

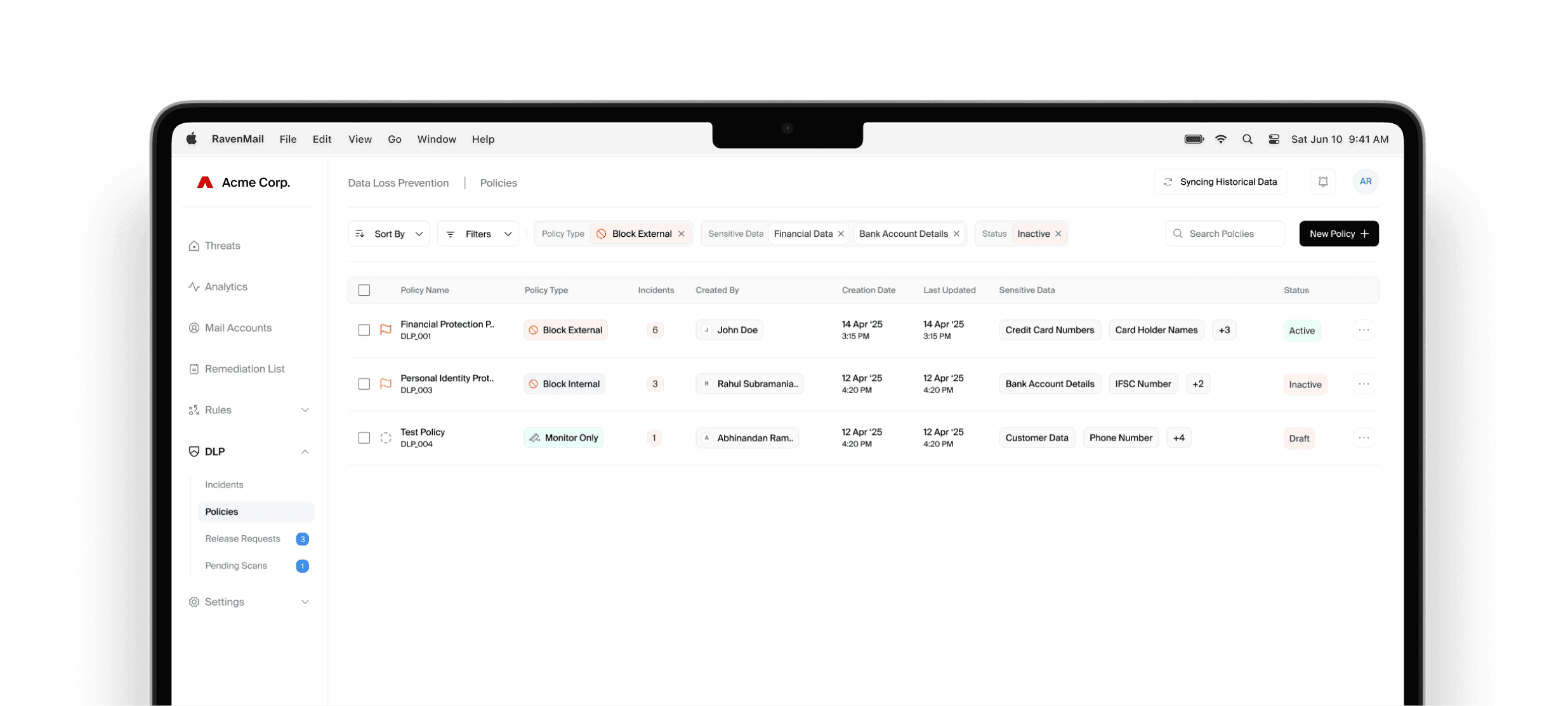
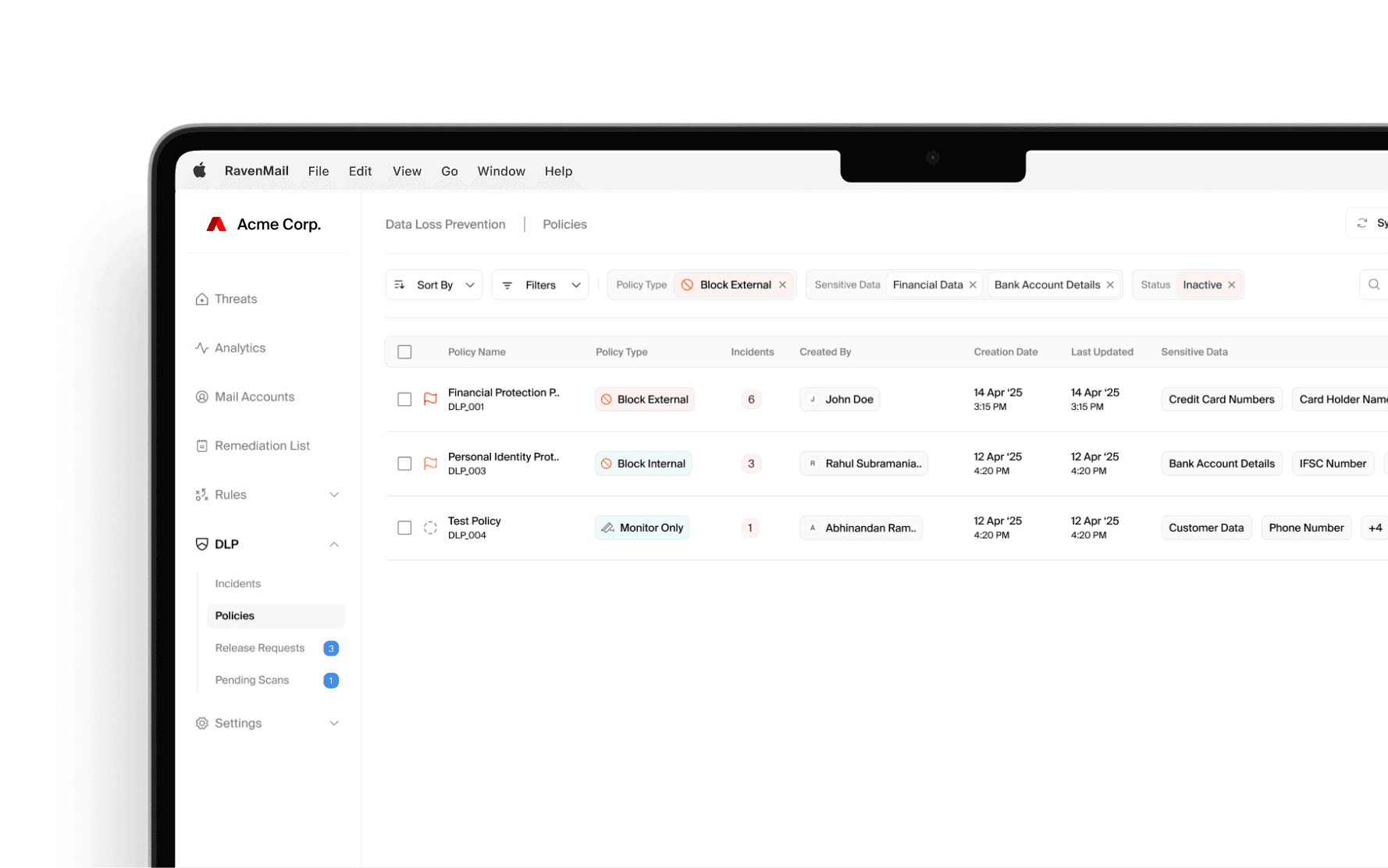
AI-Powered email DLP that is built for modern data, IP & compliance landscape
AI-Powered email DLP that is built for modern data, IP & compliance landscape
AI-Powered email DLP that is built for modern data, IP & compliance landscape
Agent-less | Regex-less
Agent-less | Regex-less
Agent-less | Regex-less
Agent-less | Regex-less

Beyond compliance with context-aware detection
Beyond compliance with context-aware detection
Beyond compliance with context-aware detection
Beyond compliance with context-aware detection
Prevent credential exposure, customer data leaks, and financial information sharing.
