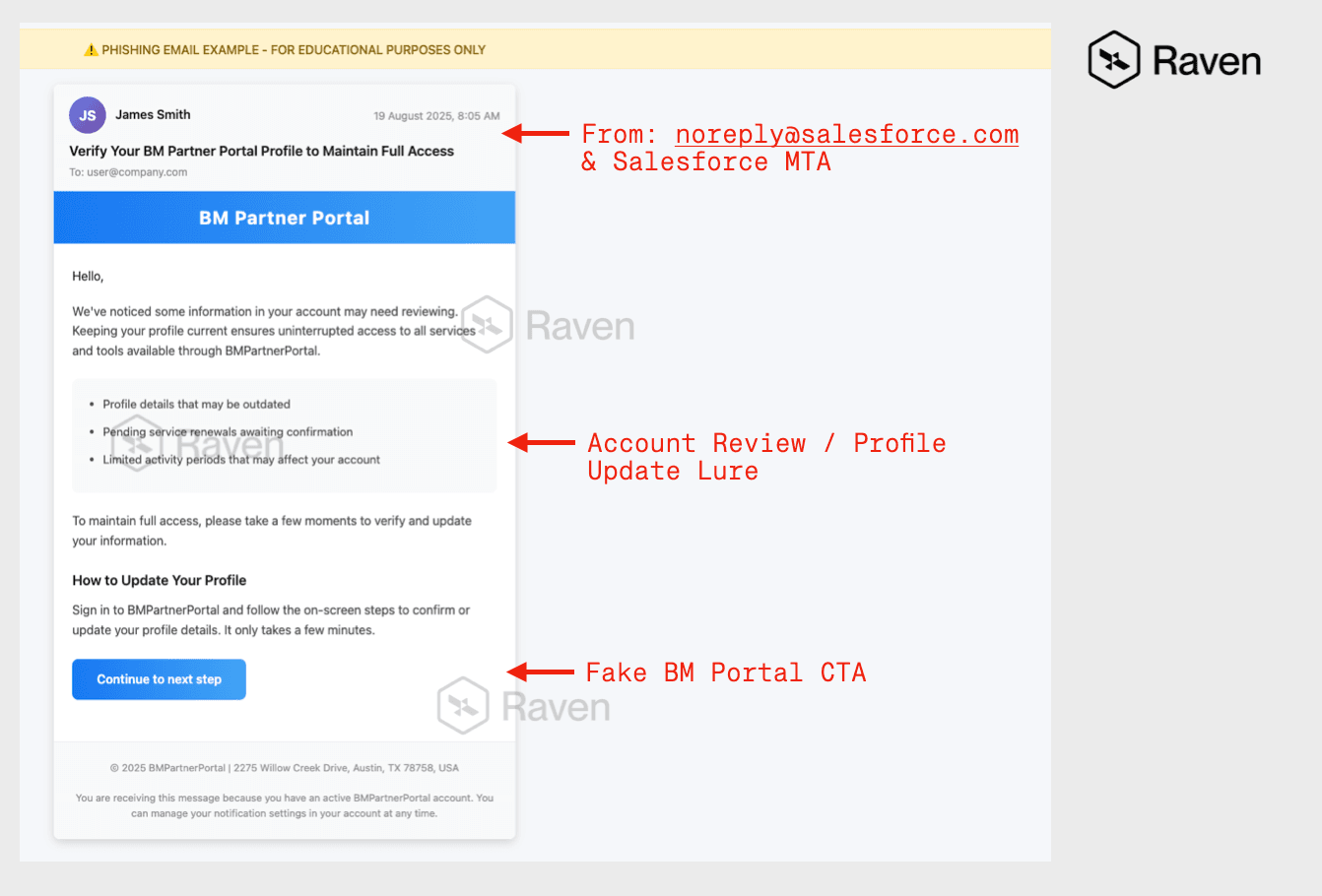
Attack Mechanics:
- Sender Infrastructure: Legitimate Salesforce servers ([email protected]) with full SPF/DKIM/DMARC authentication
- Delivery Method: Emails passed all standard security checks because they originated from genuine Salesforce Marketing Cloud
- Payload: Shortened link (cli[.]re/3nqrzq) redirecting to newly registered phishing domain (bmportalpartner[.]com)
- Target Deception: Fake Meta Partner Portal login page designed to harvest credentials
Evasion Techniques:
- Trust Exploitation: Abused Salesforce's legitimate email infrastructure to bypass reputation filters
- URL Obfuscation: Used Capsulink shortener to hide the final malicious destination
- Cloudflare Hosting: Masked true hosting origin behind Cloudflare's CDN
- Impersonated Landing Page: Crafted a well designed landing page that looks like BM Portal and asks for user credentials
Technical Indicators (IoCs)
Domains & URLs:
cli[.]re/3nqrzq (Capsulink shortener – malicious)
bmportalpartner[.]com (primary phishing domain)
Example phishing URL format: https://bmportalpartner[.]com/login
Domain WHOIS (bmportalpartner[.]com):
Registrar: Cosmotown, Inc.
