Appsheet Trademark Violation Phishing Scam - Sept 2025 Update
How the AppSheet phishing campaign exposes the fundamental flaws in traditional email security
Understanding AppSheet: Google's No-Code Platform
Before diving into the security implications, it's important to understand what AppSheet is and why it carries such inherent trust with organizations worldwide.
AppSheet is Google's no-code application development platform that allows users to build mobile and web applications directly from data sources like Google Sheets, Excel files, or cloud databases. Acquired by Google in 2020, AppSheet has become a core component of Google Workspace, enabling millions of users to create business applications without writing code.
Why AppSheet Matters in Enterprise Security
Enterprise Integration: AppSheet is deeply integrated with Google Workspace, making it a trusted service for organizations already using Gmail, Google Drive, and other Google services.
Automated Communications: The platform regularly sends automated emails for:
- Application notifications and updates
- Data sync confirmations
- User access requests
- System status alerts
- Workflow notifications
Google's Security Halo: As a Google Cloud service, AppSheet inherits the trust and reputation that organizations place in Google's infrastructure. When employees see "appsheet.com" in their inbox, they naturally associate it with the same security standards they expect from Gmail or Google Drive.
Widespread Adoption: With millions of business users building applications on the platform, AppSheet communications are common in corporate environments, making malicious emails appear routine.
This combination of factors—enterprise integration, automated messaging, inherited trust, and widespread adoption—makes AppSheet communications particularly effective for attackers looking to abuse legitimate service infrastructure.
The Phishing Campaign
A recent phishing campaign targeting Google Workspace Centric organizations through AppSheet-branded emails perfectly illustrates how traditional security controls become useless when attackers abuse legitimate infrastructure. This isn't a story about sophisticated evasion techniques or zero-day exploits. It's about how legitimate services can be weaponized to deliver malicious content that sails past every security filter you've deployed.
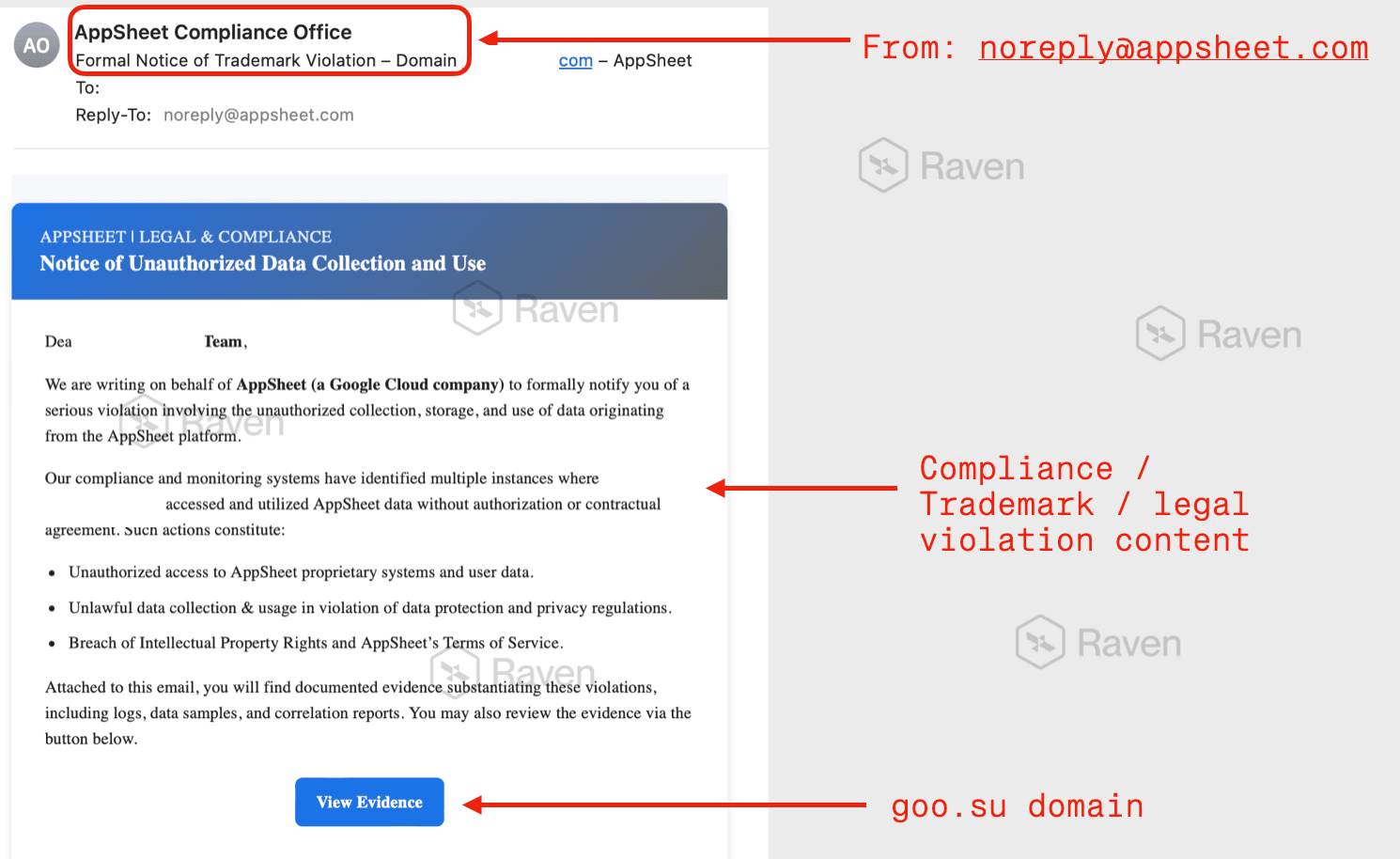
Mechanics of the Attack
What Made This Campaign Invisible to Security Filters
The attackers leveraged AppSheet's legitimate email functionality to send messages that were, from a technical perspective, completely authentic:
Sender: [email protected] (legitimate)
Infrastructure: Google mail servers (trusted)
Authentication: SPF/DKIM/DMARC passing (verified)
Reputation: appsheet.com (excellent)
