✨ AI Model Launch: Context-Aware Sender Impersonation Detection
About RavenMail Security
For people who are not familiar about us, we are an 8-old month startup solving for 3 things in email security
- Context-awareness in Threat Detection (think of it like Blue LLMs)
- Adaptive Responsive System using AI (combination of rule generation + Reinforcement using Red LLMs)
- Proactive & in-the-moment control on Human Behaviour (Making Email Client's smarter with respect to security)
We are building out of India for the world, we were finalists in Accel CyberSecurity Summit CISO Round & got featured in Bessemer Venture Partners SaaS & Cyber report 2024.
......And we brew our own Coffee and launched our own brand - Raven Coffee.
This month we are rolling out our first publicly available Beta of our AI-Model for Impersonation Detection for Microsoft Cloud Email Platform or M365 . Before we get to the details, let's understand the broad changes to the threat landscape and why we decided to launch this first.
The Era of AI-Powered Phishing is Already Here
It's not just AI-generated content & jail broken GPTs that's a problem - there are 20 different use-cases where AI is used to enhance attacks. There are already tell-tale signs of the impact of the new AI-era Phishing is there.
- The average time to launch a campaign from 21 hours to just 15 minutes - a 97% reduction.
- AI-driven phishing campaigns can generate and send up to 10,000 personalized emails per hour, compared to the previous average of 200 emails per day using manual methods.
- AI-enhanced phishing emails have a 40% higher click-through rate compared to traditional phishing attempts, due to improved personalization and timing.
- AI-powered phishing campaigns can now adapt to new security measures within 30 minutes of deployment, compared to the previous average of 48 hours.
- AI-driven phishing kits can perform A/B testing on hundreds of email variations in under an hour, a process that previously took days or weeks.
- AI-powered security systems have reduced the average time to detect a phishing campaign from 24 hours to 30 minutes.
A major corporation (name withheld) suffered a data breach after an employee fell victim to a highly sophisticated spear-phishing attack. Forensic analysis suggested the attack leveraged a jailbroken language model to craft extremely convincing emails based on the company's internal communication style.
Impersonation is at the Core of Phishing
To solve for Phishing, one needs to exhaustively solve for Impersonation at the core.
Nearly 75% of all Phishing campaigns use some form of Impersonation tactic.
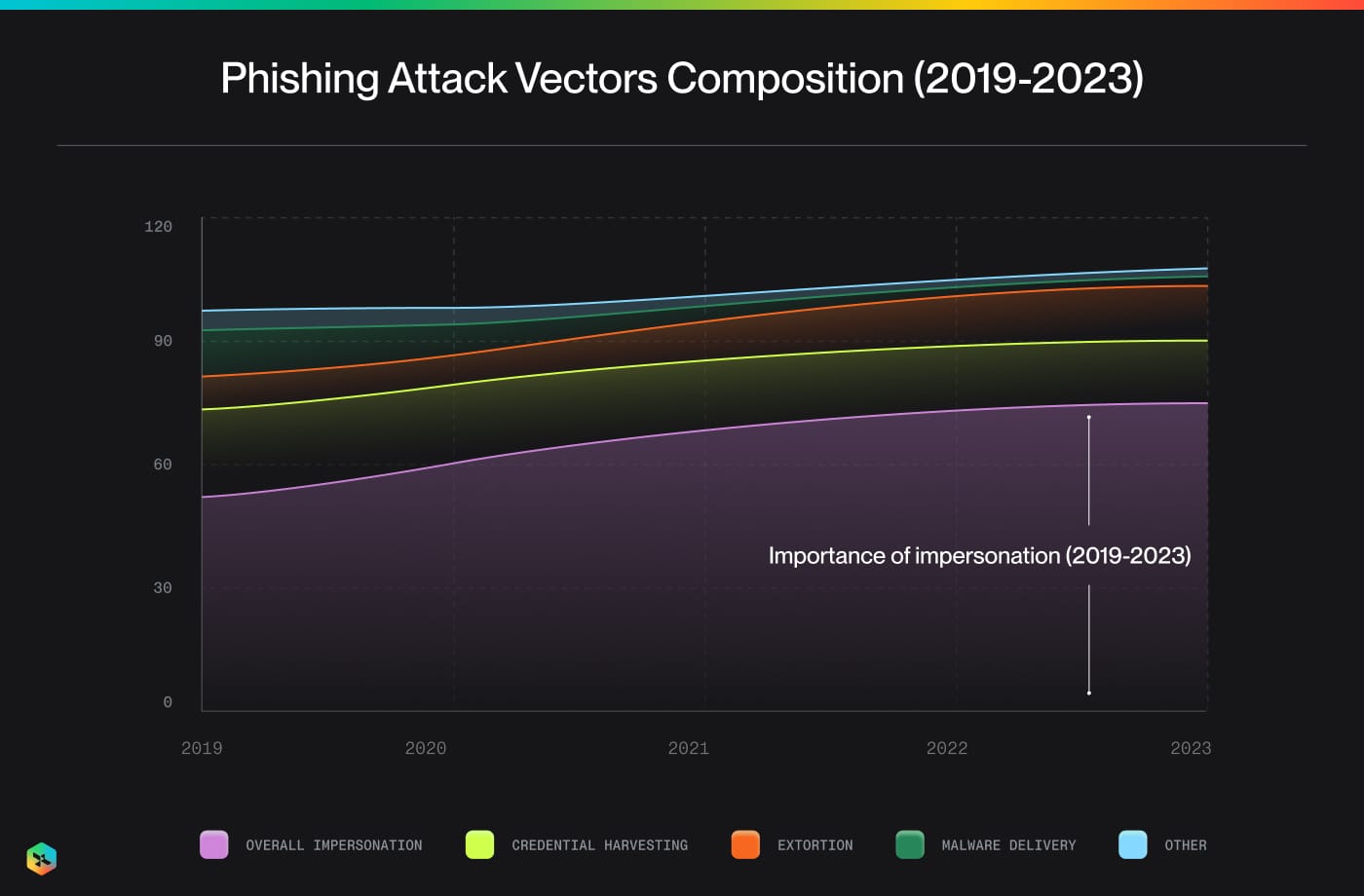
Here's a further breakdown of what kind of Impersonation is prevalent in the current landscape.