Registered: 2025-08-14
Name Servers: cory.ns.cloudflare[.]com, margaret.ns.cloudflare[.]com
IP's: Hidden behind Cloudflare (true IP obfuscated)
Type: Credential Phishing via Supply Chain Abuse
Initial Access: Legitimate Salesforce infra (compromised tenant)
Targeted Brand: Meta Business Messaging Partner Portal
Target Audience: Businesses using Meta Business Messaging APIs/WhatsApp integrations (likely Salesforce CRM clients)
Threats Tactics & Procedures (TTPs)
Compromise of legitimate SaaS account (Salesforce)
URL shortening to evade detection
Cloudflare masking to hide hosting origin
Brand impersonation with high-fidelity phishing page
Attack Pattern 2: The Salesforce Account Suspension Scam
A separate campaign, detected in April 2025, showed even more sophisticated tactics targeting businesses directly with fake Salesforce account alerts.
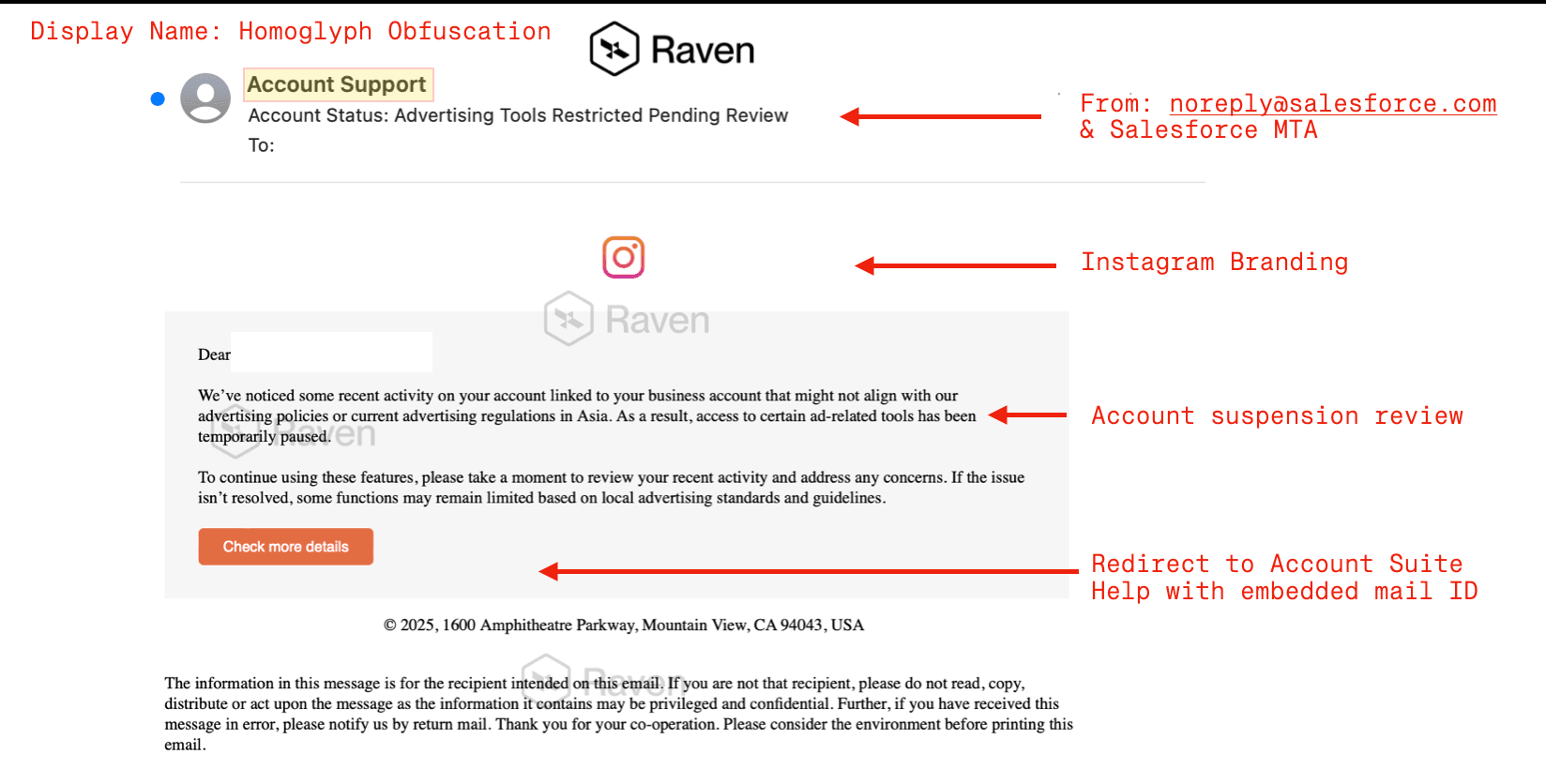
Attack Mechanics
Type: Spear Phishing (Brand Impersonation)
Theme: "Ad Tools Suspended Pending Review" — urgency and business disruption
Pretext: Suspended Salesforce features due to policy violation
Lure: CTA to review the account to restore access
Tactics, Techniques, and Procedures (TTPs) - Highly Sophisticated
Tactic | Description |
Impersonation of Trusted Brand (Salesforce) | Used the Salesforce SMTP infrastructure with SPF-pass headers to increase credibility. |
Display Name Homoglyph Obfuscation | Used UTF-8/Cyrillic characters resembling Latin letters to make the display name appear as "Salesforce Support", evading filters and misleading users. |
Missing DKIM Signature | Message was not signed using DKIM, breaking expected authenticity for Salesforce emails. |
Redirector Domain Abuse | Call-to-action linked to weavecoms.com which redirected to a phishing page at accountsuite-help.com. |
CTA URL with Fragment Data | Target's personal info (name/email) passed in URL fragment (#user_email=...) — designed to evade email/web filters. |
Cloudflare CAPTCHA as Delay Layer | Used CAPTCHA page (via Cloudflare) to delay detection and prevent automatic sandboxing by email security solutions. |
Fake Legal Footer | Footer mentions Google’s HQ address instead of Salesforce's, and lacks usual branding (e.g., unsubscribe links). |
TTP Sophistication Assessment - High
Aspect | Observed Behavior | Evaluation |
Use of Legitimate Infrastructure | Message sent via Salesforce MTA (sfdc.net) | High sophistication — bypasses traditional SPF checks and reputation systems |
Brand Impersonation | Crafted to look like Salesforce support with visual pretext | Medium sophistication — common tactic, but well executed |
Display Name Obfuscation | Unicode homoglyph spoofing to fake “Salesforce Support” | High sophistication — bypasses filters, visually deceptive |
Lack of DKIM | Missing DKIM signature despite Salesforce usually signing mail | Moderate — likely abusing a relay or non-core service |
