How the 'CrowdStrike episode' exposes the gaps in email security

This long-form has been authored by our Red Team members at RavenMail. The use of logos and brand names are meant for educational purposes only.
It's been a busy week at the RavenMail HQ where our Red Teams were unpacking the possible fallout of the CrowdStrike episode. Given the size of the impact, it is very lucrative for any Threat Actor (TA) to take advantage of the situation.
Anyone in the business of email security should have seen what's about to be unleashed. Hours after the incident, James Spiteri of whichphish.com released a list of 200 URLs that can be potentially used for malicious purposes.
We will delve into the details of the CrowdStrike event exploring how threat actors have manipulated the scenario to target unsuspecting users and why email security products failed to protect from such attacks.
The CrowdStrike Incident: A Brief Overview
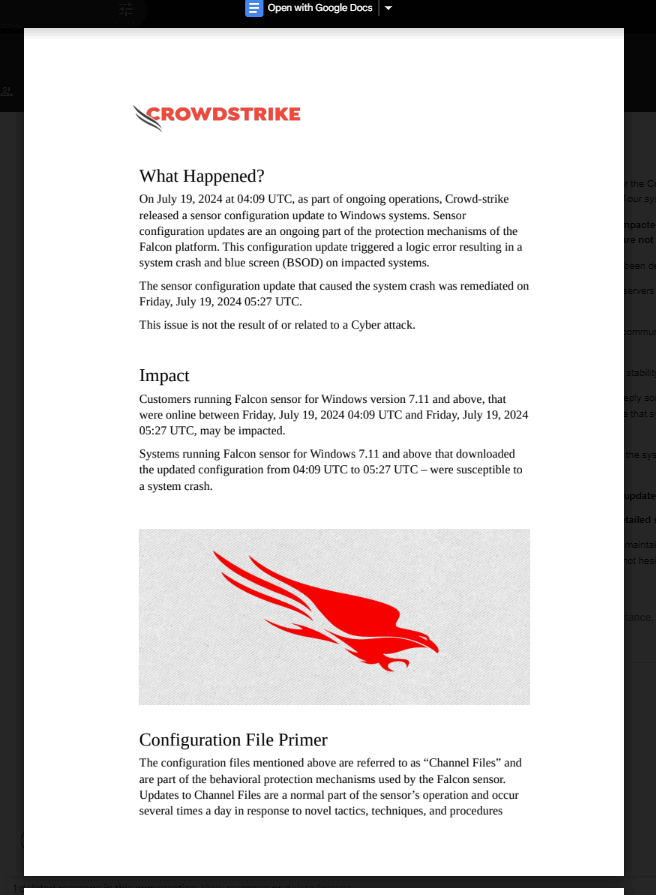
On July 19, 2024, CrowdStrike, a leading cybersecurity firm, encountered an issue where a sensor configuration update of their Falcon Platform triggered a system crash, leading to a Blue Screen of Death (BSOD) on affected Windows systems.
The update, aimed at enhancing the Falcon platform's protection mechanisms, inadvertently introduced a logic error causing the disruption. Although swiftly rectified within a couple of hours, this incident garnered significant attention across the cybersecurity community.
Malicious Actors' Exploitation Tactics
Taking advantage of the widespread concern and urgency surrounding the CrowdStrike incident, Threat Actors (TA) devised various email phishing schemes to exploit the situation. Here’s a breakdown of some prevalent tactics observed:
1. Impersonation of CrowdStrike
Phishers often masquerade as trusted entities to lure victims into their traps. In this case, emails purportedly from CrowdStrike support teams were crafted to appear legitimate. These emails typically contained urgent calls to action, such as:
- Fake Security Alerts: Emails warning recipients of the BSOD issue and urging them to download and apply a "critical patch" via an attached file or link.
- Update Notifications: Messages claiming to provide official updates or additional information on the incident, directing users to malicious websites designed to steal credentials or deliver malware.