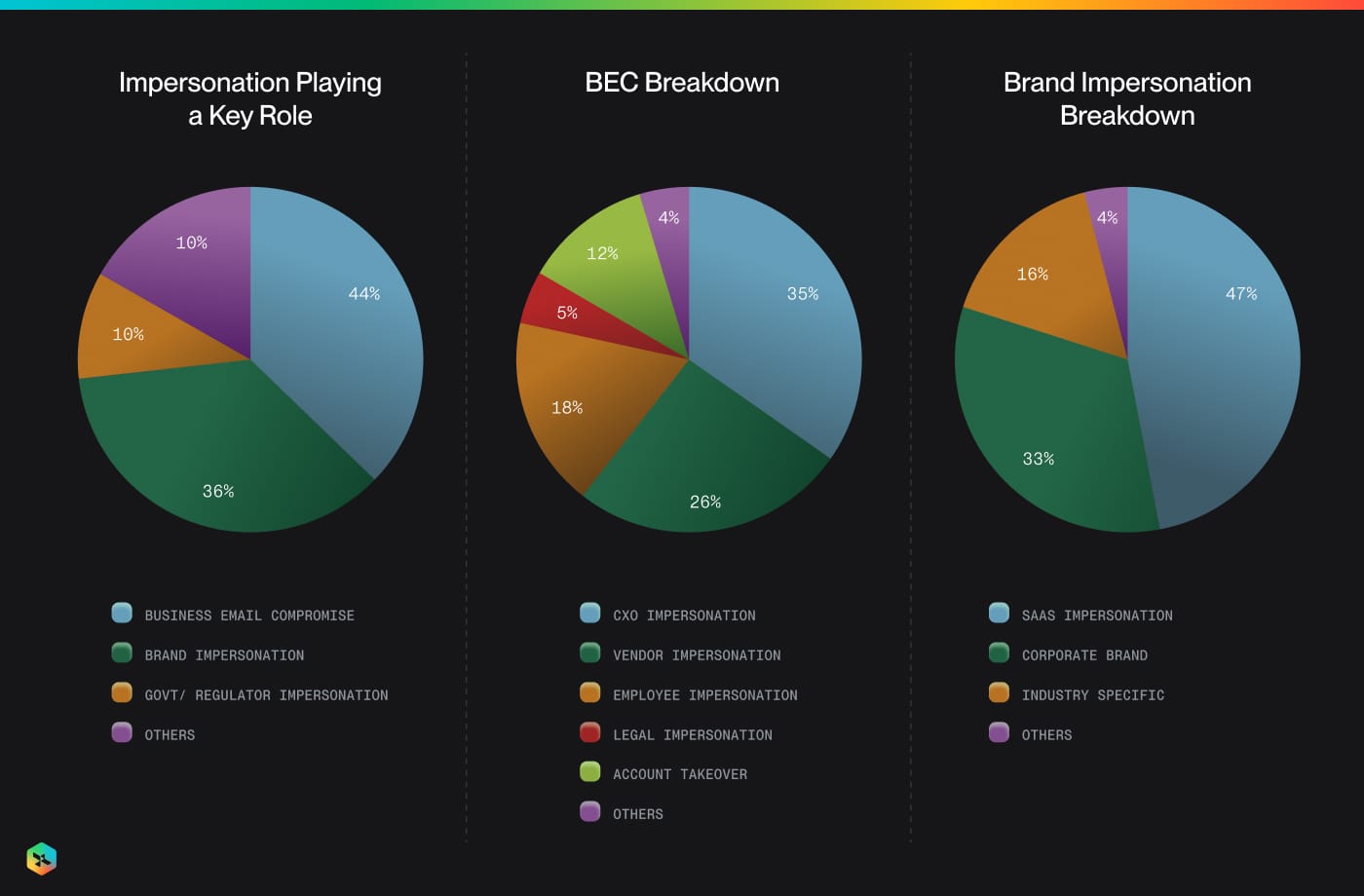
The Missing Context in Impersonation Detection
One of the reasons why BEC attacks are highly effective is that - the existing set of tools are limited in understanding the context of the organization like the business domain, vendors, SaaS tools, the regulatory & institutional interaction landscape, thus exploiting the gaps in the knowledge of the threat detection systems.
