CEO Impersonation Fraud: A Case for Context-Aware Email Security
Introduction
In an era where digital communication reigns supreme, email remains a critical tool for business operations. However, it's also become a prime vector for sophisticated cyberattacks (see demo here), with CEO impersonation scams emerging as a particularly costly threat. Despite advances in email security, many organizations find themselves vulnerable to these attacks. The question is: why do traditional email security measures fall short, and what's missing from our defensive strategies?
Understanding CEO Impersonation Scams
CEO impersonation scams, also known as "whaling" or "business email compromise" (BEC) attacks, involve cybercriminals posing as company executives to trick employees into transferring funds or sharing sensitive information. These scams are alarmingly effective, with the FBI reporting that BEC attacks caused over $2.4 billion in losses in 2021 alone.
Case Studies
Let's delve into some high-profile cases that illustrate the sophistication and impact of these attacks:
- FACC AG (2016): This Austrian aerospace parts manufacturer lost a staggering €50 million ($54 million) when scammers impersonated the CEO in emails to the finance department. The attackers crafted convincing emails requesting urgent wire transfers for a supposed acquisition project. The scam was so convincing that it went undetected until after multiple transfers had been made. The fallout was severe: both the CEO and CFO were fired, and the company filed a lawsuit against its auditors.
- Ubiquiti Networks (2015): The U.S.-based tech company specializing in networking technology fell victim to a $46.7 million scam. In this case, the attackers went a step further – they not only impersonated executives but also posed as employees from the company's outside legal counsel. This dual impersonation lent additional credibility to the fraudulent requests, convincing the finance department to make several transfers to overseas accounts. Ubiquiti managed to recover $8.1 million, but still suffered a net loss of $38.6 million.
- Crelan Bank (2016): This Belgian bank became the victim of one of the largest reported CEO fraud cases in Europe, losing €70 million ($75.8 million). The attack involved sophisticated social engineering tactics to impersonate top executives. While details remain limited due to ongoing investigations, the scale of the loss highlights the potential impact of these scams on financial institutions.
- Toyota Boshoku Corporation (2019): The Japanese car parts manufacturer (a member of the Toyota Group) lost $37 million to a BEC attack. In this case, the scammers posed as business partners rather than company executives. They managed to convince an employee to change payment directions for a legitimate transaction, showcasing how these attacks can exploit vulnerabilities in supply chain and vendor relationships.
- Facebook and Google Wire Fraud (2013-2015): Even tech giants aren't immune to these scams. Over a two-year period, Lithuanian national Evaldas Rimasauskas orchestrated an elaborate scheme that defrauded Google of $23 million and Facebook of $98 million. Rimasauskas impersonated Quanta Computer, a legitimate Asian hardware manufacturer that both tech companies regularly did business with. He sent fake invoices and forged contracts, complete with falsified corporate stamps, to add authenticity to his requests. The scheme's longevity – running for two years before detection – highlights how convincing these scams can be. Rimasauskas was eventually arrested in 2017, extradited to the U.S., and sentenced to 5 years in prison.
- Nikkei (2019): The Japanese media company Nikkei fell victim to a BEC scam that cost them $29 million. An employee of Nikkei's U.S. subsidiary was tricked into transferring the money to a bank account purportedly belonging to a business partner. The scammer impersonated a Nikkei management executive, showcasing how these attacks often exploit the hierarchical nature of corporations.
- Pathé (2018): The French cinema company lost over €19 million ($21.5 million) to a BEC scam. Scammers impersonating the company's CEO convinced the CFO and another executive to make several large transfers for a supposed confidential acquisition. The company only discovered the fraud after the third transfer. Both executives were initially fired but later exonerated in court, highlighting the complex aftermath these scams can create within an organization.
These cases underscore several key points about CEO impersonation scams:
- Scale of financial damage: Losses range from tens to hundreds of millions of dollars.
- Vulnerability of large, tech-savvy companies: Even organizations with substantial cybersecurity resources can fall victim.
- Sophisticated methods: Attackers combine technical skills with social engineering, often conducting detailed research on their targets.
