Phishing-As-A-Service Meets AI - A New Frontier in Email Security
Introduction
In the rapidly evolving landscape of cybersecurity, Phishing-as-a-Service (PhaaS) has emerged as a game-changing phenomenon. As businesses and individuals become more aware of traditional phishing techniques, cybercriminals have adapted, leveraging artificial intelligence (AI) to streamline and scale their malicious activities. This blog delves into the world of AI-enhanced phishing, exploring how it's revolutionizing the speed and effectiveness of phishing campaigns, reducing launch times from 21 hours to just 15 minutes.
At RavenMail Security we have demonstrated the use of Phishing Kits to simulate a CrowdStrike campaign.
What is Phishing-as-a-Service: The Playstore for Threat Actors

PhaaS is a model where cybercriminals offer phishing tools, infrastructure, and expertise as a service to other malicious actors. This model has made it easier for less technically skilled individuals to launch sophisticated phishing campaigns. Essentially, PhaaS operates like a "one-stop-shop" for launching phishing attacks, providing everything from phishing kits to hosting services.
Key Components of PhaaS
- Phishing Kits: Pre-designed templates that mimic legitimate websites
- Infrastructure: Domains, email servers, and hosting services
- Customization Options: Tools to tailor phishing emails and websites to specific targets
- Support and Training: Assistance and advice for setting up and running phishing operations
Popular Phishing Kits and Their Features
PhaaS & Phish-Kits are often available on Dark Web marketplaces. These kits are sold with everything needed to execute a phishing attack, including ready-to-use email templates and fake login pages. Here are some popular kits with their features
- "16Shop" Phishing Kit
- Targets multiple brands including Apple, Amazon, and PayPal
- Includes mobile-responsive phishing pages
- Anti-bot and anti-spam protection to evade detection
- "HiddenEye" Open-Source Phishing Kit
- Supports over 30 website templates including social media and banking sites
- Keylogger functionality to capture keystrokes
- IP address and location tracking of victims
- "Modlishka" Reverse Proxy Phishing Tool
- Capable of bypassing two-factor authentication (2FA)
- Real-time traffic flow monitoring and modification
- Automatic SSL/TLS certificate generation
- "SocialFish" Social Media Phishing Kit
- Focuses on social media platforms like Facebook, Twitter, and LinkedIn
- Includes URL shortener to disguise phishing links
- Email template generator for spear-phishing campaigns
- "Gophish" Open-Source Phishing Framework
- User-friendly web interface for campaign management
- Customizable email and landing page templates
- Detailed campaign analytics and reporting
- "Evilginx" Advanced Phishing Framework
- Specialized in capturing login credentials and session cookies
- Uses a reverse proxy to intercept and modify traffic in real-time
- Capable of bypassing multi-factor authentication
- Customizable phishing templates for various popular services
- "Phoenix" Phishing Kit
- Targets financial institutions with high-fidelity website clones
- User-friendly interface for creating and managing phishing campaigns
- Advanced evasion techniques to bypass security measures
- Customizable features allowing for tailored attacks
- Available on multiple dark web forums, indicating widespread use
How Attackers Sell Their Services
Attackers sell Phishing-as-a-Service (PhaaS) on dark web marketplaces, offering cybercriminals a turnkey solution for launching sophisticated phishing campaigns. These services typically include customizable phishing kits, hosting infrastructure, and ongoing support. Vendors showcase their products with detailed descriptions, screenshots, and sometimes video demonstrations.
Pricing models vary, ranging from one-time purchases to subscription-based services. To build trust, sellers often offer money-back guarantees or free trials. Payment is usually accepted in cryptocurrencies to ensure anonymity. Some advanced PhaaS providers even offer tiered services, AI-powered features, and regular updates to evade the latest security measures.
This commoditization of phishing tools on the dark web has significantly lowered the barrier to entry for cybercrime, making it accessible even to those with limited technical skills.