Prevent credential exposure, customer data leaks, and financial information sharing.
Prevent credential exposure, customer data leaks, and financial information sharing.
Prevent credential exposure, customer data leaks, and financial information sharing.
Prevent credential exposure, customer data leaks, and financial information sharing.
Infra Access Risk Detection
Infra Access Risk Detection
Infra Access Risk Detection
Identifies exposed API keys, database credentials, and authentication tokens in conversations and attachments.
Identifies exposed API keys, database credentials, and authentication tokens in conversations and attachments.
Identifies exposed API keys, database credentials, and authentication tokens in conversations and attachments.
Custom Data for Industry
Custom Data for Industry
Custom Data for Industry
Tailored protection for banking, healthcare, e-commerce and other industry-specific sensitive information.
Tailored protection for banking, healthcare, e-commerce and other industry-specific sensitive information.
Tailored protection for banking, healthcare, e-commerce and other industry-specific sensitive information.
No Regex needed
No Regex needed
No Regex needed
AI understands context and intent without manual pattern writing or complex rules.
AI understands context and intent without manual pattern writing or complex rules.
AI understands context and intent without manual pattern writing or complex rules.



Smart detection, not just pattern matching
Smart detection, not just pattern matching
Comprehensive protection across 50+ sensitive data types
Comprehensive protection across 50+ sensitive data types
Comprehensive protection across 50+ sensitive data types
Our context-aware technology understands the meaning behind text, not just patterns, allowing us to detect sensitive data even when embedded in conversational language or disguised as benign content. This provides superior protection compared to traditional regex-based solutions that fail to understand context and require constant maintenance
Our context-aware technology understands the meaning behind text, not just patterns, allowing us to detect sensitive data even when embedded in conversational language or disguised as benign content. This provides superior protection compared to traditional regex-based solutions that fail to understand context and require constant maintenance