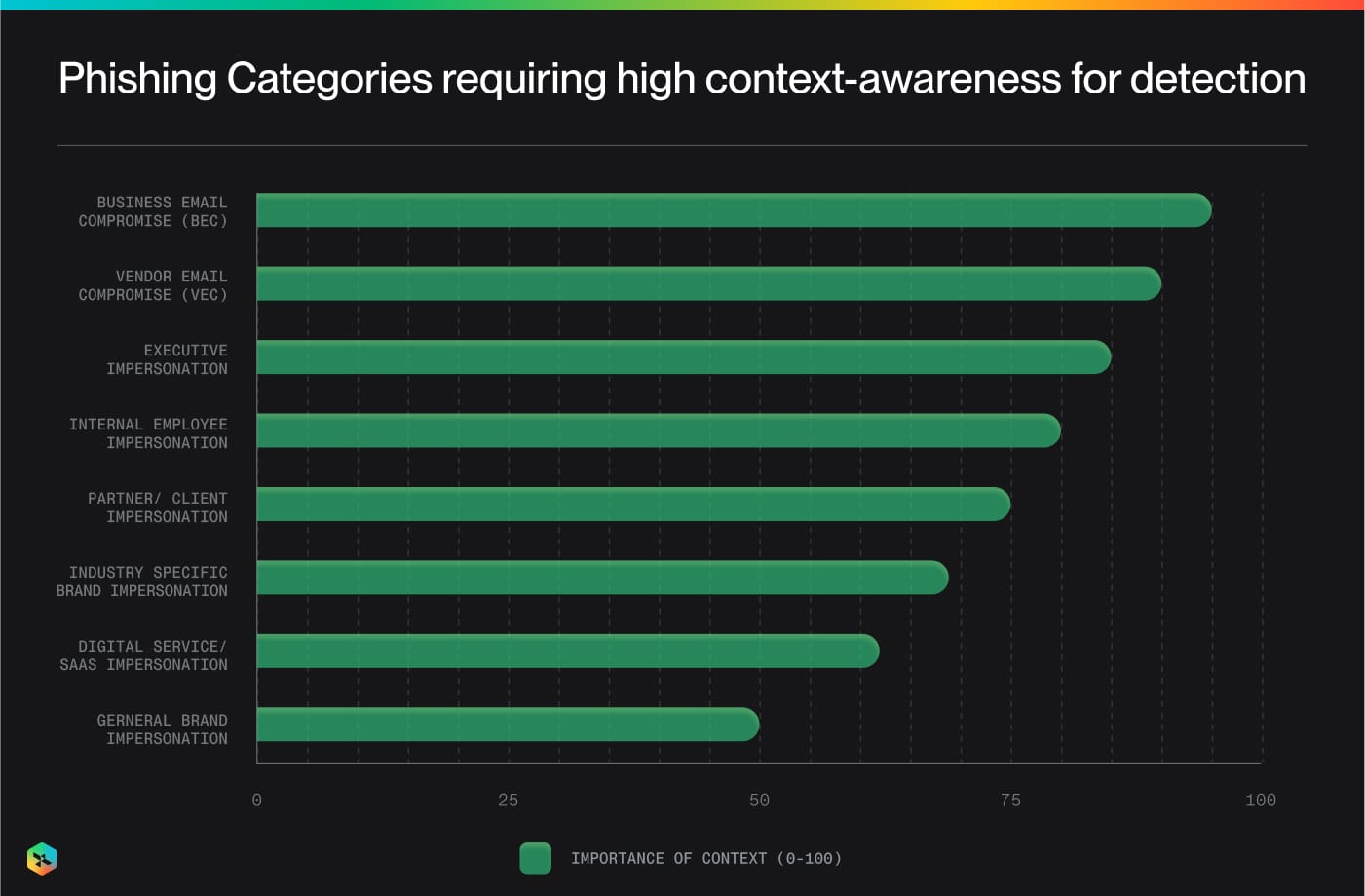
Existing email security products operate as blackbox when it comes to impersonation detection & essentially all human-centric attacks requires context-based protection
AI-Native Approach for Impersonation Detection
One of the problems with existing systems is the - manual intervention for users, vendors, domains, spoofing etc. AI is not only superior when it comes to applying heuristics but also in bringing a wide-range of context into the detection itself.
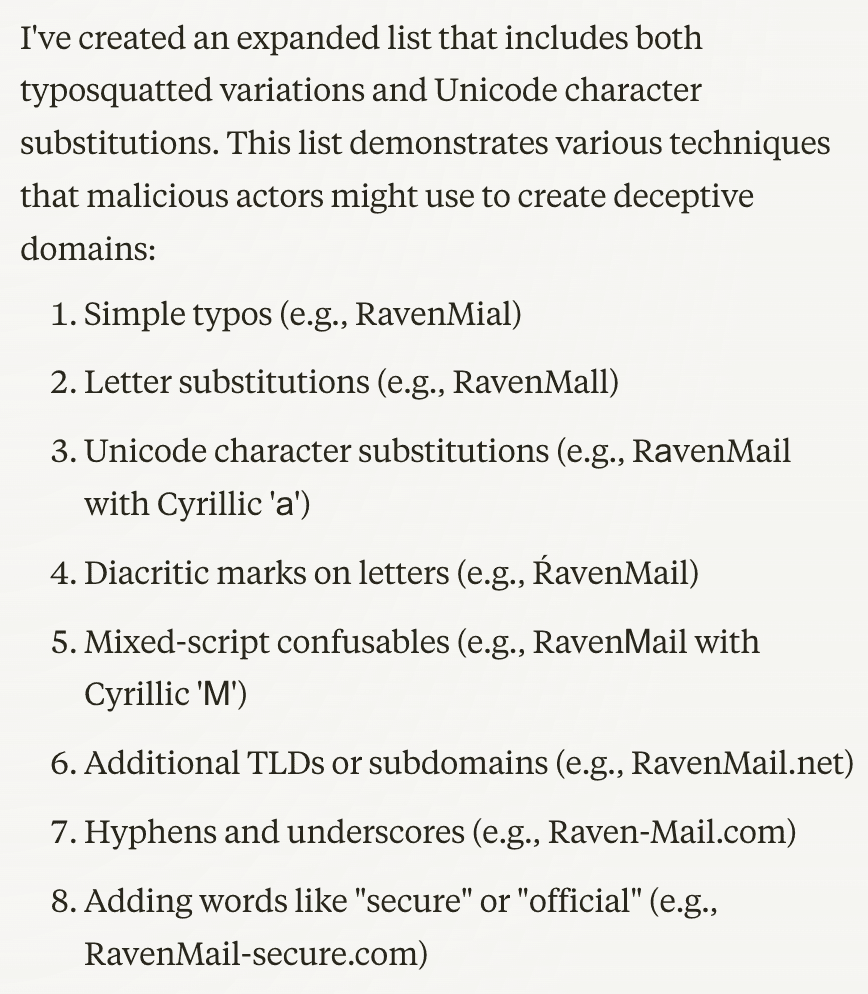
A quick example of domain spoofing logic from an AI Chat bot reveals the dynamic ways it can be programmed to help in detection.