Link Redirection via Third-Party Domain | Redirector weavecoms[.]com before phishing page | High — avoids direct linking to suspicious domains, evades URL filters |
User Data in Fragment URI | Personal info (name/email) passed in #fragment | High — this avoids web proxies and Secure Email Gateways that don’t parse JS |
Cloudflare CAPTCHA Gate | Human verification challenge to slow analysis | Advanced — helps evade automated sandbox detonation and adds credibility |
No Attachments or Malware | Entirely web-based, no traditional malware | Stealth-oriented — avoids AV/EDR triggers |
Custom URL Personalization | #user_email=... to tailor experience | Medium to High — improves trust in phishing site |
Infrastructure Involved - Compromised Sales Force Tenant
Component | Description |
salesforce.com | Legitimate sender domain (spoofed with partial legitimacy via relay abuse). |
smtp-0e67926779f85ec45.core1.sfdc-8tgtt5.mta.salesforce.com | Salesforce MTA used — possibly via compromised tenant or abused API. |
url6484.marketing.sg.weavecoms[.]com | Obfuscated redirector used to track clicks and forward to phishing site. |
accountsuite-help[.]com | Final phishing site impersonating a secure login or account management portal. Registered recently. Uses CAPTCHA screen. |
Potential Motives for these campaigns
Motive | Likelihood | Description |
Credential Harvesting | High | Fake login/CAPTCHA page likely leads to form for capturing Salesforce or corporate credentials. |
Reconnaissance/Target Profiling | Moderate | Information in URL fragments suggests targeted user tracking (email, name). |
Brand Abuse for Financial Gain | High | Abusing Salesforce branding for trust to increase click-through and submission rates. |
Access to Business Platforms | Moderate | May be targeting individuals with admin roles or advertising privileges in CRMs. |
The OAuth Supply Chain Context
While Raven's primary detection focused on email-based attacks, these incidents occurred alongside a broader campaign of OAuth abuse and supply chain attacks:
The Salesloft Drift Breach
Between August 8-18, 2025, a threat actor tracked as UNC6395 exploited compromised OAuth tokens linked to the Salesloft Drift application to gain API access to Salesforce customer instances. This campaign impacted over 700 organizations, including Cloudflare, Google, Proofpoint, Zscaler, Palo Alto Networks, and SaaS giant Workiva.
The Human Element
These recent Salesforce breaches started with a human being tricked. Someone answered a call and made a click. Attackers used voice phishing (vishing) to:
- Impersonate IT support staff
- Convince employees to approve malicious Connected Apps
- Obtain long-lived OAuth tokens bypassing MFA
- Export data using scripts mimicking legitimate Data Loader operations