Our context-aware technology understands the meaning behind text, not just patterns, allowing us to detect sensitive data even when embedded in conversational language or disguised as benign content. This provides superior protection compared to traditional regex-based solutions that fail to understand context and require constant maintenance
Our context-aware technology understands the meaning behind text, not just patterns, allowing us to detect sensitive data even when embedded in conversational language or disguised as benign content. This provides superior protection compared to traditional regex-based solutions that fail to understand context and require constant maintenance
Customer PII
Source Code
Legal Documents
Phone Number
API Keys
Credit Card Number
Credit Card Number
Authentication Tokens
Medical Records
Aadhaar Number
CVV
Customer PII
Customer PII
Legal Documents
Source Code
Phone Number
API Keys
Credit Card Number
Authentication Tokens
Social Security Number
Aadhaar Number
Medical Records
CVV
Customer PII
Bank Account Details
Customer PII
Legal Documents
Source Code
Phone Number
API Keys
Credit Card Number
Authentication Tokens
Social Security Number
Aadhaar Number
Medical Records
CVV
Customer PII
Bank Account Details
Customer PII
Source Code
Legal Documents
Phone Number
API Keys
Credit Card Number
Credit Card Number
Authentication Tokens
Medical Records
Aadhaar Number
CVV
Customer PII
Customer PII
Legal Documents
Source Code
Phone Number
API Keys
Credit Card Number
Authentication Tokens
Social Security Number
Aadhaar Number
Medical Records
CVV
Customer PII
Bank Account Details
Customer PII
Legal Documents
Source Code
Phone Number
API Keys
Credit Card Number
Authentication Tokens
Social Security Number
Aadhaar Number
Medical Records
CVV
Customer PII
Bank Account Details
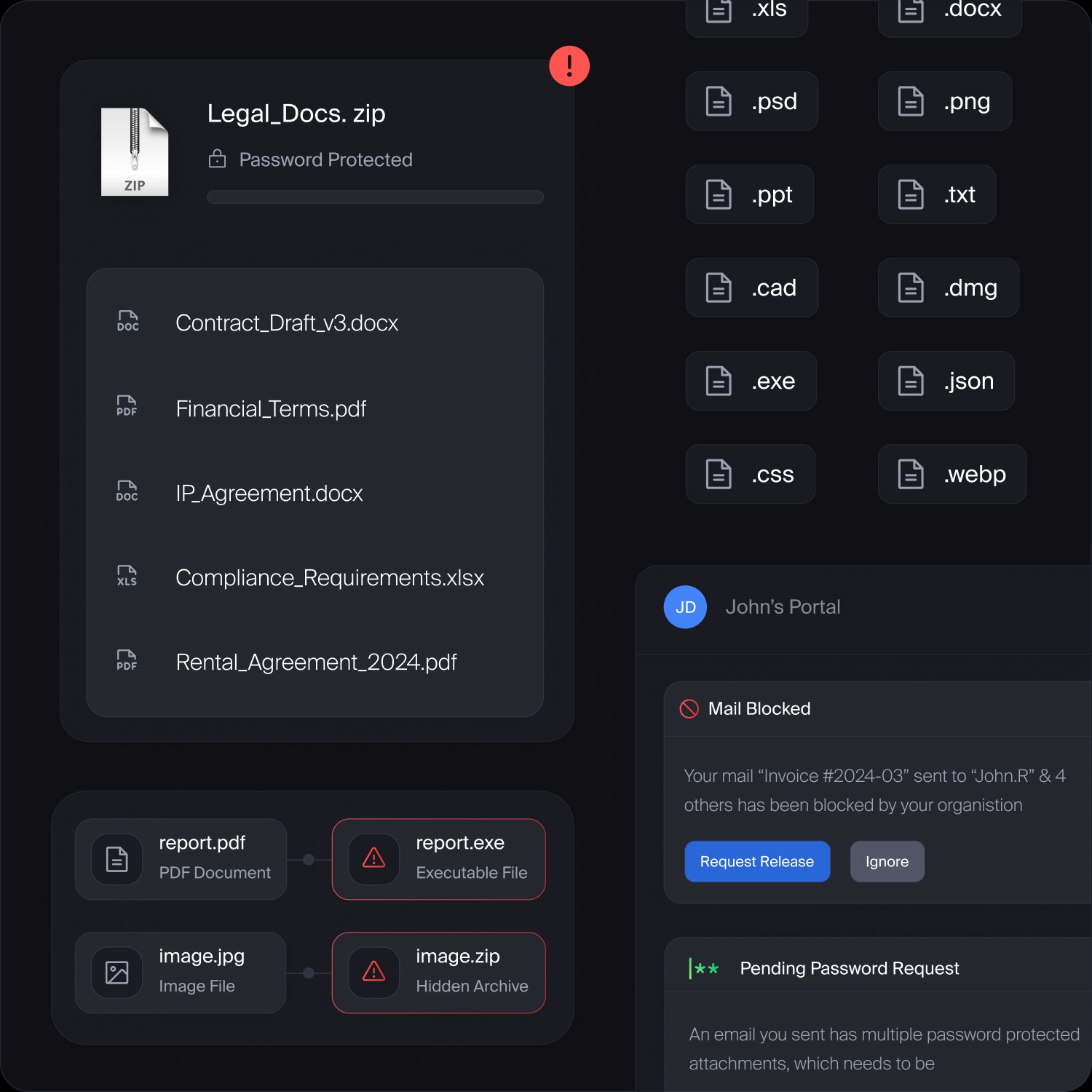
Detect where end-point DLP doesn’t see
Detect where end-point DLP doesn’t see
Detect where end-point DLP doesn’t see
Detect where end-point DLP doesn’t see
Detect data across email content, images and password-protected files
Detect data across email content, images and password-protected files
Detect data across email content, images and password-protected files
Detect data across email content, images and password-protected files
Detect data across email content, images and password-protected files
Block file types
Block file types
Block file types
Detects sensitive data in password-protected archives and masked files that traditional scanners miss due to encryption.
