CEO Impersonation on WhatsApp & the Role of Email enabling Cross-Platform attacks
Introduction
In today's interconnected business world, communication platforms like email and WhatsApp have become integral to daily operations. However, this multi-channel approach has opened new avenues for cybercriminals. A particularly insidious threat has emerged: cross-platform CXO impersonation attacks. These sophisticated schemes leverage the unique characteristics of different communication channels to manipulate victims and bypass security measures.

The Intelligence Gathering Phase: Exploiting Public Professional Databases
Before delving into the mechanics of email-to-WhatsApp attacks, it's crucial to understand how attackers arm themselves with information to make their impersonations convincing. One of the most accessible and potent sources of such information is publicly available professional databases and networking sites.
The Role of Professional Intelligence Platforms
Platforms like ZoomInfo, SignalHire, and RocketReach have revolutionized business intelligence and recruitment. However, they've also inadvertently become treasure troves for cybercriminals planning impersonation attacks. Here's how attackers exploit these resources:
- Organizational Hierarchy Mapping: These platforms often provide detailed org charts, allowing attackers to understand reporting structures and identify high-value targets.
- Contact Information Harvesting: Attackers can easily obtain professional email addresses and sometimes even direct phone numbers of executives and key employees.
- Career Trajectory Insights: By analyzing career histories, attackers can craft more believable narratives, referencing past roles or companies in their impersonation attempts.
- Corporate Jargon and Culture: Job descriptions and company overviews provide attackers with industry-specific terminology and insights into corporate culture, making their communications seem more authentic.
- Identifying Potential Victims: These platforms allow attackers to pinpoint employees in finance, HR, or other sensitive departments who might have the authority to perform requested actions.
- Cross-Referencing Data: By combining information from multiple platforms, attackers can build comprehensive profiles of their targets and the executives they plan to impersonate.
Bridging to Email and WhatsApp Attacks
Armed with this rich, publicly available data, attackers can craft highly convincing initial emails. They can reference correct job titles, mention recent company news or initiatives, and use appropriate corporate language. This level of detail lends credibility to their impersonation, making the eventual transition to WhatsApp seem more plausible and less suspicious.
The Prevalence of Email-to-WhatsApp Attacks
While cross-platform attacks can occur in various ways, our research indicates that email-to-WhatsApp attacks are significantly more common. In fact, a crucial finding is that most WhatsApp-based attacks can be traced back to origins in email communication. This trend reflects a calculated strategy by cybercriminals to exploit the strengths and weaknesses of both platforms.
Why Email-to-WhatsApp is the Preferred Attack Vector:
- Email as the Attack Origin: Our data shows that an overwhelming majority of WhatsApp-based impersonation attacks have some connection to email. This could range from initial contact via email to the use of email for gathering intelligence or establishing credibility before moving to WhatsApp.
- Established Trust: Email remains the primary formal communication channel in most businesses. Attackers leverage this to establish initial credibility, making the transition to WhatsApp seem more natural and less suspicious.
- Rich Data Source with Context: Corporate email often contains valuable information about organizational structure, ongoing projects, and communication styles. Attackers use this intelligence to craft more convincing WhatsApp impersonations.
- Familiarity with Email Spoofing: Cybercriminals have extensive experience with email spoofing techniques. They often use this as a starting point, even if the main attack occurs on WhatsApp.
- Verification Challenges for WhatsApp: Many organizations have robust email security but lack equivalent measures for WhatsApp. The transition from a 'secure' email environment to WhatsApp can catch victims off guard.
- Perceived Urgency: After establishing context via email, attackers use WhatsApp to escalate the perceived urgency of their requests, exploiting its association with immediate, informal communication.
- Exploitation of WhatsApp's Privacy Features: The move to WhatsApp allows attackers to take advantage of its end-to-end encryption, making detection more difficult once the conversation has moved platforms.
- Multi-Stage Attack Opportunity: Starting with email allows attackers to conduct multi-stage attacks. They can use email for reconnaissance and initial trust-building, then switch to WhatsApp for the final, often more urgent or sensitive, phase of the attack.
This prevalent pattern of email-to-WhatsApp attacks underscores the need for organizations to view their communication security holistically. While securing each platform individually is crucial, it's equally important to focus on the transitions between platforms, as these often represent the most vulnerable points in the communication chain.
The Anatomy of an Email-to-WhatsApp Attack
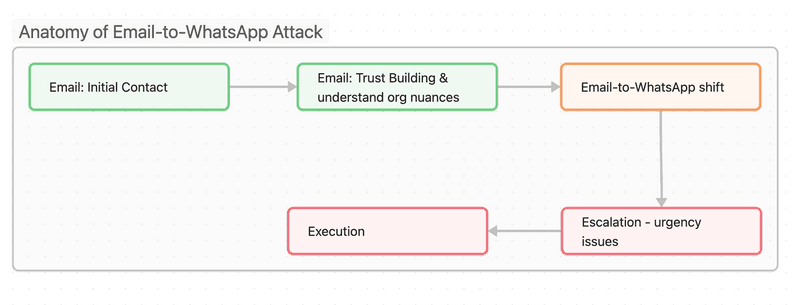
A typical attack might unfold as follows:
- Initial Contact: The attacker sends a spoofed email impersonating a high-level executive, often the CEO or CFO.
- Trust Building: Through a series of emails, the attacker establishes credibility and creates a sense of importance around a particular issue.
- Platform Shift: The attacker suggests moving the conversation to WhatsApp for "security" or "urgency" reasons.
- Escalation: On WhatsApp, the attacker ramps up the pressure, often pushing for immediate action like a fund transfer.
- Execution: The victim, convinced by the initial email exchange and feeling the urgency on WhatsApp, complies with the attacker's request.
The WhatsApp Factor: A Double-Edged Sword