Content: Professional formatting (convincing)
CTA URL: Look-alike Google URL shortener
Possible Scenarios of Abuse
This AppSheet campaign represents a broader trend of legitimate service abuse. Attackers are discovering they can achieve better results by using trusted platforms rather than building their own infrastructure:
Method 1: Account Compromise
- Compromise legitimate user accounts on trusted platforms
- Use established reputation and authentication
- Insert malicious content into otherwise legitimate message templates
Method 2: Feature Abuse
- Create legitimate accounts on trusted services
- Abuse notification systems, form builders, or automated messaging
- Craft messages that appear to come from the service itself
Method 3: Template Injection
- Inject malicious links into legitimate templates or forms
- Leverage the platform's email infrastructure for delivery
- Exploit user-generated content features
Similar Earlier Attacks
Since March 2025, cybersecurity researchers have documented a massive surge in phishing attacks exploiting Google's AppSheet platform, with the campaign reaching its peak on April 20th when 10.88% of all global phishing emails were sent from AppSheet—98.23% impersonating Meta and 1.77% targeting PayPal. These attacks used the identical bypass strategy as the current trademark violation campaign, originating from [email protected] to bypass Microsoft and Secure Email Gateways (SEGs) that rely on domain reputation and authentication checks (SPF, DKIM, DMARC).
The Meta campaign introduced advanced evasion techniques including polymorphic identifiers using AppSheet's unique ID generation functionality, ensuring every message was slightly different to bypass traditional detection systems, while utilizing man-in-the-middle proxy mechanisms and hosting phishing sites on reputable platforms like Vercel. This earlier campaign establishes AppSheet platform abuse as a proven, scalable attack vector, with the current trademark violation campaign representing an evolution of these tactics—demonstrating that AppSheet has become a preferred platform for sophisticated phishing operations because it provides authenticated, trusted delivery infrastructure that consistently bypasses traditional email security controls.
How Raven AI Caught The Attack
While traditional email security filters saw only green authentication checkmarks and trusted sender reputation, Raven's AI-powered context-aware detection engine identified the subtle inconsistencies that revealed this as a sophisticated attack. Raven's analysis went beyond surface-level authentication, this nuanced, context-driven analysis understanding not just who sent the email but whether the content makes sense for that sender enabled Raven to detect a campaign that bypassed every traditional security control.