Detects sensitive data in password-protected archives and masked files that traditional scanners miss due to encryption.
Detects sensitive data in password-protected archives and masked files that traditional scanners miss due to encryption.
True file type detection
True file type detection
True file type detection
Reveals actual file types regardless of disguised extensions, stopping threats like .dmg, .exe, .zip attempts.
Reveals actual file types regardless of disguised extensions, stopping threats like .dmg, .exe, .zip attempts.
Reveals actual file types regardless of disguised extensions, stopping threats like .dmg, .exe, .zip attempts.
Secure User Portal
Secure User Portal
Secure User Portal
Allows users to view blocked emails, request releases, and submit passwords with minimal IT involvement.
Allows users to view blocked emails, request releases, and submit passwords with minimal IT involvement.
Allows users to view blocked emails, request releases, and submit passwords with minimal IT involvement.


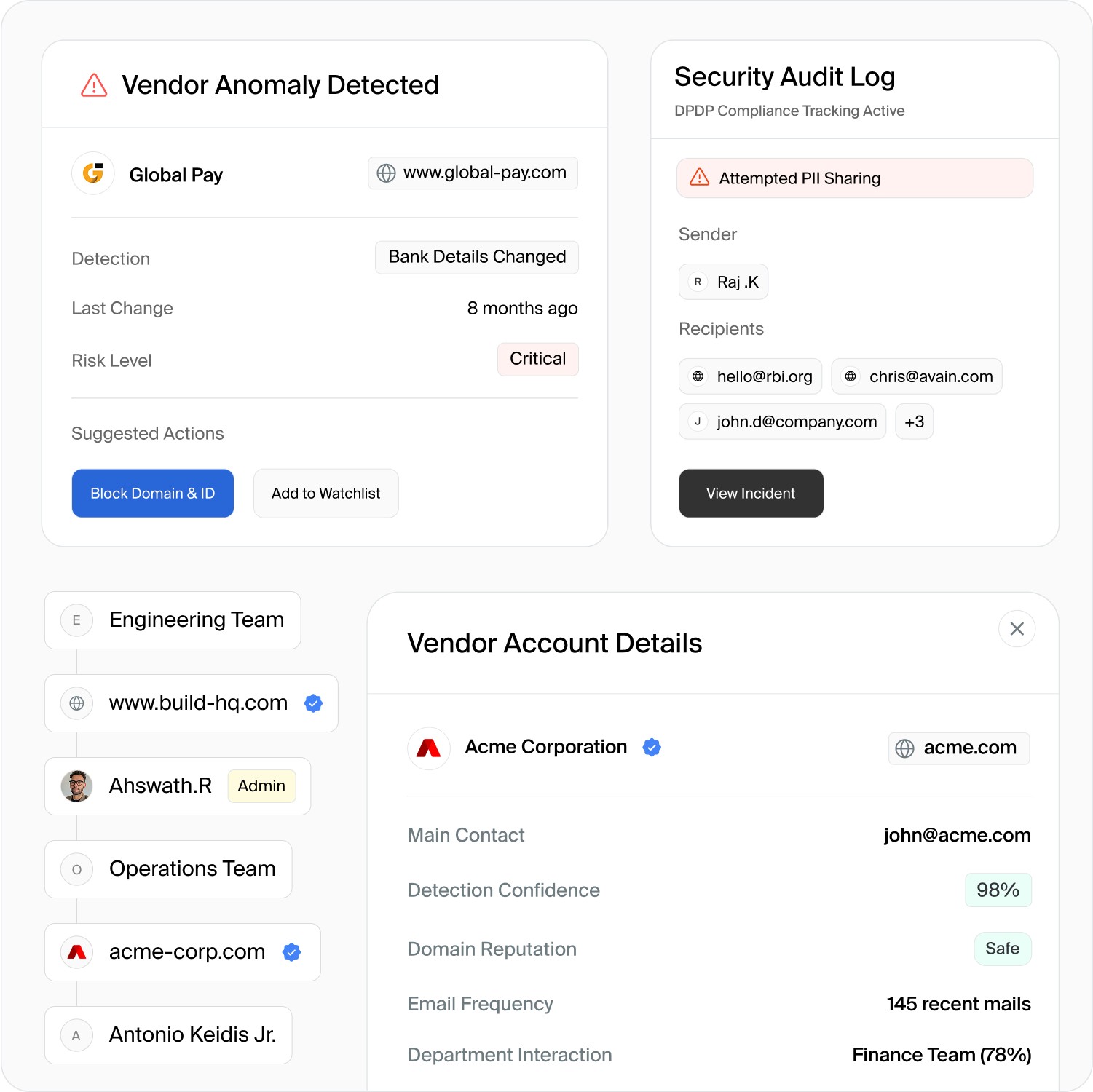
Built for communication flow
Built for communication flow
Built for communication flow
Built for communication flow
Setup & manage communications flow across confidential internal groups or trusted external partners
Setup & manage communications flow across confidential internal groups or trusted external partners
Setup & manage communications flow across confidential internal groups or trusted external partners
Setup & manage communications flow across confidential internal groups or trusted external partners