2. Spoofed Internal Communications
- Attackers also simulated internal company communications, targeting employees of organizations known to use CrowdStrike services. Examples include:
- IT Department Memos: Phishing emails mimicking internal IT department notices, instructing employees to update their systems or verify their credentials to ensure protection against the reported issue.
- Executive Directives: Spoofed emails appearing to come from company executives, emphasizing the urgency of the situation and directing staff to follow specific steps to mitigate the risk.
3. Social Engineering Attacks
Social engineering remains a cornerstone of effective phishing campaigns. In the context of the CrowdStrike incident, attackers leveraged psychological manipulation, including:
- Fear and Urgency: Crafting messages that instill fear about the potential impact of the BSOD issue, prompting immediate, often irrational responses from recipients.
- Technical Jargon: Using complex technical language to create an illusion of authority and legitimacy, convincing recipients that the instructions are credible and must be followed without question.
Examples of Phishing Emails
Below are some examples (only body content) of the phishing emails observed during this period:
- Fake Security Alert:
Subject: URGENT: Apply Critical Patch to Avoid System Crash
Dear User,
Due to a recent update issue with CrowdStrike, we have identified a critical vulnerability that could cause your system to crash. Please download and apply the patch from the link below immediately to secure your system.
[Download Patch]
Regards,
CrowdStrike Support Team
2. IT Department memo:
Subject: Immediate Action Required: System Update
Attention All Staff,
Our security team has been alerted to an issue with CrowdStrike's recent update. Please visit the following link to verify your system's status and apply necessary updates.
[Verify System]
Thank you,
IT Department
3. Executive Directive
Subject: Important Security Update from CrowdStrike
Dear Team,
In light of the recent CrowdStrike incident, it is imperative that all employees update their systems to prevent any potential disruptions. Follow the instructions in the attached document to complete the update process.
Regards,
[Executive Name]
How we simulated the scenario and were able to compromise accounts
The approach
- Victim or employee receives the email
- Victim/employee should be convinced that the email is legit
- Should download the pdf file which contains the instructions to update the patch
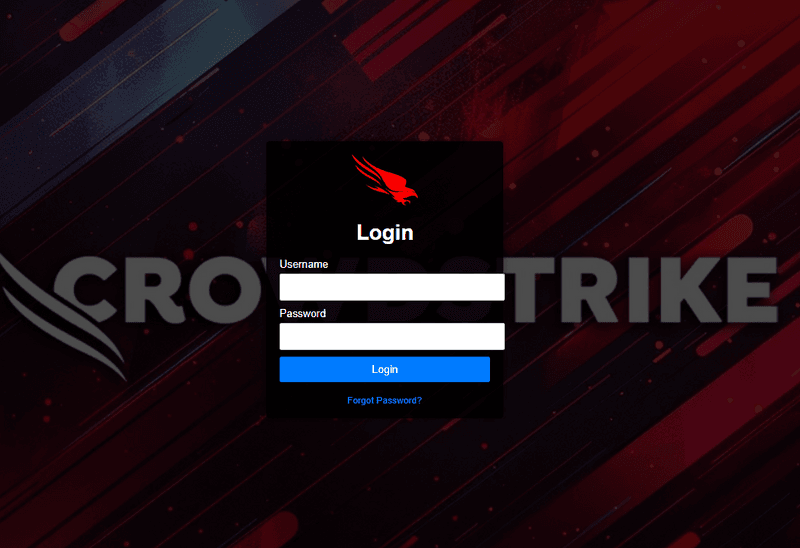
- A download link is present in the pdf file which takes the victim to the Malicious or Fake login portal with Cloudflare’s JavaScript protection making it look more legit.
- The credentials and the session of the user are captured, which will be used for other scenarios.
Setting up the phish infra
For the Phishing simulation to be successful we need a domain which is similar to Crowd strike. Example domain names which are used for phishing link, set up sub-domains that look like support teams.