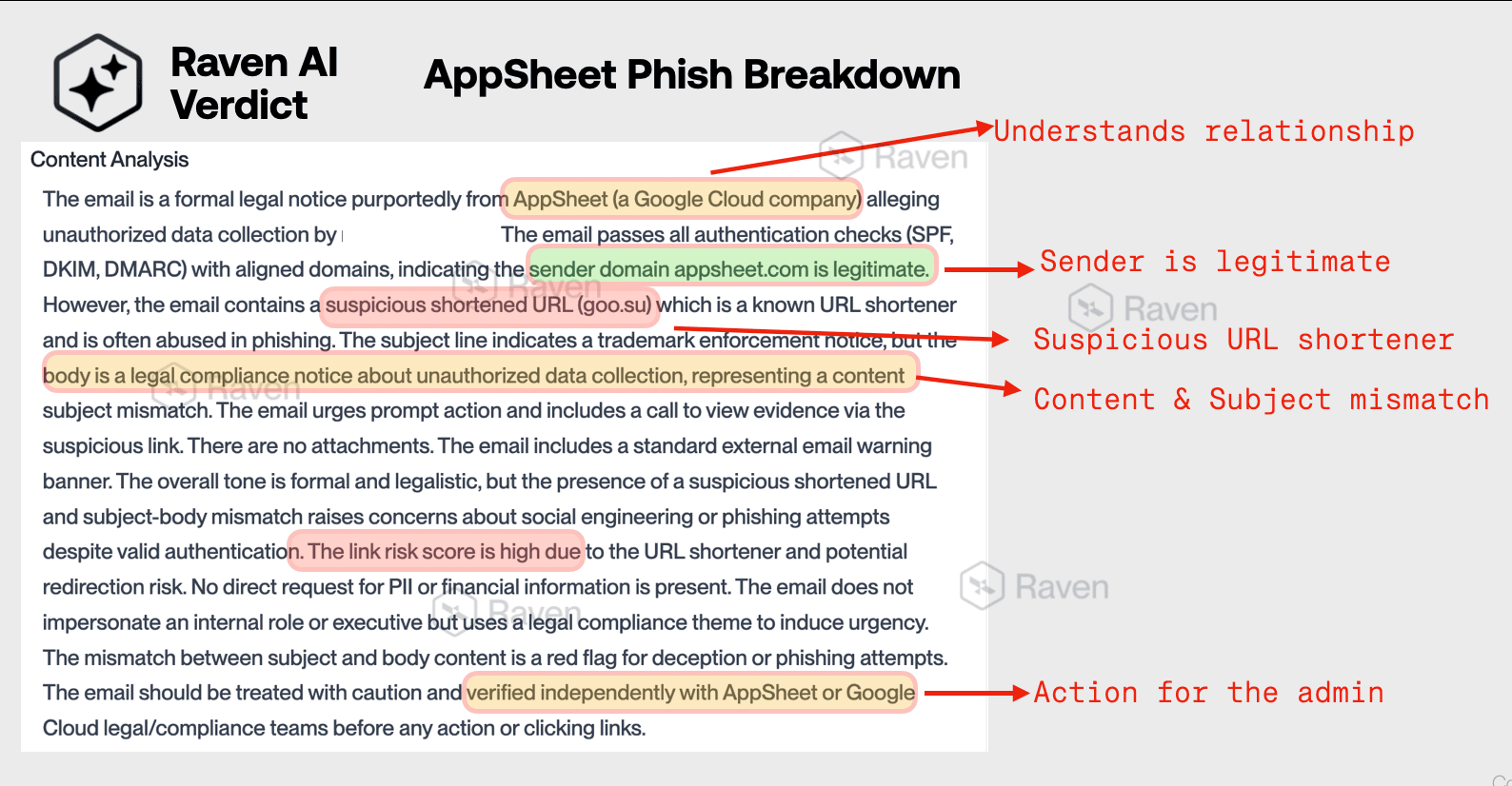
Key Detection Indicators from Raven's Analysis
These detection points demonstrate how Raven's context-aware engine analyzes relationships, content appropriateness, and behavioral patterns rather than just technical authentication - catching sophisticated attacks that traditional filters completely miss.
- Understands Relationship: Raven recognizes that AppSheet is "a Google Cloud company" and understands the service's legitimate business functions vs. the inappropriate legal threat content
- Sender is Legitimate: Authentication checks (SPF, DKIM, DMARC) all pass with aligned domains, confirming appsheet[.]com is a genuine sender - yet the email is still flagged as suspicious
- Suspicious URL Shortener: Identifies goo[.]su as a known URL shortener frequently abused in phishing campaigns, inconsistent with legitimate AppSheet communications
- Content & Subject Mismatch: Detects the disconnect between the "trademark enforcement notice" subject line and the actual "unauthorized data collection" legal compliance content in the body
- Action for the Admin: Provides clear, actionable guidance to "verify independently with AppSheet or Google Cloud legal/compliance teams before any action or clicking links
Conclusion: Rethinking Email Security
The AppSheet phishing campaign isn't just another phishing attempt—it's a fundamental challenge to how we think about email security. When attackers can abuse the same legitimate services that our organizations depend on, traditional security models break down.
The solution isn't to stop trusting legitimate services—it's to develop smarter, context-aware trust. We need security systems that don't just ask "Is this sender legitimate?" but also "Does this message make sense coming from this sender?"
As attackers continue to abuse legitimate infrastructure, security teams must evolve beyond authentication-based defenses toward behavioral and contextual analysis. The alternative is a future where every legitimate service becomes a potential attack vector—and traditional email security becomes obsolete.
The question isn't whether your authentication checks are working.
The question is: what happens when the attacker doesn't need to bypass them?
Comments
Your comment has been submitted