At RavenMail, we have deeply applied AI into our detection engines - some of the key elements are
- Generating custom detection logics given the nature of rules to be written
- Analysing all signals, inferences and detections & marrying it with context data to enhance Threat Detection
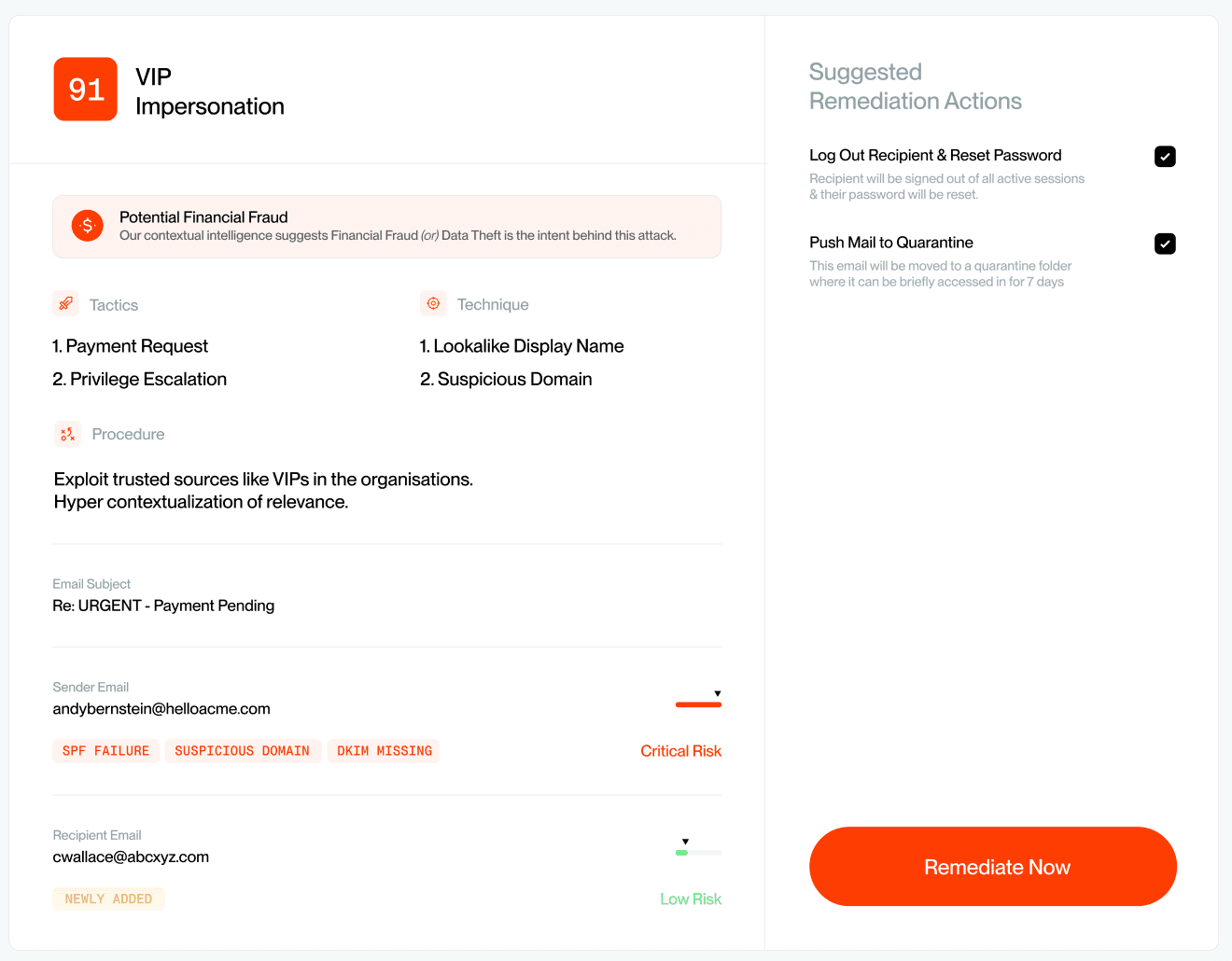
- Explainability of why the detection is a threat
- MailSecOps workflows
- Enterprise-grade LLMs with India region deployment
Here's an overview of our Threat Detection Model, as always the disclaimer is - this is a Beta version and this model will undergo changes as per market needs & feedback.