WhatsApp's end-to-end encryption, while excellent for user privacy, presents unique challenges in combating these attacks:
- Content Inaccessibility: The encryption prevents external tools from scanning message content for threats.
- Limited Monitoring: Traditional security measures can't perform real-time analysis of WhatsApp communications.
- False Sense of Security: Users may assume that WhatsApp's encryption makes it inherently secure, lowering their guard against social engineering.
Attackers exploit these factors, using WhatsApp as a "blind spot" in corporate security to advance their schemes.
Case Studies: Real-World Examples of Cross-Platform Attacks
Case Study 1: The CFO Wire Transfer Fraud
A multinational corporation fell victim to a sophisticated attack where the CFO was impersonated. The attacker initially contacted the finance department via a spoofed email, discussing an urgent and confidential acquisition. After establishing credibility through several email exchanges, the impersonator suggested moving to WhatsApp for "secure, real-time updates." On WhatsApp, the attacker pressured a senior finance employee to make a swift wire transfer of $1.5 million to "secure the deal." The fraud was only discovered when the real CFO inquired about the unusual transaction days later.
Case Study 2: The Gift Card Scam
In a notable incident, a mid-sized tech company fell victim to a sophisticated gift card scam. The attack unfolded as follows:
- Initial Email: An employee in the HR department received an email seemingly from the CEO, discussing an urgent employee appreciation initiative.
- Trust Building: Over a series of emails, the "CEO" explained the need for discretion to maintain the surprise element of the initiative.
- Platform Shift: The attacker suggested moving to WhatsApp for quicker communication and to "avoid leaks."
- Escalation on WhatsApp: On WhatsApp, the impersonator urged the HR employee to purchase a large number of gift cards for the supposed initiative, promising reimbursement.
- Execution: The employee, convinced by the elaborate setup and feeling pressured by the perceived urgency, purchased $50,000 worth of gift cards and sent the codes via WhatsApp.
The fraud was only discovered days later when the real CEO inquired about an unrelated HR matter. By then, the gift cards had been redeemed, and the funds were irretrievable.
Case Study 3: The UPI Scam
In India, where digital payments via UPI (Unified Payments Interface) are ubiquitous, attackers have adapted their techniques to exploit this system:
- Email Impersonation: An accounts payable employee at a large Indian corporation received an email from what appeared to be the company's Managing Director.
- Contextual Manipulation: The email discussed a confidential new vendor partnership, adding credibility by referencing recent company news.
- WhatsApp Transition: The "MD" asked to continue the conversation on WhatsApp, citing the need for end-to-end encryption due to the sensitive nature of the deal.
- UPI Exploitation: On WhatsApp, the impersonator provided UPI details for an urgent payment to the "new vendor," stressing the criticality of immediate action for the partnership.
- Rapid Execution: The employee, convinced by the elaborate ruse and the perceived authority of the MD, transferred ₹75 lakhs (approximately $100,000) via UPI.
The scam was uncovered only when the real vendor inquired about the delayed payment a week later. The immediacy of UPI transactions and the difficulty in tracing the beneficiary made recovery of the funds nearly impossible.
Conclusion
Cross-platform CXO impersonation attacks, particularly those moving from email to WhatsApp, represent a significant and evolving threat in the global business landscape. The prevalence of attacks originating in email before transitioning to WhatsApp highlights the need for a holistic approach to communication security. The exploitation of publicly available information from professional databases adds another layer of sophistication to these attacks, making them increasingly difficult to detect.
By understanding these mechanics and implementing comprehensive, culturally-aware security strategies, businesses can better protect themselves against these sophisticated threats. Remember, in the world of multi-channel communication, vigilance must extend across all platforms, and verification is crucial – especially when dealing with urgent financial requests or when asked to switch communication channels.


Comments
Your comment has been submitted