Here are some real examples found by our threat researchers
1. Customised panels delivered in 1hr
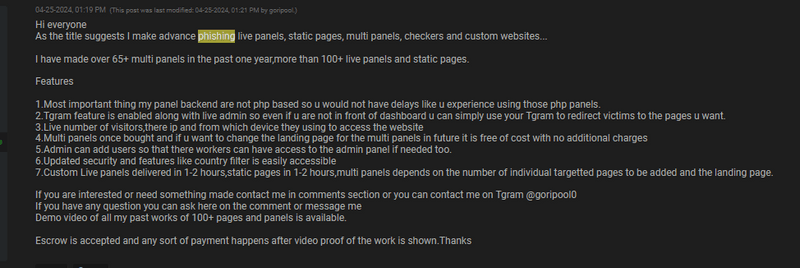
2. Banks available for targets
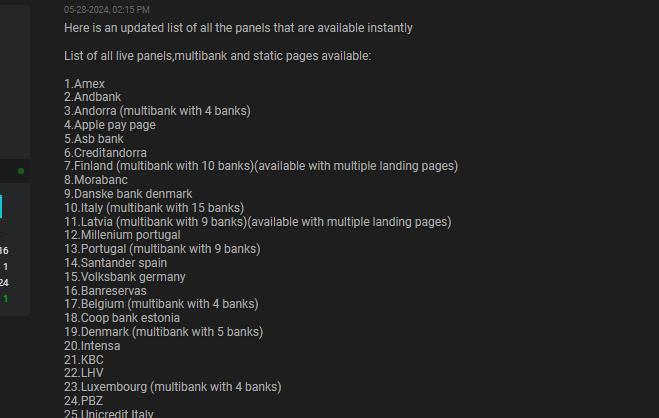
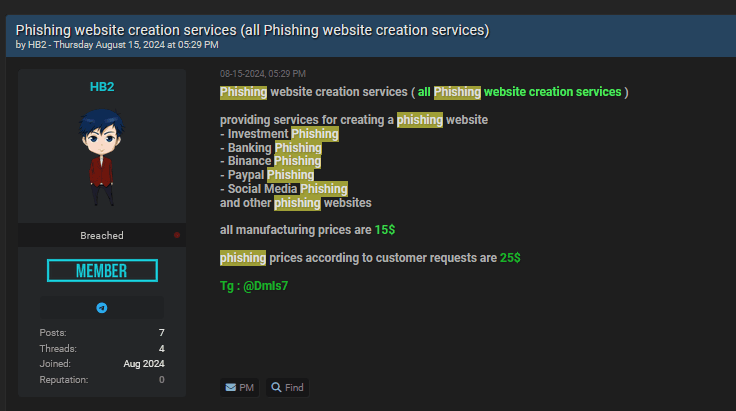
3. Sector-wise phishing website creation services
Alarming Statistics of how AI has Enhanced Phishing-As-A-Service
- The average time to launch a campaign from 21 hours to just 15 minutes - a 97% reduction.
- AI-driven phishing campaigns can generate and send up to 10,000 personalized emails per hour, compared to the previous average of 200 emails per day using manual methods.
- AI-enhanced phishing emails have a 40% higher click-through rate compared to traditional phishing attempts, due to improved personalization and timing.
- AI-powered phishing campaigns can now adapt to new security measures within 30 minutes of deployment, compared to the previous average of 48 hours.
- AI-driven phishing kits can perform A/B testing on hundreds of email variations in under an hour, a process that previously took days or weeks.
- AI-powered security systems have reduced the average time to detect a phishing campaign from 24 hours to 30 minutes.
Conclusion: Approach to Mail Security Needs to Shift to AI-Native Solutions
The rise of AI-enhanced phishing has dramatically shifted the cybersecurity landscape, reducing campaign launch times from 21 hours to just 15 minutes. This acceleration, coupled with increased sophistication and scale, poses unprecedented challenges that traditional email security measures are ill-equipped to handle.
Legacy systems, designed for conventional phishing methods, are overwhelmed by the volume, speed, and adaptability of modern attacks. Rule-based detection, static blacklists, and signature-based antivirus software prove increasingly ineffective against AI-generated phishing content that evolves in real-time. The rapid iteration and learning capabilities of AI systems allow attackers to deploy new variations almost instantly when one attack vector is blocked.
Organizations must recognize that conventional approaches are no longer sufficient. The future of digital security depends on harnessing AI not just as a weapon, but as a shield. This requires a fundamental shift towards dynamic, AI-driven defense systems that can adapt and respond in real-time to emerging threats.
The arms race between AI-enhanced phishing and AI-driven defense will define the cybersecurity landscape for years to come. Only by embracing advanced, AI-powered security solutions can businesses hope to protect their digital assets in this new era of AI-accelerated threats.


Comments
Your comment has been submitted