Attack Demo #2: System Take Over Using a Single Mail
Phishing to Pwnage: Our Journey Through a Cybercriminal's Playbook
At RavenMail, we've seen it all - from simple phishing attempts to full-blown system compromises. Today, we're taking you on a journey where are showing you how a single email can lead to a complete system takeover. To understand the demo (in the sections below), read through the blog to get the full context.
Crafting the Perfect Bait: The Phishing Email
It all starts with a well-crafted email. We've observed attackers putting significant effort into making these emails look legitimate (in our demo case it an AWS Invoice). They're not just throwing darts in the dark; they're studying their targets, using social engineering to create the perfect lure.
- Spoofed Email Addresses: Attackers often disguise their email addresses to mimic trusted sources.
- Fake Domains: We've seen domains that look strikingly similar to real ones. A slight change like "example.co" instead of "example.com" can easily go unnoticed.
- Malicious Attachments or Links: These are the payload delivery mechanisms. Attackers embed malicious attachments or links, often disguised as urgent documents.
Slipping Past the Guards: Email Delivery
Once the email is crafted, it needs to land in the target's inbox. We've observed several techniques attackers use to bypass security systems:
- Bypassing Spam Filters: Attackers use spear-phishing techniques, carefully crafting emails to avoid raising red flags.
- Email Authentication Manipulation: We've seen attackers exploit weak DMARC and SPF configurations to make their emails appear more trustworthy.
The Moment of Truth: Initial Interaction
This is where the victim either falls for the trap or spots it. If they click a malicious link or open an infected attachment, the attack chain begins.
The Real Attack Begins: Malware Execution and Shellcode
Once the phishing email has served its purpose, the real attack kicks off:
- Deploying Shellcode: This small piece of code executes a larger payload, often downloading more complex malware in the background.
- Second-stage Payload: This could be ransomware or a Remote Access Trojan (RAT).
Digging Deeper: Privilege Escalation and Lateral Movement
With a foothold in the system, attackers typically try to increase their level of access and spread to other systems in the network.
The Grand Finale: Exfiltration and Persistence
Assuming full control, attackers aim to steal data and ensure long-term access to the network:
- Establishing Persistence: Attackers create mechanisms to maintain access, even after system reboots.
- Data Exfiltration: Valuable information is siphoned off, often encrypted to avoid detection.
Attack Demo
We've created a demo of how an endpoint can be compromised with a single email attachment. For infrastructure details, check out our blog post on the CrowdStrike phishing email incident.
In our demo, we use a custom script to send an email with a tailored SMTP profile and custom headers. This approach helps ensure the email lands in the victim's inbox and once the attachment is opened it establishes a connection with the C2 server.
Note: Our demo uses proof-of-concept attacks in a controlled environment and does not replicate actual ransomware or malware.
MITRE ATT&CK Framework Mapping
To help you better understand how this attack chain aligns with known cyber attack patterns, we've mapped each stage to the MITRE ATT&CK framework. This mapping provides valuable insights into the tactics and techniques used by attackers, which can inform your defensive strategies.
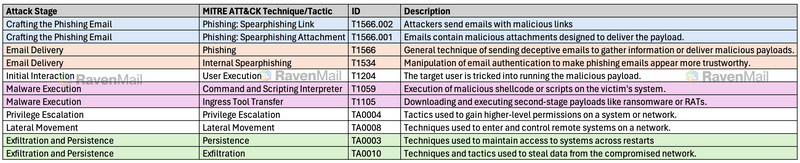
By understanding these mappings, we can develop more targeted and effective defense strategies. Each technique in the MITRE ATT&CK framework has associated mitigations and detection methods, which can guide our cybersecurity efforts.
Remember, staying informed about these tactics and continuously updating our defenses is crucial in the ever-evolving landscape of cybersecurity threats.
Stay vigilant, and stay secure!
As we say, It all begins with an email
P.S: Something's new coming, check out our new product launch by clicking the banner below

Comments
Your comment has been submitted