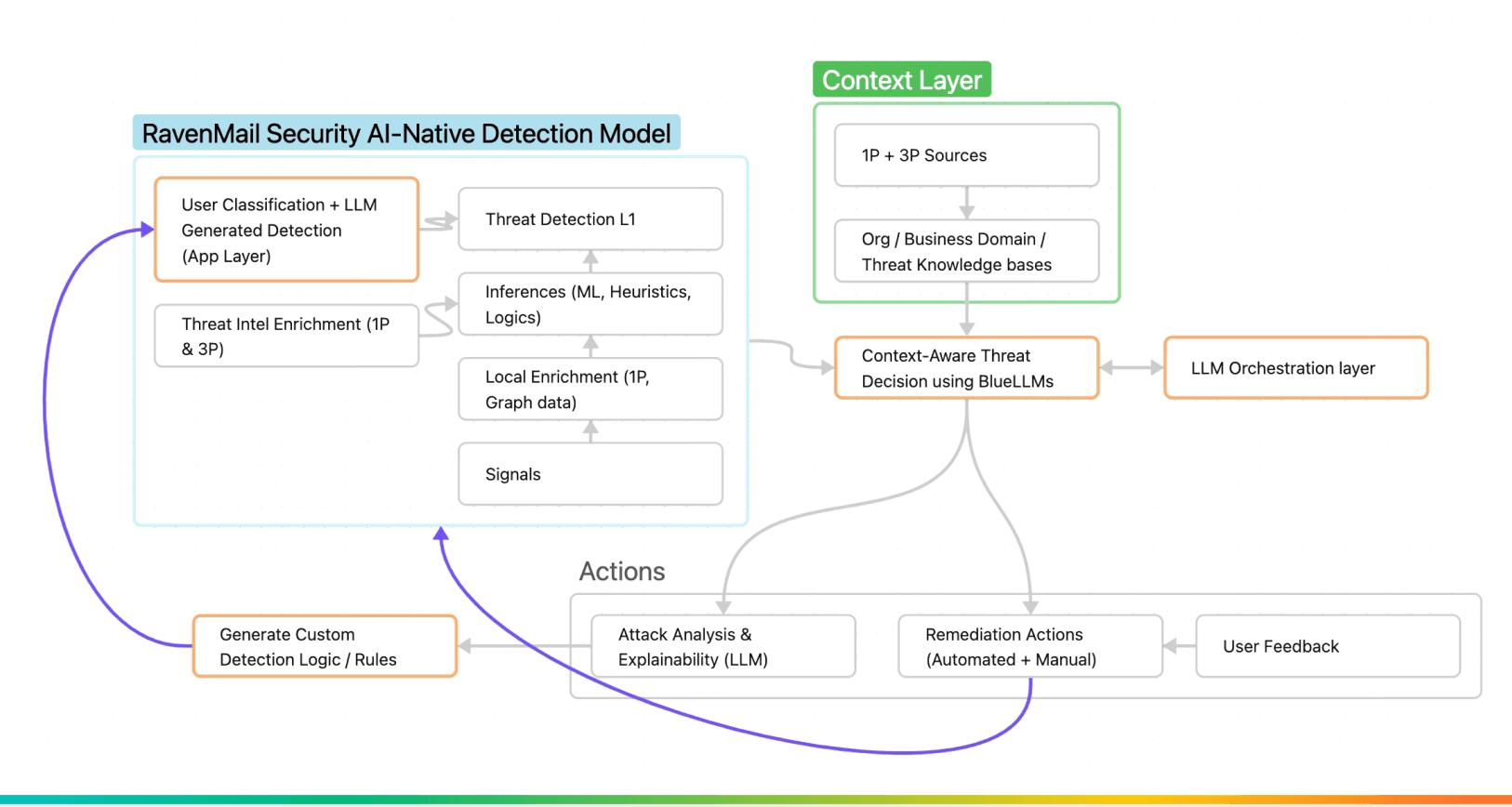
Our system has the following advantages
- Classify with contextual detection - CXO protection, Government / Regulator Impersonation, SaaS tools impersonation and expand into any relevant category for our clients
- Learning without training - Ex: Predict who are likely vendors
- Explainability for SoC Analysts
- Ability to use multi-modal inputs
Comparison with Existing Vendors
Most existing vendors provide Impersonation protection as part of their entire email security suite or bundled with email service itself.
One of the key reasons BEC attacks slip through existing mail security solutions is the lack of context and in-ability to stitch information across various signals.
