Attack Demo: How attackers can read inbox contents without getting inside
You read that right, you don't need to log inside your inbox to read the contents. There are ways for attackers to snoop what's happening on your account without being detected.
In this blog we want to show how this is done and address the following questions with a demo
- What can the attacker do once they gain an initial access of the admin?
- How the attackers can understand the context of the organisation before launching a targeted attack (similar to the Jenkin's server attack on Indian payment systems)
- How do attackers exfiltrate sensitive documents as part of corporate espionage or to be sold in dark web?
Reconnaissance Activities
Attackers often gather information before finalising the right method to infiltrate the organisation. According to MITRE Framework, Reconnaissance (TA0043) involves methods where adversaries actively or passively collect information that can assist in their targeting efforts. This data may include specifics about the victim's organization, infrastructure, or personnel. Adversaries can use this information to facilitate other stages of their attack lifecycle, such as planning and executing Initial Access, prioritizing goals after a compromise, or guiding further Reconnaissance activities.
The following scenarios are used in the reconnaissance phase using email as an entry point
- Understand who are the key personnel - admins, CXOs, finance team IDs
- Understanding the tooling ecosystem - SaaS, Infra, Security
- Monitor vendor payment cycles, bank accounts details
- Search for sensitive information - passwords, documents, keys
Overview of the demo
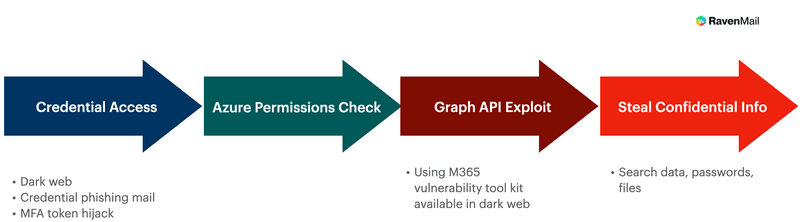
In this flow, we start with find credentials or sessions sold in dark web and using that how to use off-the shelf tools like Graph Runner to steal confidential info.
Graph Runner Capabilities Used
Source: https://github.com/dafthack/GraphRunner
- Search and export email.- RNC240816087451
- Search and export SharePoint and OneDrive files accessible to a user
- Search all Teams chats and channels visible to the user and export full conversations
- Deploy malicious apps
- Discover misconfigured mailboxes that are exposed
- Clone security groups to carry out watering hole attacks
- Find groups that can be modified directly by your user or where membership rules can be abused to gain access
- Search all user attributes for specific terms
- Leverage a GUI built on the Graph API to pillage a user's account
- Dump conditional access policies
- Dump app registrations and external apps including consent and scope to identify potentially malicious apps
- Tools to complete OAuth flow during consent grant attacks
- GraphRunner doesn't rely on any third-party libraries or modules
- Continuously refresh your token package
Attack demo using Graph Runner
How to detect these of attacks?
This attack vector completely sits outside email security filters in the traditional sense, the following detection logics can be used at the IAM layer and the mail security layer to discover these attacks.
- Auto-fowarding logic
- Privilege escalation
- Mail send & immediate sent mail deletion alert
- Dark web monitoring alerts
Comments
Your comment has been submitted