How Traditional Email Security Failed
The Trust Assumption Problem
Legacy email security operates on a fundamental assumption: trusted infrastructure sends legitimate emails. This assumption shattered in 2025 when:
- SPF/DKIM/DMARC Became Insufficient: When emails originate from legitimate Salesforce servers, authentication passes by design
- Brand Impersonation Filters Failed: Unicode homoglyph spoofing evaded traditional detection
- URL Filtering Gaps: Redirect chains through low-reputation domains weren't flagged initially
- Context Blindness: Traditional filters couldn't understand the mismatch between Salesforce infrastructure and Meta content
How Raven AI Detected and Stopped These Email Attacks
1. Context-Aware Brand Analysis
While traditional solutions relied on sender reputation, Raven's AI understood the context mismatch:
- Cross-Brand Detection: Recognized when Salesforce infrastructure was sending non-Salesforce branded content
- Semantic Analysis: Identified Meta Business Portal references in emails from Salesforce servers
- Trust Verification: Validated whether the claimed sender matched the actual business relationship
2. Advanced Linguistic and Visual Analysis
Raven's LLM-powered detection caught what static rules missed:
- Homoglyph Detection: Identified Unicode character substitution in display names
- Urgency Pattern Recognition: Flagged social engineering language patterns
- Content-Infrastructure Mismatch: Detected when email content didn't align with sending infrastructure
3. Deep URL and Redirect Analysis
Unlike surface-level URL scanning, Raven performed:
- Chain Following: Mapped complete redirect sequences from legitimate shorteners to malicious endpoints
- Domain Intelligence: Flagged newly registered domains
- Behavioral Analysis: Detected evasion techniques like CAPTCHA gates and fragment parameters
Conclusion: Email Security in the Age of Trusted Infrastructure Abuse
The 2025 Salesforce email attacks represent a fundamental shift in the threat landscape. When trusted infrastructure becomes the attack vector, traditional email security approaches based on sender reputation and authentication are insufficient.
Raven AI's success in detecting these email-based attacks demonstrates the critical importance of:
- Context-aware analysis that goes beyond infrastructure trust
- AI-powered detection that understands content-sender relationships
- Real-time adaptation to evolving social engineering tactics
- Cross-brand intelligence that detects infrastructure abuse
As SaaS platforms become increasingly central to business operations, the abuse of trusted infrastructure for phishing attacks will only grow. The question isn't whether this will happen again—it's whether your email security solutions are sophisticated enough to detect it when it does
Comments
Your comment has been submitted