- We acquired domains via
- Name cheap
- GoDaddy
- We acquired VPS via
- Digital Ocean
- AWS
- Azure
- We set up web mailing service via
- Mail gun
- SendGrid
- Use basic developer capabilities for
- SSL certs
- Code Signing
- Phish kits from Evilgink
- Content generated by ChatGPT
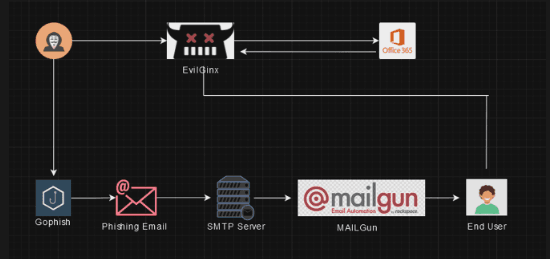
Obfuscating the phishing infrastructure hosting
Directly hosted servers are ideal for vulnerability screening and blacklisting because they can be easily identified by defense monitoring systems (e.g., VirusTotal). Automated scanning programs that analyze traffic patterns to and from these servers can reveal malicious activity and the nature of the operations.
Setting up redirectors are necessary to mask our infrastructure's IP addresses so it could not be easily traced and making it anonymous.
To improve chances of success on Social Engineering engagements, we protected our Evilginx server from being marked as dishonest by combining Cloudflare and HTML Obfuscation.
The warning 'Deceptive site ahead' is a common sight for anyone who has attempted to run a Social Engineering campaign.
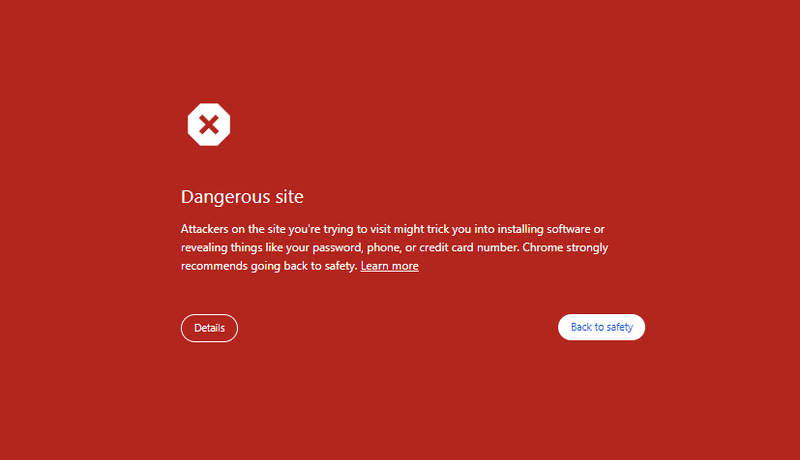
We set up Cloudflare in under attack mode and bot fight mode so we get a temporary protection which prevents our domain from getting blacklisted or marking the domain as dangerous site [deceptive site ahead].
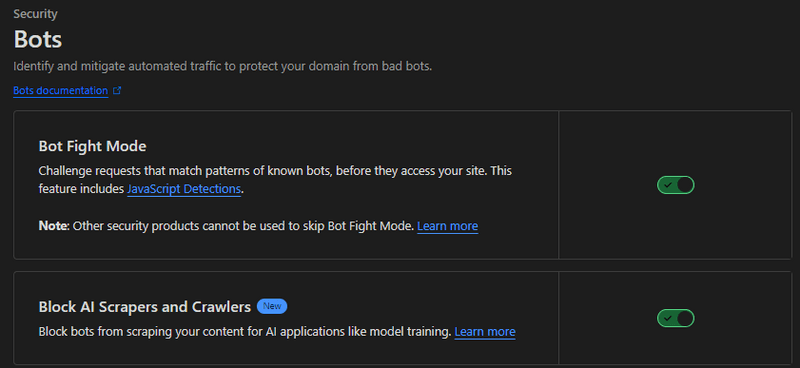
Geo Blocking link scanners
This is another effective way to block the web scrappers and link scanners that could happen across your infrastructure is restricting access by the geographical location.
