[Nov 2025] Zero-Day Tax Evasion Phishing Attack Targeting Indian Companies
In November 2025, Raven AI (formerly Ravenmail) identified and blocked a zero-day phishing campaign impersonating the Income Tax Department of India. The attacks used bilingual notices, government-themed PDFs, and highly convincing templates to create urgency around alleged tax irregularities.
The campaign delivered a two-stage malware chain consisting of a shellcode based RAT loader packaged in a ZIP file and a rogue remote administration executable disguised as a GoToResolve updater. Both payloads were confirmed as malicious.
Traditional Secure Email Gateway defenses failed to detect these messages because the sender authenticated correctly, the attachments were password protected, and the content imitated real government communication. Raven’s context-aware threat engine was able to detect the anomaly based on intent, behavioral signals, content semantics, and metadata analysis.
This blog explains how the attack was engineered, what the malware does, why Indian enterprises were specifically at risk, and how Raven neutralized the threat.
The Attack Deep Dive: How the Phishing Emails Were Structured
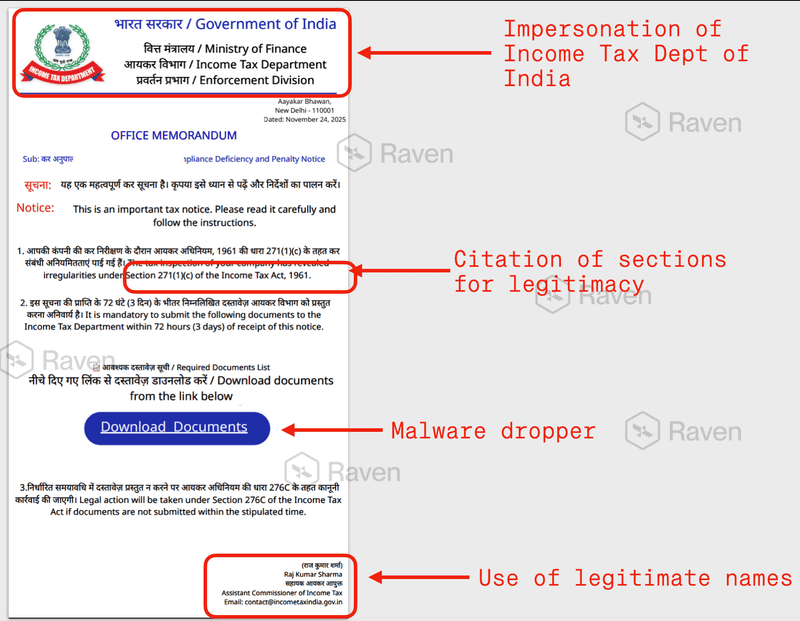
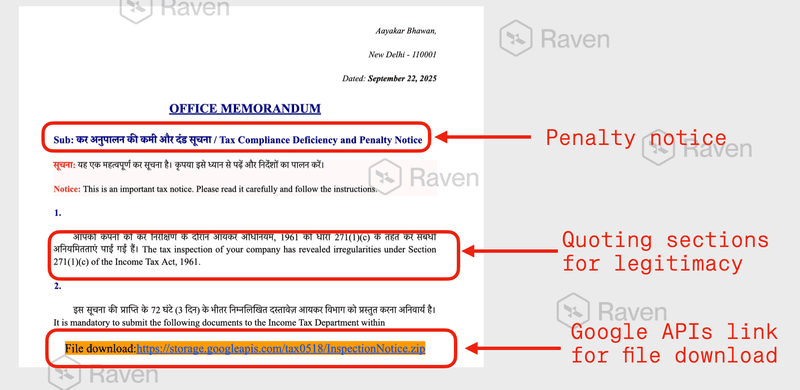
The emails claimed to be an official Tax Compliance Deficiency and Penalty Notice. The structure of the message included:
Government style formatting in both Hindi and English
Legal references such as Section 271(1)(c) and Section 276C of the Income Tax Act, 1961
A 72 hour deadline to provide documents
A download button for a ZIP file or a Google Docs link
A separate password to open the attached PDF or ZIP file
The notice format was nearly identical to real government communication, including fonts, seals, and document formatting. This authenticity influenced users to trust and open the attachments without scrutiny.