Most solutions offer the following
- Display Name Spoofing of external mail id to internal employee
- Sender-Recipient Relationship strength
To customise the Spoofing rules, one needs to learn Powershell Scripting or navigate complicated workflows in Defender
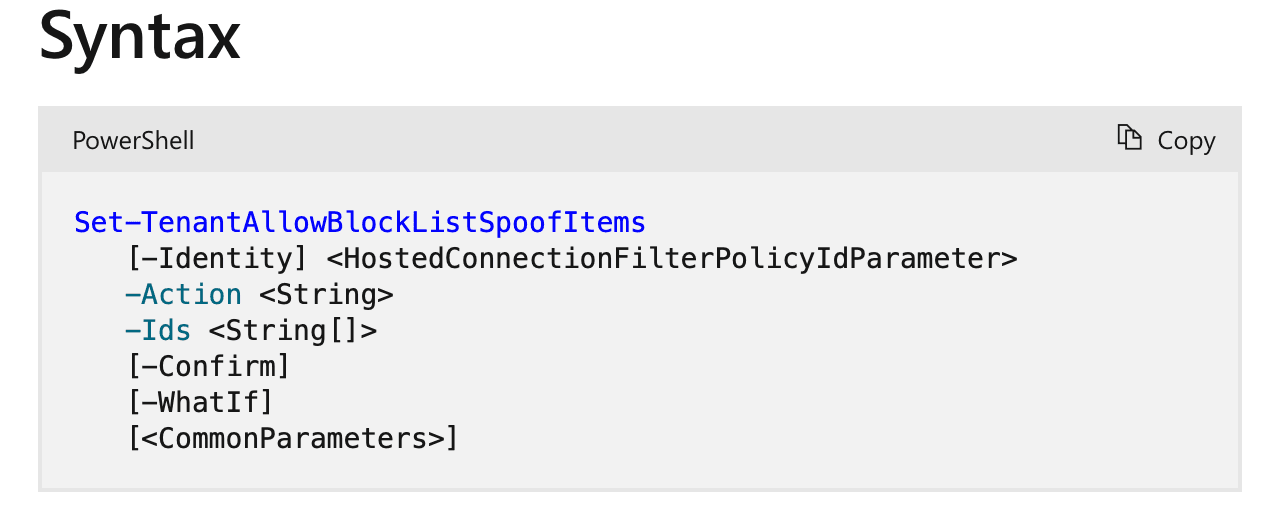
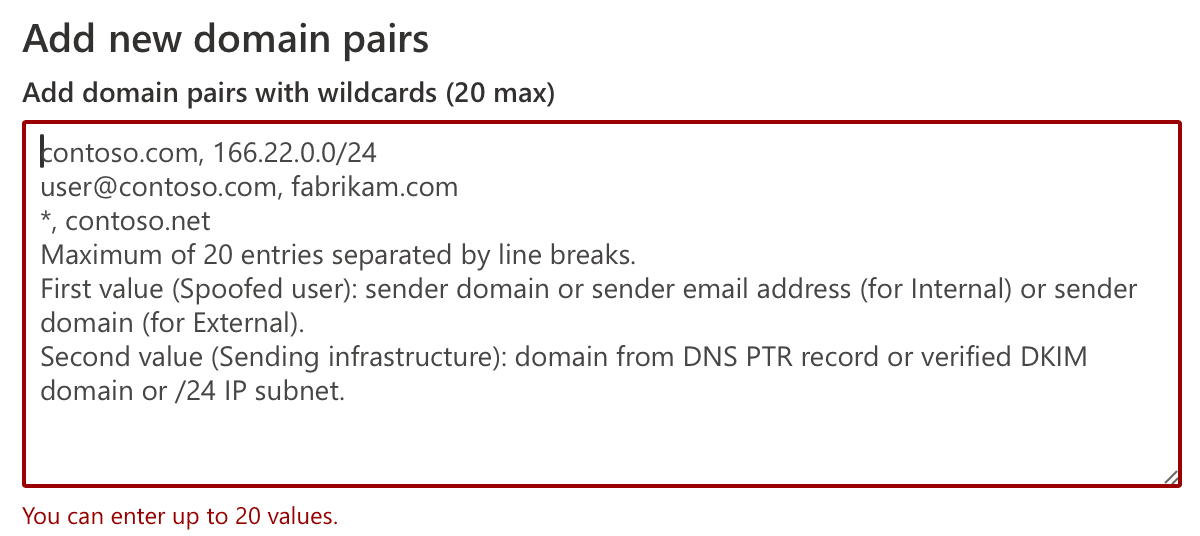
Not only these solutions are cumbersome, it doesn't capture the context of the nature of entity impersonating them and hence the threat detection outcome itself.