Below is a sample screen shot that shows how many unauthorized request that are trying to access the domain and getting blocked by the rule.
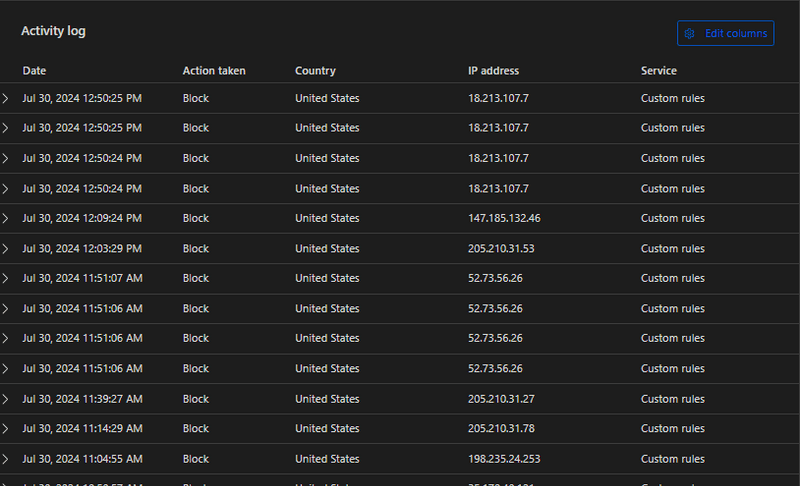
Using Java script Challenge when ever a user visits the domain or our malicious link. Below is the sample image showing the interactive challenge.
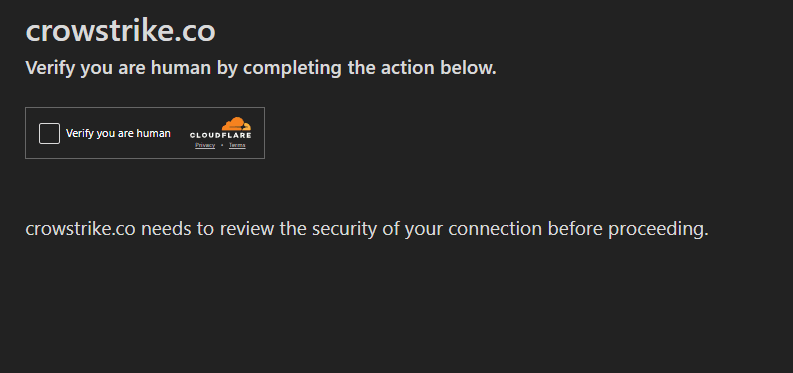
On successful interaction with the challenge, the users or victim is then redirected to the malicious link where the landing page is hosted.
Enhancing email delivery with MailGun and Gophish:
We used a robust email service that provides reliable delivery for bulk emails and SMTP credentials for sending an email.
With the help of Gophish and Mailgun and some configs we can send the email to our victim’s inbox which basically reduces the pain in creating our own SMTP servers.
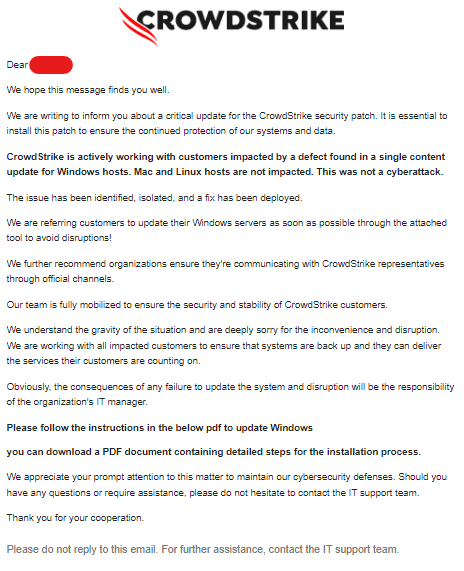
Below is the sample of the phishing email sender and the convincing email template generated by ChatGPT
Dear employee,
We hope this message finds you well.