- Global nature of the threat: Companies worldwide are at risk, regardless of industry or location.
- Potential for reputation damage and leadership changes: These incidents can lead to firings, lawsuits, and significant corporate upheaval.
- Challenges in fund recovery and legal prosecution: While some funds may be recovered, companies often face substantial net losses, and bringing perpetrators to justice can be a complex, international effort.
As we can see from these examples, traditional email security measures often fail to prevent these attacks. In the next section, we'll explore why these measures fall short and identify the critical missing piece in most organizations' defenses.
Traditional Email Security Measures: Necessary But Not Sufficient
Most organizations rely on a standard set of email security tools:
- Spam filters to block unwanted bulk emails
- Antivirus software to detect malware
- Email authentication protocols like SPF, DKIM, and DMARC to verify sender domains
While these measures are essential for blocking a wide array of threats, they operate without specific organizational context. They can verify that an email comes from a legitimate domain, but they can't determine if the content of that email is appropriate or expected within the organization's normal operations.
The Critical Missing Piece: Organizational Context
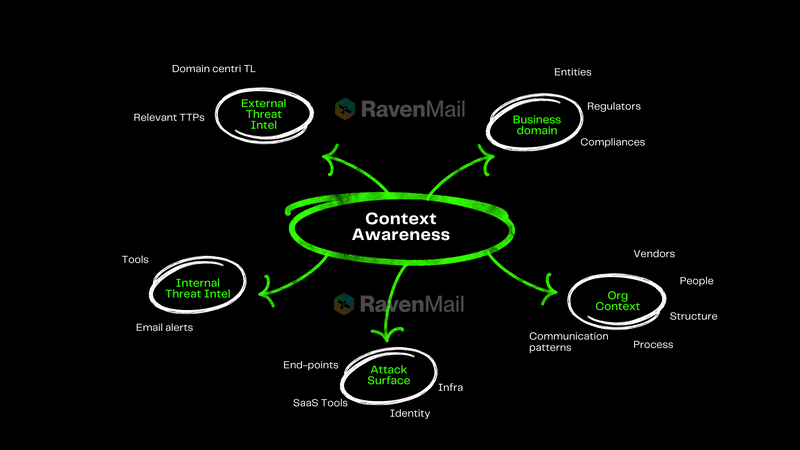
The key element that traditional email security lacks is organizational context. But what exactly does this mean?
Organizational context encompasses:
- Understanding of company structure, processes, and communication patterns
- Knowledge of key personnel and their roles
- Awareness of ongoing projects and typical financial transactions
- Understanding of internal & external threat landscape and intelligence
This context matters because it helps distinguish between legitimate and fraudulent requests, enables detection of anomalies in communication style or content, and allows for validation of unusual or high-stakes requests.
Consider the FACC case mentioned earlier. A system with proper organizational context would have flagged several anomalies:
- An unusual request for a large wire transfer
- An acquisition project that wasn't part of known company plans
- Potentially, a communication style that didn't match the CEO's typical emails
Why Traditional Methods Fall Short in Providing Context
Traditional email security methods focus primarily on technical indicators rather than content and context. They check for malware, bad links, or spoofed addresses, but not the appropriateness of the request itself. Here's why this approach is insufficient:
- Inability to understand communication patterns: They can't detect if a supposed CEO's email style differs from their norm.
- Lack of integration with business processes: There's no awareness of typical approval chains or transaction procedures.
- Absence of real-time learning and adaptation: These systems can't evolve with changing organizational dynamics.
- Over-reliance on predefined rules: Rigid rule sets can't account for the nuanced and evolving nature of business communications.
Conclusion
Traditional email security measures play a vital role in protecting organizations from a wide array of threats. However, their lack of organizational context leaves a critical gap that sophisticated attackers exploit through CEO impersonation scams.
By incorporating solutions and practices that account for the unique context of your organization — its structure, processes, and communication norms — you can significantly enhance your defenses against these costly attacks. Remember, in the world of email security, context isn't just helpful — it's essential.
Comments
Your comment has been submitted