At RavenMail, we want to be at the forefront of email & communications protection for the AI-era
Modern Protection for the AI-Era
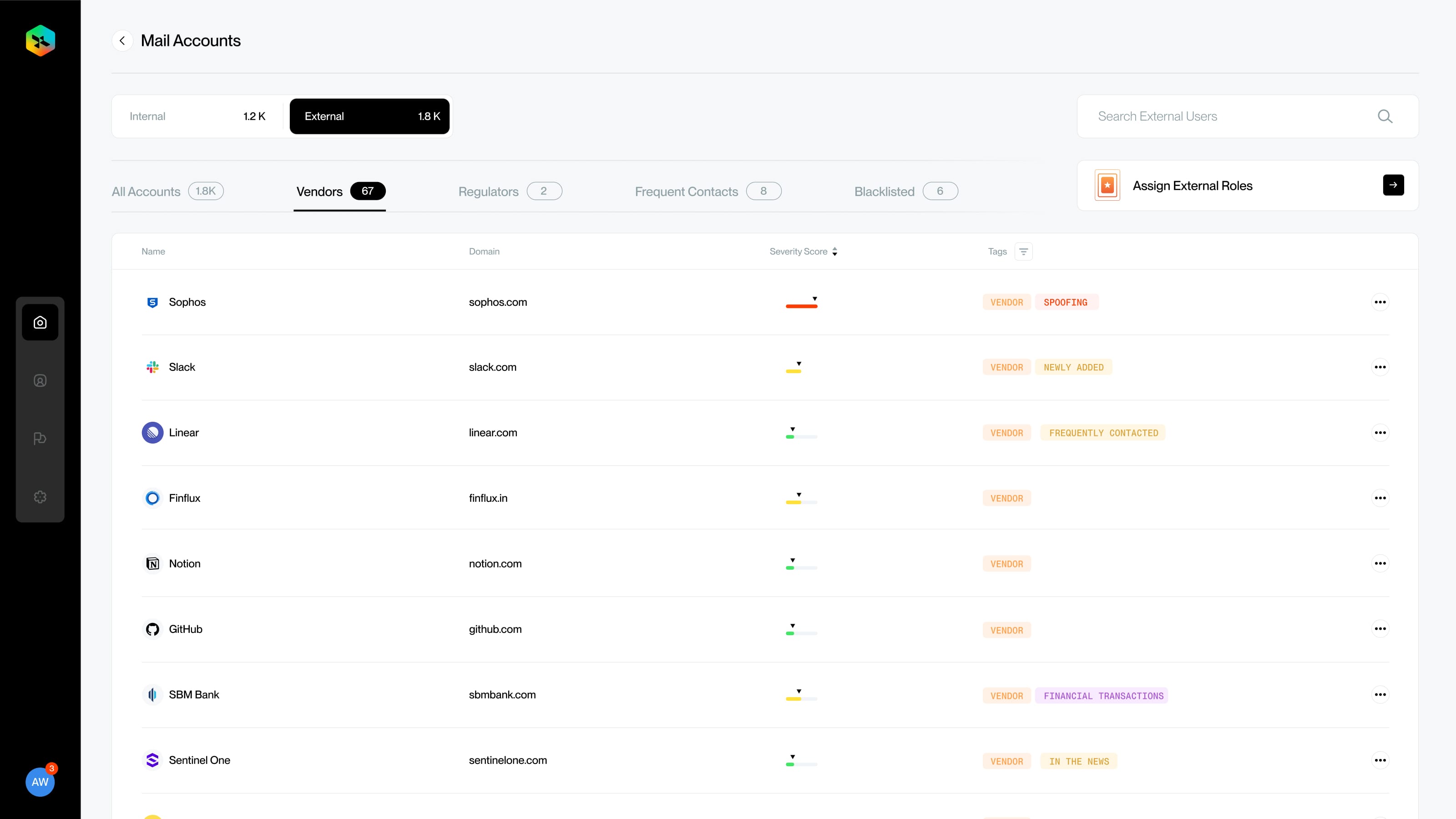
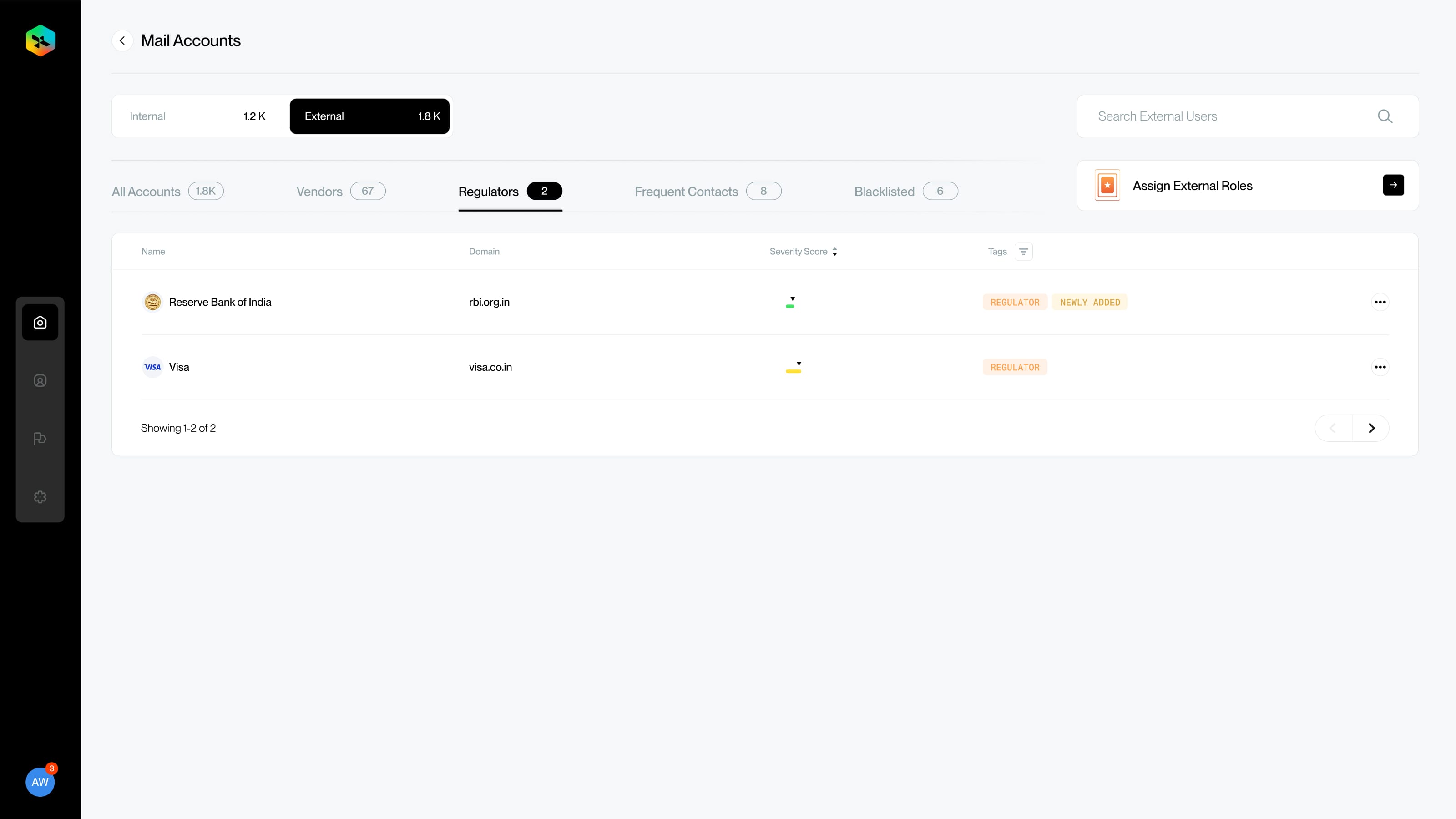
We have launched our first version of the product to our Beta clients with the following features