We are writing to inform you about a critical update for the CrowdStrike security patch. It is essential to install this patch to ensure the continued protection of our systems and data.
CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts. Mac and Linux hosts are not impacted. This was not a cyberattack.
The issue has been identified, isolated, and a fix has been deployed.
We are referring customers to update their Windows servers as soon as possible through the attached tool to avoid disruptions!
We further recommend organizations ensure they're communicating with CrowdStrike representatives through official channels.
Our team is fully mobilized to ensure the security and stability of CrowdStrike customers.
We understand the gravity of the situation and are deeply sorry for the inconvenience and disruption.
We are working with all impacted customers to ensure that systems are back up and they can deliver
the services their customers are counting on.
Obviously, the consequences of any failure to update the system and disruption will be the responsibility
of the organization's IT manager.
Please follow the instructions in the below pdf to update Windows
you can download a PDF document containing detailed steps for the installation process.
We appreciate your prompt attention to this matter to maintain our cybersecurity defenses. Should you
have any questions or require assistance, please do not hesitate to contact the IT support team.
Thank you for your cooperation.
Please do not reply to this email. For further assistance, contact the IT support team.
The execution
Email Subject &Sender Name
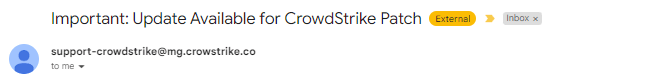
Email Body
Attachment Overview
Attachment Content
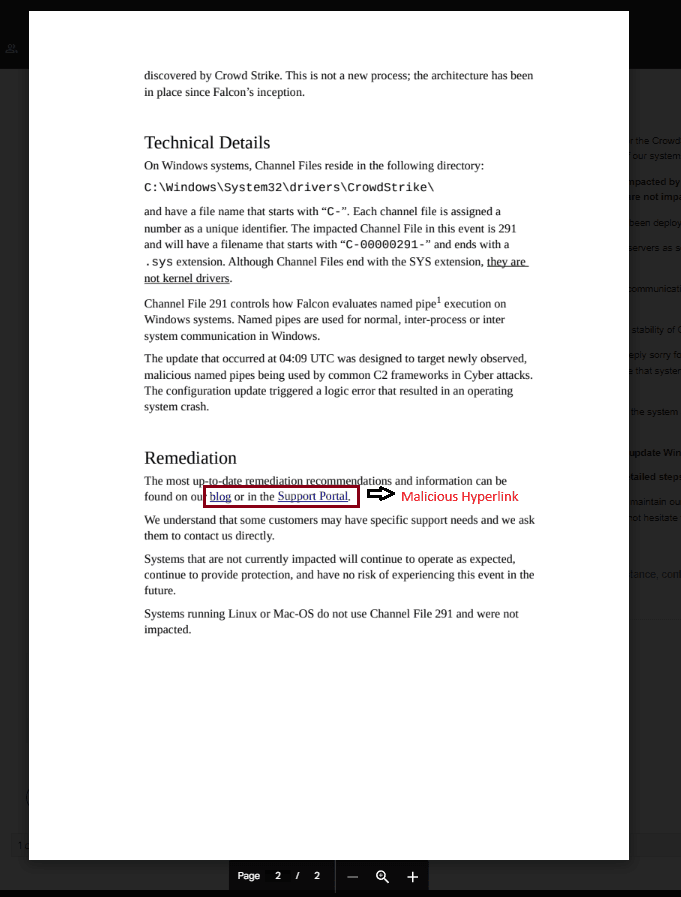
The Result
With this we were able to directly land in the user's inbox across Google Workspace & M365 using 3P email security layers. We used all attack vectors in this campaign and still landed in the users inbox.
- Sender reputation & infra scanning
- Spoof a look-like domain of a major security company
- Able to convincingly write mails in context to what's happening across the world
- Pass attachment scanners
- Pass URL scanning within attachment
In Part 2 we will deep dive on the why some emails get past the security engines and why we need to rethink email security from first principles
Comments
Your comment has been submitted