Setup & manage communications flow across confidential internal groups or trusted external partners
Internal Closed User Groups
Internal Closed User Groups
Internal Closed User Groups
Create secure communication boundaries for teams handling sensitive data, preventing accidental exposure outside approved groups.
Create secure communication boundaries for teams handling sensitive data, preventing accidental exposure outside approved groups.
Create secure communication boundaries for teams handling sensitive data, preventing accidental exposure outside approved groups.
Partner Domains & Internal Touchpoints
Partner Domains & Internal Touchpoints
Partner Domains & Internal Touchpoints
Establish trusted connections with external vendors while maintaining control over what information can be shared beyond your organization.
Establish trusted connections with external vendors while maintaining control over what information can be shared beyond your organization.
Establish trusted connections with external vendors while maintaining control over what information can be shared beyond your organization.
Block Compromised Vendors
Block Compromised Vendors
Block Compromised Vendors
Automatically detect and block communications with vendors showing suspicious behavior or signs of account compromise.
Automatically detect and block communications with vendors showing suspicious behavior or signs of account compromise.
Automatically detect and block communications with vendors showing suspicious behavior or signs of account compromise.


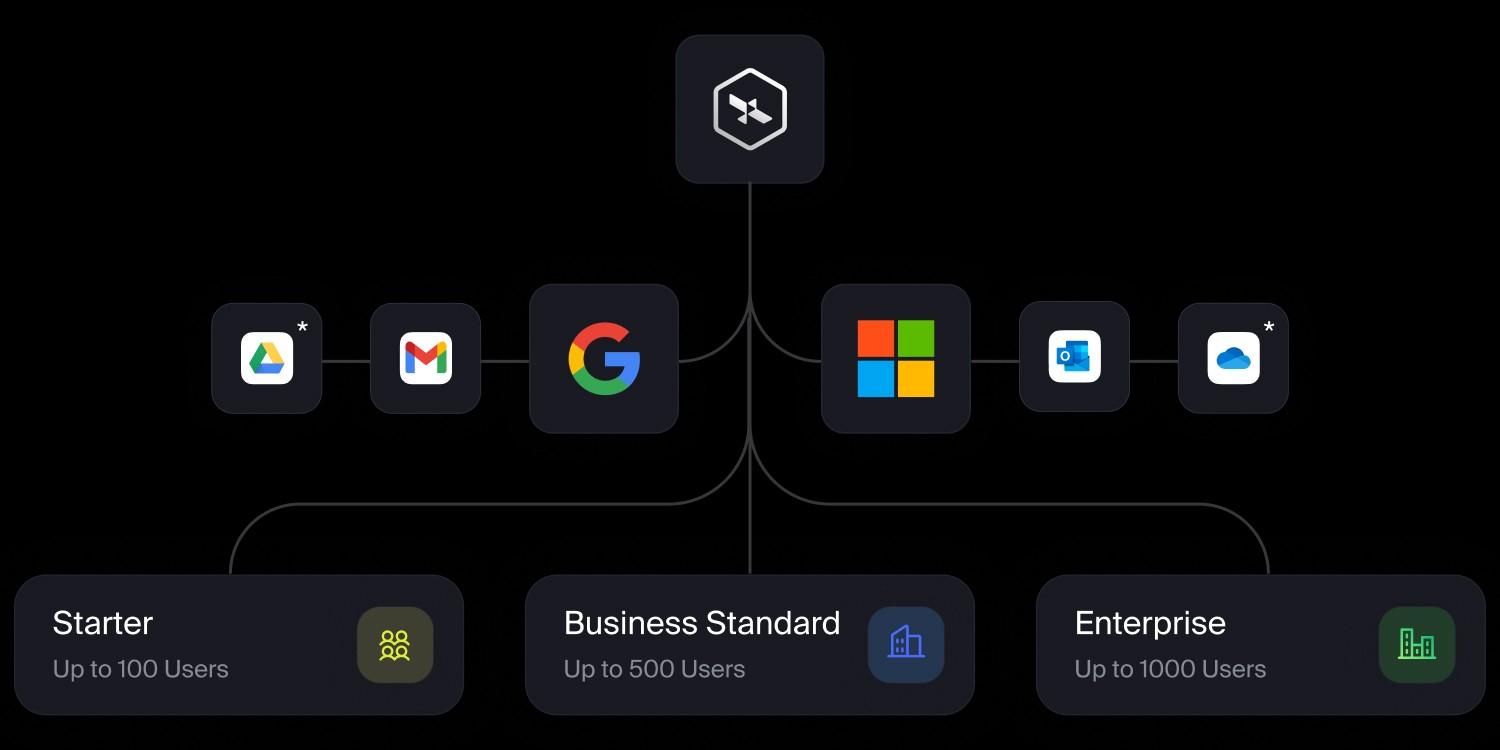
Optimise Spends
Optimise Spends
Optimise Spends
