How Sophos newsletter forums were gamed to distribute malware to its clients
TL:DR - A malicious link linked to QakBot infrastructure slipped into a Sophos Community Daily Digest via a user comment. Traditional email security missed it — Raven caught it using context-aware, AI-driven detection
Newsletter Forums as Phishing Vector
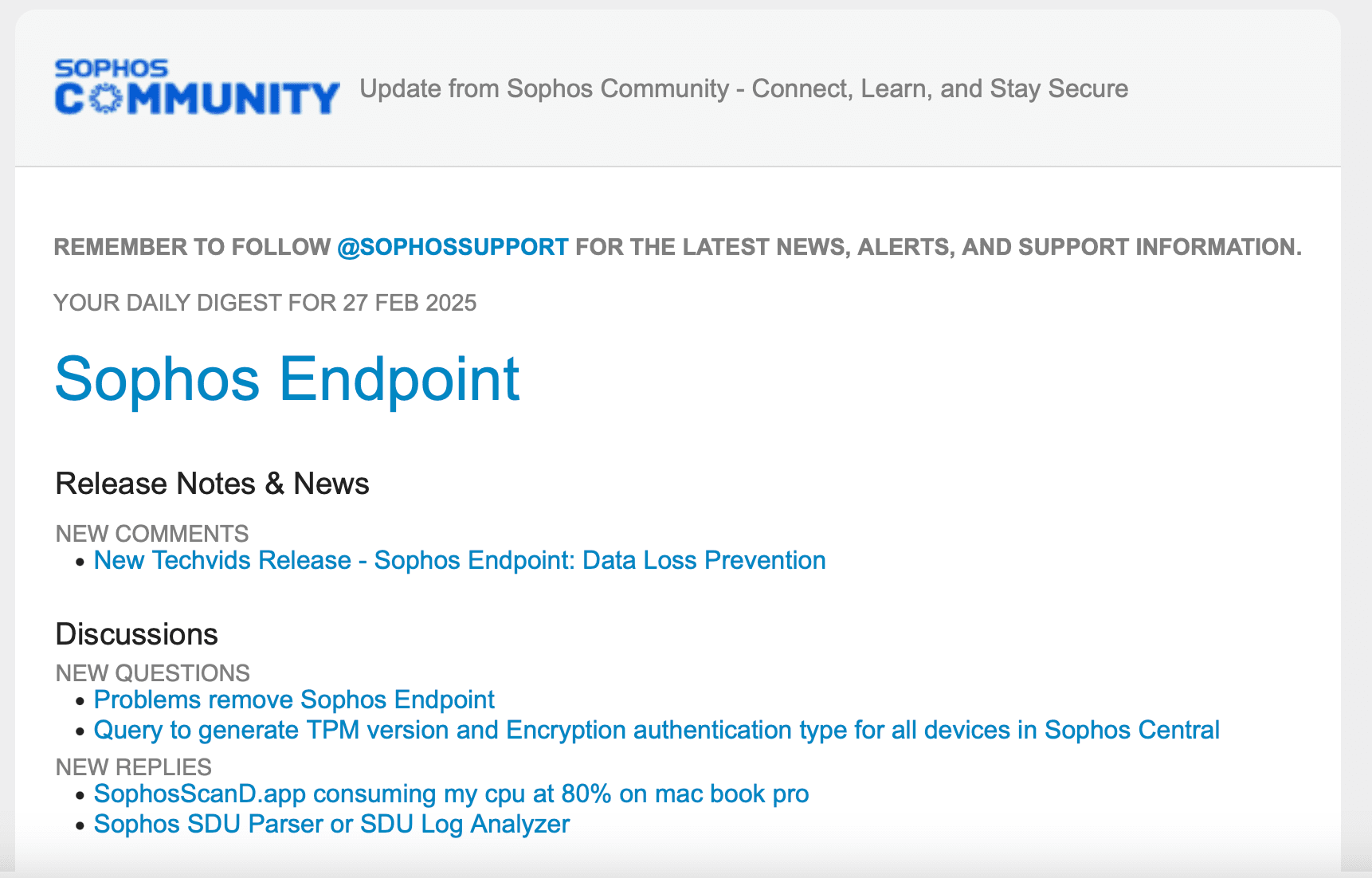
The Sophos Community Daily Digest is an automated email summary sent to registered users of the Sophos Community forum. It highlights recent discussions, comments, and activity across various cybersecurity topics. Designed to keep users informed and engaged, the digest reflects real-time user participation — including links and content contributed by the community.