- VIP /CXO / Executive Impersonation protection
- Regulators / Government Bodies / Institutional Impersonation protection
- SaaS tools Impersonation Protection
- Vendors / Clients / Partners Email Compromise Protection
Here's an overview of our product screens
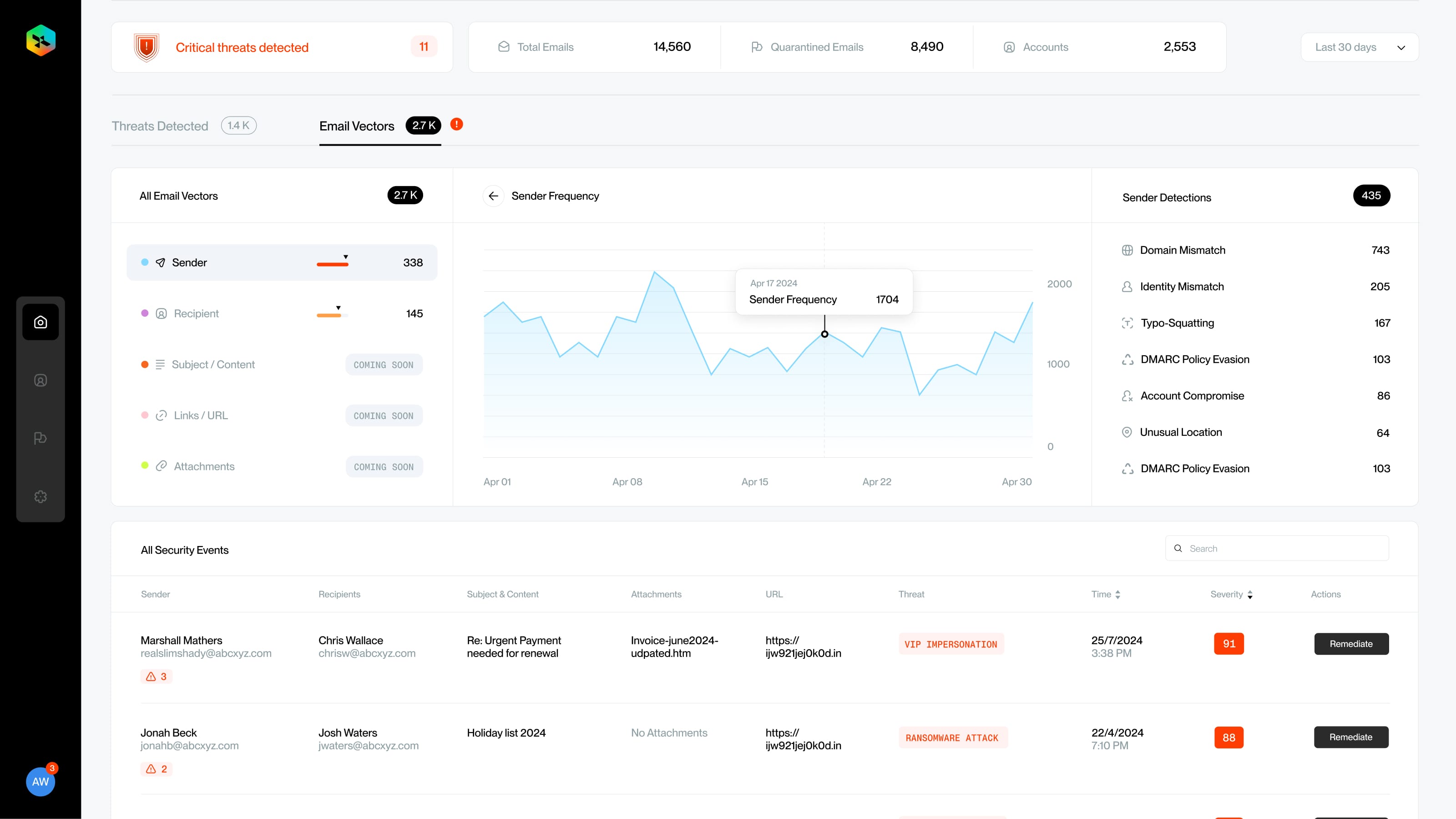
Comments
Your comment has been submitted