Phishing Email #1 - Re: Your company is engaged in tax evasion. Please refer to the attachment for violations
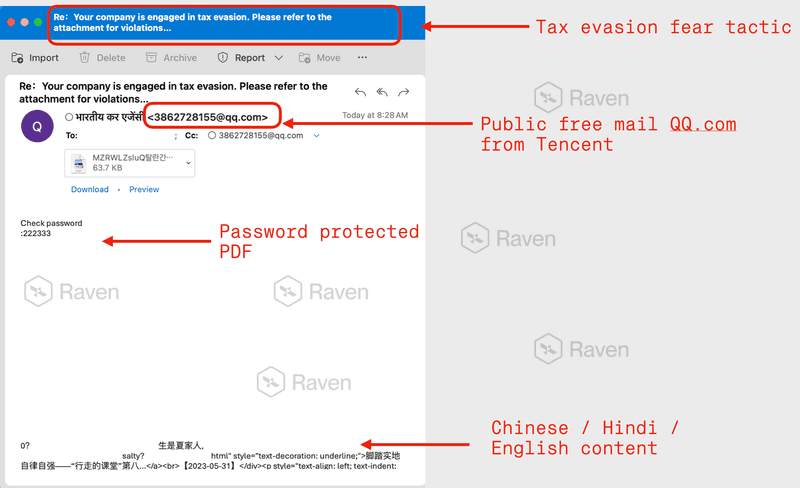
Contents of the password protected PDF file
URL trace (Disclaimer: do not access these directly)
CTA URL: https://taxwisegrupo.cc/download[.]php
Redirect URL: https://f005.backblazeb2[.]com/file/Malaysiaok/2[.]vbs
The second redirect installs and EXE file which is a Remote Access Back door
Fake GoToResolve Updater EXE: Remote Access Backdoor
VirusTotal reference: 4b97e3b17b0f6b10131c26eafa79616585f6bd283f2031e7d8faaea1e9b899b0.pdf
The payload was a 23.34 MB executable named GoToResolveUnattendedUpdater[.]exe
Key findings:
Classified as Hacktool.LogMeIn or RemoteAdmin.Win32
Uses the identity of GoToResolve, a legitimate RMM product
Loads RstrtMgr.dll, a DLL used by ransomware families (Conti, Cactus) to kill locking processes
Exhibits remote control, screen sharing, file transfer and full RMM capability
DNS and TLS activity related to gotoresolve dot com infrastructure
This indicates that attackers planned a remote interactive session after the initial RAT foothold was established. Misused legitimate remote administration tools remain one of the hardest threats to detect because they resemble actual IT operations.
Phishing Email #2 - Your tax audit report
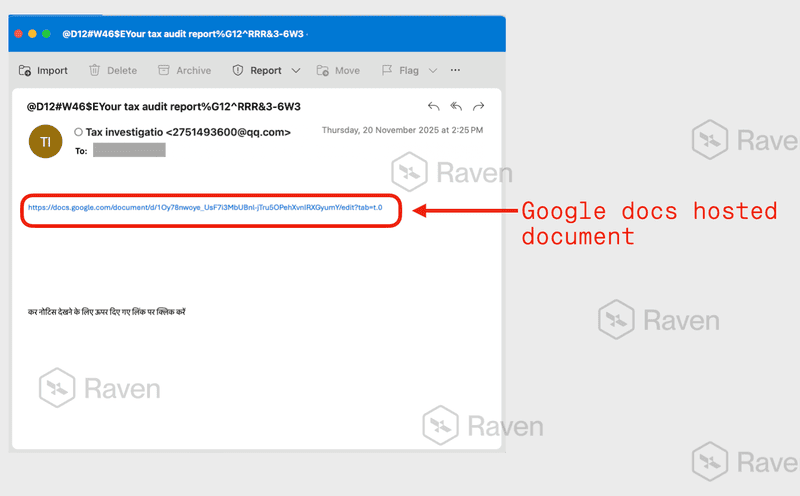
Google Docs hosted document
The redirect URL leads to download of Malicious Shellcode loaders
Malicious ZIP File: Shellcode Loader and AsyncRAT Infrastructure
VirusTotal reference: c03ecde797da2d6aee70f1a5434d9696d4766355d4deab33f32d8bec6e4d0643.pdf)
The file named Needed+Documents.zip was a 10.48 MB archive containing a multi-stage loader.