Anyone with a Sophos Community account — this includes:
- End users of Sophos products (admins, analysts, IT staff)
- Prospects or evaluators who signed up for discussions
- Sophos partners and MSPs
It’s not limited to paying customers, but many enterprise clients subscribe to it to stay updated on product-related discussions, threat insights, or peer problem-solving.
Breach of Trust: Malicious link in Newsletter Digest
On February 27, 2025, recipients of the Sophos Community Daily Digest received what looked like a harmless forum update. Buried in a comment under a post about Data Loss Prevention was an unexpected hyperlink
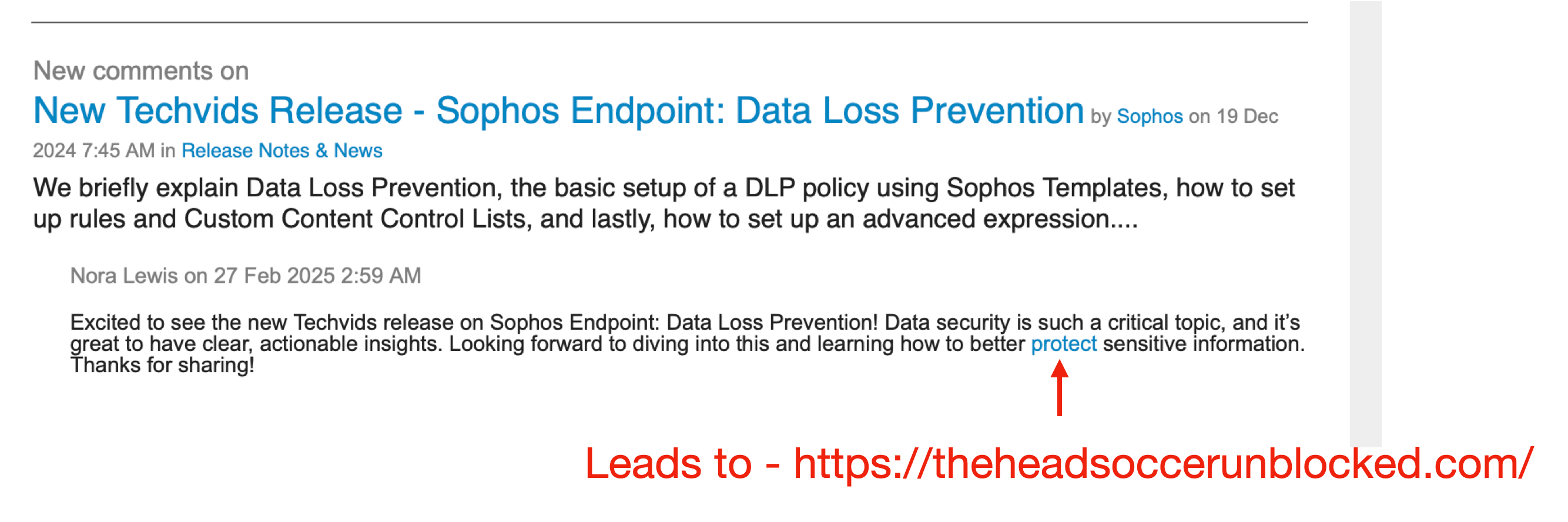
This wasn't just a random gaming site.
