The Silent Threat: Why SEGs, Google, Microsoft Struggle to Stop Executive Impersonation
TL;DR
Modern executive impersonation attacks don’t carry links, malware, or spam—they carry intent. A simple “Are you available?” can be the start of a multi-stage, high-stakes attack. Legacy email security systems—from SEGs to Google and Microsoft—miss them because they scan emails, not conversations. Raven was built from the ground up to detect impersonation through context, not just content.
The New Face of Email Attacks: No Payload, Just Pressure
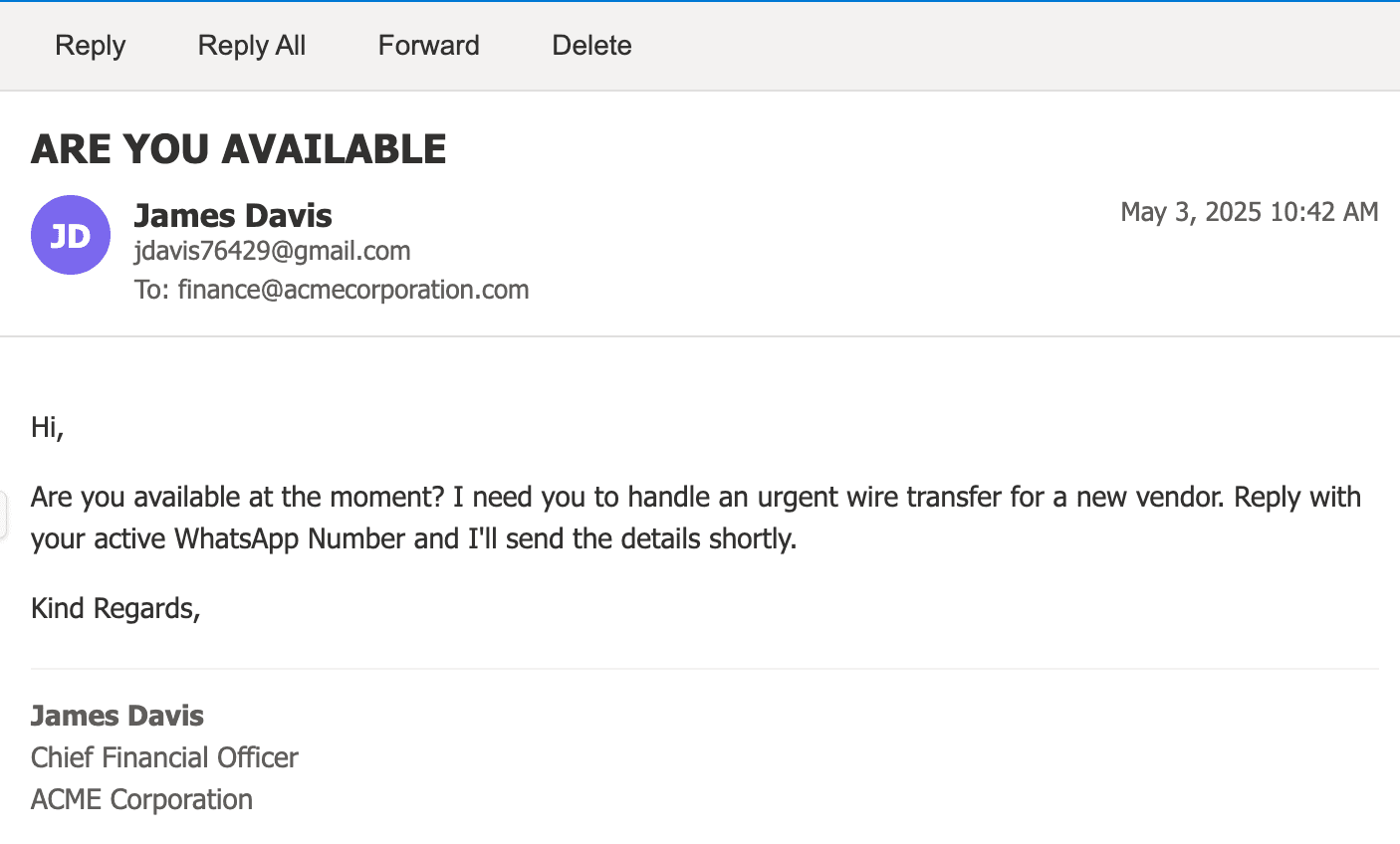
Most executives brush off emails like these:
Subject: Quick Request
Body:Hey, are you around? Need a quick favor.