Key findings:
Classified as Trojan.Shellcode and Fragtor
Detection of .NET CLR DLL loading via scripting applications
Regsvr32 execution from unusual locations
Unsigned DLL loading via trusted Windows utilities
Network indicators linked to AsyncRAT and ResolverRAT C2 fingerprints
JA3 SSL fingerprints that match known RAT families
The ZIP contained shellcode designed to execute through regsvr32 proxy loading, a common method for fileless execution that avoids static signature detection.
This stage establishes persistence, credential harvesting, and remote command execution capabilities inside the victim environment.
How the Attack Bypassed Traditional Email Security
The campaign was engineered specifically to evade perimeter defenses. The attack used several modern evasion techniques:
Clean Sender Authentication
The emails originated from real QQ.com accounts. SPF, DKIM, and DMARC all passed successfully.
Password Protected Attachments
Password protected PDFs and ZIP files prevented antivirus engines from scanning the content. This is a common tactic for concealing malware.
Legitimate Cloud Hosting
Some variants used Google Docs for second stage delivery. Since the base domain is trusted, URL filtering is ineffective.
Bilingual Government Identity Abuse
The layout, legal references, and Hindi language content increased credibility. Legacy filters do not evaluate semantic inconsistencies or impersonation context.
AI Generated Padding
The email body contained Unicode filler text and random spacing to evade Bayesian filters. These patterns match automated phishing kits documented in earlier threat analyses.
Why Indian Enterprises Were Targeted
Indian companies are frequent targets of authority themed phishing campaigns because:
Tax communication often happens through digital channels
Compliance deadlines create psychological urgency
Many SMEs rely only on native email filtering
Government impersonation has high trust value
Securities firms, Finance, NBFC companies routinely exchange documents with regulators
The broader industry data reflects this trend. Global intelligence sources show a steady increase in tax themed attacks and impersonation using legitimate platforms. The KnowBe4 threat report indicates a significant rise in these techniques during 2025.
How Raven Detected the Zero-Day Attack
Raven AI relies on context, intent analysis, metadata understanding, and deep semantic inspection rather than signature matching. This allowed it to detect the threat immediately.
Key detection signals included:
Regulator Impersonation and Identity Conflict
A government tax department notice sent from a free foreign mailbox is an identity mismatch that Raven’s models flag as anomalous.
Behavioral and Intent Analysis
The combination of urgency, compliance deadlines, and document submission demands is typical of authority themed phishing.
Attachment Metadata and Shellcode Indicators
Raven extracted metadata from the ZIP without opening it and identified indicators consistent with malware loaders.
No Prior Relationship Signal
There was no historical communication associated with the sender domain.
Cloud Hosted Payload Anomalies
A Google Docs link delivering a supposed tax compliance notice is inconsistent with actual government workflows.
The combination of these signals allowed Raven to stop the attack without relying on any known IOC.
Conclusion
This attack demonstrates a shift in phishing tactics affecting Indian businesses. Attackers are increasingly blending authentic looking regulatory communication with sophisticated malware chains and misused remote administration tools.
The campaign passed traditional authentication checks, used password protected payloads, and relied on legitimate cloud services. These characteristics make it invisible to traditional secure email gateways.
Raven’s context aware and intent driven approach detected the inconsistencies, behavioral indicators, and malicious attachment traits before the malware could execute.
In an environment where attackers continually adapt, organizations require detection that understands communication intent and identity context rather than relying solely on signatures or known threat patterns.
Comments
Your comment has been submitted