Upon analysis, Raven’s threat engine flagged it as part of the QakBot malware distribution infrastructure — linked to malicious ZIP payloads, obfuscated JavaScript droppers, and historical C2 activity.
Yet Sophos' own community digest circulated it — and it reached inboxes unfiltered.
How did this happen - Delayed URL attack?
The domain in question possible had a clean reputation at the time of posting, but was later weaponized. The sequence likely unfolded like this:
Step | What Happened |
|---|---|
🧑💻 User Post | A user (or a bot) commented on a forum thread and embedded the domain. |
📨 Newsletter Generated | Sophos’ automated system compiled the comment into its daily digest and sent it to community members. |
🔄 URL Goes Live | At a later point, the domain began hosting malware payloads tied to QakBot |
✅ Passed Email Security | Because the domain had not yet been flagged by threat intel feeds, no major email security vendor blocked it. |
🚨 Raven Detected It | Raven’s out-of-context URL scanner flagged it based on historical behavioral patterns, subdomain reputation, and downloaded file telemetry. |
The Core Problem: Traditional Trust Signals No Longer Work in Email Security
Most email security systems still rely heavily on legacy indicators of trust — things like SPF/DKIM alignment, sender reputation, and basic URL reputation. In theory, these were designed to validate that an email is legitimate. In reality, attackers have learned to weaponize the very signals that were meant to ensure safety.
Here’s why they fail:
Trust Signal | Why It Fails Today |
|---|---|
SPF/DKIM/DMARC | These only verify that the sender is authorized — not whether the content is safe. A malicious link in a community forum digest with perfect email authentication will pass untouched. |
Sender Reputation | If the sender is a known vendor (e.g., Sophos), their emails are implicitly trusted — even when they contain user-injected malicious content. |
URL Reputation | Most systems check reputation at time of delivery. But attackers often weaponize links after the email is sent, or use newly registered domains that haven’t yet been flagged. |
Attachment Scanning | Not relevant when the threat is a URL or delayed-download payload. |
Traditional signals validate who sent the email — but not why it was sent, or what the content implies.
To catch modern threats, we need systems that ask:
“Does this message make contextual sense?” — not just “Does this link look safe right now?”
This is the shift Raven enables.
How Raven AI Caught What Others Missed
While traditional email security systems assessed the Sophos newsletter as safe based on sender reputation and static URL checks, Raven took a fundamentally different approach — analyzing the context, behavior, and intent behind every element of the message.
Context-Aware Detection
Raven evaluated the email in context: a technical discussion on data loss prevention containing a hyperlink to a gaming domain was immediately flagged as anomalous. The platform identified the link as contextually irrelevant and potentially suspicious, even before the domain appeared in threat feeds.
Behavioral and Historical Analysis
Raven traced the domain's behavior over time — uncovering its association with known malware payloads, including ZIP and JavaScript files frequently used in QakBot distribution. This longitudinal view allowed Raven to flag emerging threats before traditional reputation systems caught up.
LLM-Based Anomaly Detection
Using large language models trained on legitimate business communication patterns, Raven identified the inconsistency between the message content and the embedded link. This AI-native analysis enabled it to detect out-of-place URLs and content mismatches that signature-based tools miss entirely.
Raven doesn't just scan for known bad indicators — it understands what doesn’t belong.
Go-live in 5 mins with Raven
To get a free-trial with Raven fill the contact form below
Disclaimer: The URL in question was removed by Sophos at the time of posting. The purpose of this blog post is to highlight evolving phishing tactics and underscore the importance of context-aware threat detection in modern email security. The reference to Sophos is based on a publicly observed incident involving a community-generated newsletter and is not intended to criticize or undermine Sophos as a cybersecurity provider. Sophos remains a respected player in the cybersecurity ecosystem. This post does not claim or imply any breach or failure on the part of Sophos’ core security infrastructure or products.
All observations are based on publicly available information and security analysis as of the date of publication.
Comments
Your comment has been submitted