How a phishing email disrupted the UPI & ATM services in India
Background
On 31 July 2024, the National Payments Council of India (NPCI) issued a press release about a possible ransomware attack on a TSP (Technology Service Provider) serving over 300 banks in India, impacting UPI and ATM services for retail customers.

It was prudent of NPCI to isolate the TSP's processor and proactively issue a statement, thereby averting a major issue. There was extensive coverage in mainstream media, which you can read about here, here & here . The forensics, led by CloudSEK , indicated that the attack on Brontoo Technology Solutions was traced to the RansomEXX group
India's leading cybersecurity advisory body, CERT-In, issued a vulnerability note seven days later.
Top 10 Things About the RansomEXX (aka Defray777) Group
- They have been active since 2018, usually targeting high-profile government institutions, healthcare, telecom, and banking sectors.
- They are known to target victims through spear-phishing emails, using stolen credentials of exposed applications.
- In 2021, they launched a newer variant to expand their footprint from Windows to Linux-based servers
- They specialize in using "In-Memory" or "Fileless" execution methods to evade traditional screening and forensic techniques.
- They are known to extract passwords, tokens, secrets from in-memory - using tools like Mimikatz
- They add a personal touch to their ransom notes and artifacts.
- They use advanced encryption techniques like RSA-4096 to encrypt payload keys (it takes 4-14 years to crack this!).
- Their version 1 exploited macros in Microsoft Office documents that downloaded a trojan to run its malicious DLL.
- They targeted a legal firm with a malicious payload delivered via a steganography technique embedded in a PNG file.
- The latest attack on banking infrastructure in India targeted an exploit in the Jenkins server. The access to the server could have been sold by an IntelBroker or acquired through a payload delivered via a phishing email.
How Attackers Gained Access to the Jenkins Server via an Attachment
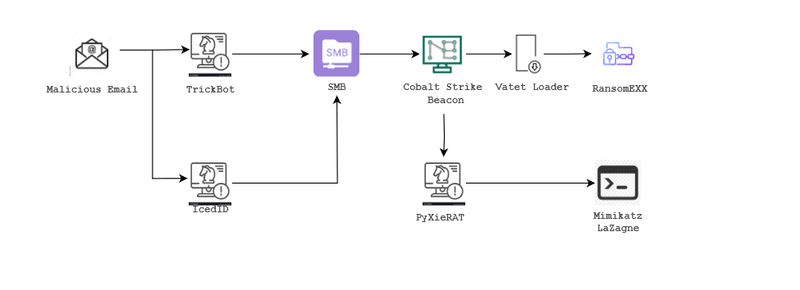
The RansomEXX attack on the Jenkins server likely began with a carefully crafted phishing campaign. Attackers sent emails to targeted individuals within the organization, particularly those who had access to critical systems or administrative privileges.
The email appeared to come from a trusted source, perhaps a colleague or a known business partner. It contained an urgent message designed to elicit a quick response, such as an invoice that needed immediate attention or a security alert that required action.
The email included an attachment, often a document such as a Word file, PDF, or Excel spreadsheet. The document contained a malicious macro or embedded script.
The Role of Email in RansomEXX Attacks
Emails are a critical vector in the initial stages of RansomEXX attacks. Here’s how email plays a role:
- Phishing Emails: Attackers craft phishing emails that appear to come from trusted sources, such as colleagues, partners, or well-known companies. These emails often contain urgent messages that prompt the recipient to click on a link or open an attachment.
- Malicious Attachments: The attachments may be disguised as legitimate documents (e.g., invoices, reports) but contain malicious macros or embedded scripts that execute the ransomware upon opening.
- Malicious Links: Links within the email may direct the recipient to a compromised website or a website designed to look legitimate. These sites can host exploit kits or prompt the download of a malicious file.
- Spear Phishing: More targeted phishing emails, known as spear phishing, are directed at specific individuals within the organization, often those with higher levels of access or authority, making them more effective.
Possible Connection with the Income Tax Filing Season
July happens to be the month of income tax filing for employees. This situation has been exploited in the past by the use of Microsoft Word documents with macros that unleash the Trojan.W97M.CVE202140444.A or TrojanSpy.Win32.ICEDID.BP in Windows systems (e.g., reference file name used: Income_tax_and_benefit_return.docx).
Once the recipient opened the attachment, the embedded malicious code was executed, leading to macro execution and payload delivery.
Gaining Access to Jenkins
With the initial payload delivered and executed, the attackers gained a foothold in the network. They used this access to move laterally and escalate their privileges until they reached the Jenkins server. With access to Jenkins, the attackers deployed the RansomEXX ransomware.
Jenkins' role as an automation server made it an ideal platform to distribute the ransomware payload quickly and effectively across the organization’s infrastructure.
The ransomware was executed, encrypting critical files and systems connected to Jenkins. This caused widespread disruption, as automated build and deployment pipelines were halted, and encrypted data became inaccessible.
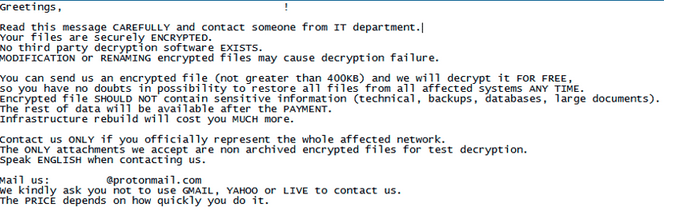
The attack culminated in the display of a ransom note, demanding payment in cryptocurrency in exchange for the decryption keys. The note often included threats of data leakage if the ransom was not paid, adding pressure on the organization to comply.
Conclusion
The RansomEXX attack is a stark reminder of the evolving threat landscape in cybersecurity. Organizations must be proactive in their defense strategies, including regular employee training on recognizing phishing attempts, implementing robust security protocols, and having an incident response plan in place. By understanding the tactics used by attackers and maintaining vigilance, organizations can better protect themselves from the devastating impacts of ransomware.
Comments
Your comment has been submitted