No link. No attachment. Nothing overtly malicious.
But this isn’t random. It’s a calculated opening move. We wrote about this earlier here about the links between email impersonation and WhatsApp based impersonation.
How Executive Impersonation Attacks Unfold
Stage 1: The Setup
The attacker poses as a senior executive—typically a CEO, CFO, or Head of Department. They send a short, urgent message from a personal email address or lookalike domain. The goal is simple: provoke a response.
Stage 2: The Hook
Once the recipient replies, the attacker escalates. They now have a live conversation and legitimacy. Common next steps include:
- Requesting a confidential employee report
- Asking for an urgent wire transfer
- Instructing access to sensitive internal systems
These messages often reference real names, departments, or workflows to increase believability.
Stage 3: The Execution
If the recipient complies, the organization suffers:
- Wire fraud
- Data leakage
- Policy violations
- Reputational fallout
These attacks don’t exploit technical vulnerabilities. They exploit human psychology—and legacy email security systems fail to catch them in time.
Why SEGs and Cloud Email Tools Miss the Threat
Existing Solutions | Why It Fails |
|---|---|
SEGs (Proofpoint, Mimecast, etc.) | Focused on malware, links, and known threat indicators. Impersonation emails have none of these. |
Microsoft Defender / Google Workspace Security | Effective at scanning links, attachments, and reputation-based indicators. Fail when the email contains only plain text with crafted intent. |
SPF / DKIM / DMARC | These protocols confirm that the sender’s domain is allowed to send the message. They do not detect when someone is pretending to be your CEO or their intent. |
Tenant-level AI in Microsoft/Google | Rely on large-scale telemetry, often missing low-volume, targeted impersonation attempts that are new or uncommon. |
These systems treat each email as an isolated event. They don’t model behavior over time, and they don’t understand subtle deviations in communication tone, authority, or relational history.
Common Impersonation Scenarios That Get Missed
Personal Gmail Posing as the CEO
`[email protected]` sends an urgent payment request to a finance associate. The sender name looks legitimate. The email body is clean. The result? A silent transfer of funds.
Vendor Thread Hijacking
A compromised vendor email thread is used to send altered bank account details. Since it’s a legitimate thread, filters trust the message.
Consultant Impersonation
A third-party posing as a known consultant says, “As per the CEO’s instructions…” and instructs HR to share employee data. The name drop is enough to bypass suspicion.
In all of these, the attacker wins by staying within the boundaries of normal-looking behavior while subtly steering the recipient toward action.
The Organizational Impact
- Financial Loss: Wire frauds and diverted payments can cost millions.
- Data Breaches: Sensitive employee, client, or financial data leaked due to misplaced trust.
- Compliance Violations: Violations of internal controls, SOX, GDPR, or sector-specific data handling rules.
- Reputational Damage: Employees and partners lose trust in leadership communication integrity.
Even more damaging: most of these events go undetected until an audit or customer complaint.
How Raven Catches What Others Miss
Raven is purpose-built to detect impersonation and social engineering threats—not just based on what the email says, but why it’s being said, and who’s saying it.
Raven Capability | Why It Matters |
|---|---|
LLM-based Behavioral Modeling | Raven learns the communication patterns of every executive—tone, timing, linguistic quirks—and flags messages that deviate. |
Out-of-Context Request Detection | Detects when the content of a message (e.g., payment request, access ask) doesn’t match the context of the sender or thread. |
Relationship Graph Analysis | Builds dynamic relationship graphs to understand who normally communicates with whom—and who doesn’t. |
Cross-Email Thread Analysis | Raven correlates signals across multiple messages and threads. It sees manipulation in progress, not just in a single email. |
Inline Warnings and Escalation Options | Provides real-time alerts to users and administrators with options to quarantine, forward for review, or block execution. |
Raven doesn’t rely on signature files, blocklists, or rules. It learns. It adapts. It understands identity as a pattern—not a static string in an email header.
