Attack Demo #3: Github Abuse - Delivering Malware Using Trusted Platforms
[Disclaimer: This blog is part of our Attack Demo series where our Red Team members demonstrate emerging tactics used by attackers. This content is for educational purposes only]
Recap of Attack Demo Series
Demo #1: Scanning Inbox without logging in
Demo #2: How attackers establish connection using a single email
Emerging Trend of Abusing Trusted Platforms
Attackers are increasingly turning to trusted platforms to distribute malicious content. File hosting services and code repositories, particularly GitHub, have become prime targets for these nefarious activities. Their widespread use, inherent trust among users, and integration into development workflows make them attractive vectors for cyber attacks.
From hosting malware-laden documents to leveraging GitHub Actions for crypto-mining, bad actors are exploiting these platforms in diverse and sophisticated ways.
In this blog we demonstrate how attackers can deliver malware payload containers using GitHub hosted documents and also understand the attack chains using case studies.
34% of all phishing downloads originated from cloud storage apps & GitHub has 100,000 repositories containing malicious code or being used for malicious purposes.
Document-Based Attack Examples Using GitHub
1. Malicious Word Documents in GitHub Repositories
Attack Vector: Compromised Word documents hosted on GitHub
Description: In several instances, attackers have used GitHub to host malicious Microsoft Word documents containing embedded macros.
Details:
- Attackers create or compromise GitHub repositories to host seemingly legitimate Word documents.
- These documents contain malicious macros that execute when opened.
- The macros often download additional payloads or execute malicious code directly.
- Attackers use GitHub's reputation to bypass security filters and appear more legitimate.
Example Scenario: An attacker creates a repository named "Company-HR-Templates" containing Word documents. One document, "Employee_Onboarding_Form.docx", contains a macro that, when enabled, downloads malware from a separate server.
2. Phishing Campaigns Using GitHub Pages
Attack Vector: Phishing pages hosted on GitHub Pages
Description: Attackers have leveraged GitHub Pages to host phishing sites, often mimicking login pages for popular services.
Details:
- GitHub Pages allows hosting static websites directly from GitHub repositories.
- Attackers create repositories with HTML/CSS that closely mimics legitimate login pages.
- These pages are then distributed via phishing emails or other means.
- When victims enter their credentials, the data is sent to the attacker.
Example Scenario: An attacker creates a repository named "secure-login-portal" with HTML/CSS files mimicking a Microsoft 365 login page. They use GitHub Pages to host this at a URL like https://attacker-username.github.io/secure-login-portal/.
3. Malicious PDF Documents for Drive-By Downloads
Attack Vector: PDF documents hosted on GitHub with embedded malicious JavaScript
Description: Attackers have used GitHub to host PDF documents containing malicious JavaScript that executes when the PDF is opened.
Details:
- PDF documents are uploaded to GitHub repositories.
- These PDFs contain JavaScript that exploits vulnerabilities in PDF readers.
- When opened, the malicious code may attempt to download additional malware or exploit system vulnerabilities.
Example Scenario: A repository named "Free-Ebooks" hosts various PDF files. One file, "NetworkSecurity_Basics.pdf", contains JavaScript that attempts to exploit a vulnerability in older versions of Adobe Reader.
4. Steganography in Image Files
Attack Vector: Image files with hidden malicious payloads
Description: Attackers have used steganography techniques to hide malicious code within image files hosted on GitHub.
Details:
- Seemingly harmless image files (e.g., PNG, JPG) are uploaded to GitHub repositories.
- These images contain hidden malicious payloads or scripts embedded within them.
- A separate script or application is used to extract and execute the hidden content.
Example Scenario: A repository called "Wallpapers-HD" contains various high-quality images. One image, "sunset_beach.png", has a malicious script embedded in it that can be extracted and executed by a separate dropper program.
5. Malicious Markdown Files
Attack Vector: Markdown files with embedded HTML and JavaScript
Description: Attackers have exploited GitHub's rendering of Markdown files to execute malicious scripts.
Details:
- Markdown files (.md) in GitHub repositories can contain HTML and JavaScript.
- When viewed on GitHub, these scripts can potentially execute in the user's browser.
- While GitHub has measures to prevent this, attackers have found ways to bypass these protections.
Example Scenario: A repository named "Coding-Tutorials" contains various Markdown files. One file, "JavaScript_Best_Practices.md", includes obfuscated HTML and JavaScript that attempts to exploit browser vulnerabilities or perform phishing attacks when rendered.