Unified Data Security across license tiers of Google and Microsoft
Unified Data Security across license tiers of Google and Microsoft
Unified Data Security across license tiers of Google and Microsoft
Unified Data Security across license tiers of Google and Microsoft
Unified Data Security across license tiers of Google and Microsoft





Modern DLP for a Modern Email Stack
Modern DLP for a Modern Email Stack
Stop building regex. Start protecting data.
Stop building regex. Start protecting data.
Schedule a demo
Schedule a demo
Raven
AI Native Context-aware email security for M365 & Google Workspace
commnova Technologies Pvt. Ltd., 12, Murugappa Rd, Chitra Nagar, Kotturpuram, Chennai, Tamil Nadu, 600085
© Commnova Technologies Pvt. Ltd. 2026
Raven
AI Native Context-aware email security for M365 & Google Workspace
commnova Technologies Pvt. Ltd., 12, Murugappa Rd, Chitra Nagar, Kotturpuram, Chennai, Tamil Nadu, 600085
© Commnova Technologies Pvt. Ltd. 2026
Raven
AI Native Context-aware email security for M365 & Google Workspace
commnova Technologies Pvt. Ltd., 12, Murugappa Rd, Chitra Nagar, Kotturpuram, Chennai, Tamil Nadu, 600085
© Commnova Technologies Pvt. Ltd. 2026
Raven
AI Native Context-aware email security for M365 & Google Workspace
commnova Technologies Pvt. Ltd., 12, Murugappa Rd, Chitra Nagar, Kotturpuram, Chennai, Tamil Nadu, 600085
© Commnova Technologies Pvt. Ltd. 2026
Raven
AI Native Context-aware email security for M365 & Google Workspace
commnova Technologies Pvt. Ltd., 12, Murugappa Rd, Chitra Nagar, Kotturpuram, Chennai, Tamil Nadu, 600085
© Commnova Technologies Pvt. Ltd. 2026