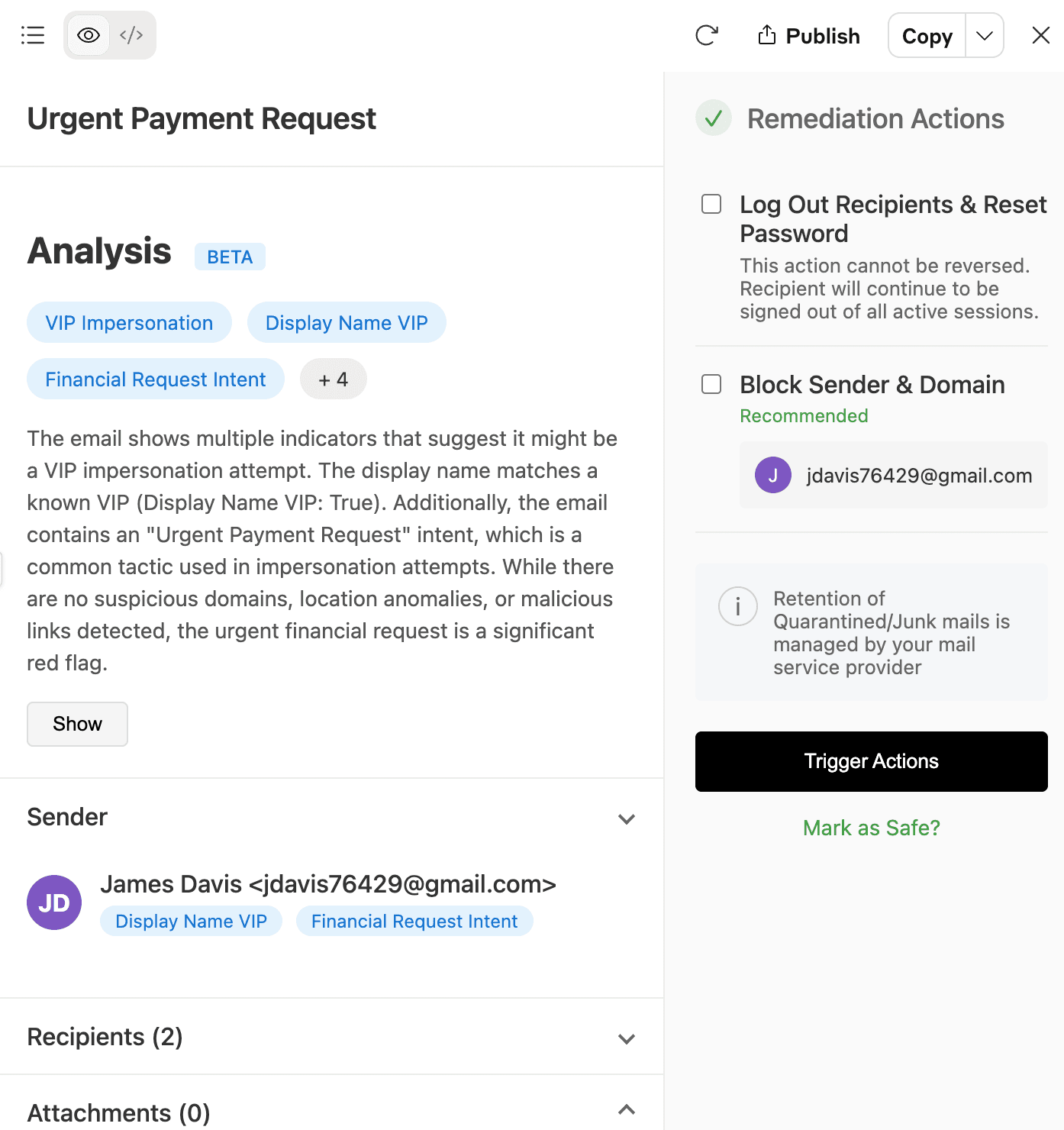
Detecting & Remediating Impersonation in Raven
Raven identifies your executives automatically using meta-data or allows you to manually configure the VIP accounts.
Raven provides a comprehensive summary of the nature of attack and along with it appropriate remediation actions.
In a single click the mail can be removed from affected inboxes in manual mode or just set up automatic remediation to filter without admin intervention.
The Bottom Line
Executive impersonation is not a technical attack. It’s a psychological one.
It doesn’t trip filters. It trips decision-makers.
And in a world where trust is the attack surface, the only way to stop these threats is by understanding the context behind the conversation.
To prevent executive impersonation attacks in your organization ask for a free-trial below.
Comments
Your comment has been submitted