Demo of Document Based Attack Delivered Using Email
Demo Deep Dive
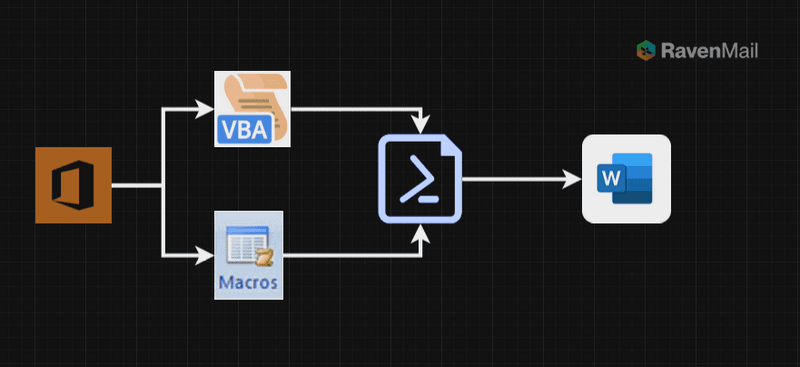
Step 1: Document Creation
- Using office to craft a malicious word doc.
- Leveraging use of VBScript and macros will will call the powershell payload from a remote location
- All the above will be used to craft the payload to create a complete malicious word Doc.
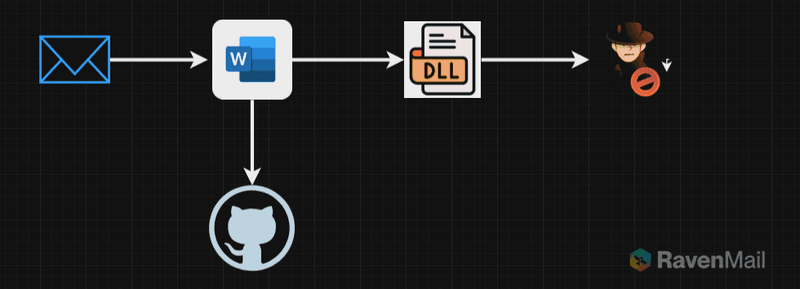
Step 2: Hosting in GitHub
Next is to host the attachment in a local server or any other hosting services. Here we are using Github to host our payload. By this we can bypass many active scanning tools that will be scanning the attachments that comes as an email.
Step 3: Direct download link & C2 Connection
Next step is to use hyper link, once the link is clicked the attachment is directly downloaded instead of taking the user to file. This way we can achieve the goal easy. Once the attachment is downloaded to the victims PC and the file is opened, the malware is executed which makes a connection to the attacker. Which can be observed in the below video and diagram.
Step 5: Initial Compromise - The Email Hook
The attacker sends a well-crafted phishing email that appears to come from a trusted source. The email often contains an attached Word document or a link leading to the document stored on Github.
The message could be urgent, asking you to review the document immediately or claiming it's related to an ongoing project. This creates a sense of urgency, compelling you to act without thoroughly inspecting the email.
Step 6: Direct download & Opening the Document
Once you open the Word document, it may prompt you to "Enable Content" or "Enable Macros." These macros are small pieces of code embedded in the document that are typically used for legitimate purposes, such as automating repetitive tasks.
However, in this case, the macro is malicious. Enabling the macro allows the attacker's code to execute on your system, often without you realizing it.
Step 7: Payload Delivery
By enabling the macro, you allow the attacker to run a variety of malicious actions on your system. Common outcomes include the installation of malware, such as keyloggers (to capture your keystrokes) or remote access Trojans (RATs) that allow the attacker to control your system remotely.
These attacks often target your email credentials, stealing your login information and sending it back to the attacker. Once the attacker gains access to your email account, they can proceed with the next phase of the attack.
Conclusion
In conclusion, the use of reputable file hosting services and platforms like GitHub for delivering malicious content presents a significant challenge for current email security systems. These attacks exploit the inherent trust placed in well-known platforms, often bypassing traditional security measures. Several factors contribute to the difficulty in detection:
- Legitimate domains: Emails containing links to GitHub or popular file hosting services are less likely to be flagged as suspicious.
- Dynamic content: Attackers can rapidly modify hosted content, making it challenging for security systems to keep up with evolving threats.
- Encrypted connections: HTTPS connections to these platforms can obscure the nature of downloaded content from security scanners.
- Delayed execution: Malicious actions are often triggered after the initial download, evading point-of-entry detection.
- Blended attacks: Combining legitimate files with hidden malicious elements confuses traditional signature-based detection methods.
To combat these sophisticated threats, email security solutions must evolve. This includes implementing more advanced behavioral analysis, improving real-time threat intelligence sharing, and enhancing sandboxing techniques to detect malicious content hosted on trusted platforms. Additionally, user education remains crucial in recognizing and avoiding these increasingly subtle attack vectors. As attackers continue to innovate, the cybersecurity community must remain vigilant and adaptive in its approach to email and content security.

Comments
Your comment has been submitted