Best Practices for Securing Group Email IDs in Google Workspace & M365
Setting up a group email ID like `[email protected]` or `[email protected]` is often the first step in improving team coordination and customer communication.
It’s quick, convenient, and built into both Google Workspace and Microsoft 365.
But here’s what most admins don’t realize:
These shared mailboxes can quietly open up serious vulnerabilities—making them a favorite target for phishing, impersonation, and vendor fraud.
Unlike individual accounts, group email addresses:
- Often accept mail from outside your domain by default
- Are monitored by multiple users, making accountability vague
- Frequently forward messages internally, breaking authentication checks
And rarely have the same security controls as standard inboxes
In this post, we’ll break down:
How attackers exploit misconfigured group IDs and distribution lists
The forwarding and self-signing quirks that weaken trust signals like SPF, DKIM, and DMARC
Real-world examples of group ID abuse across industries
And how to properly secure these shared inboxes before they become a liability
Let’s start by understanding why attackers love group mailboxes—and why your configuration choices matter more than you think.
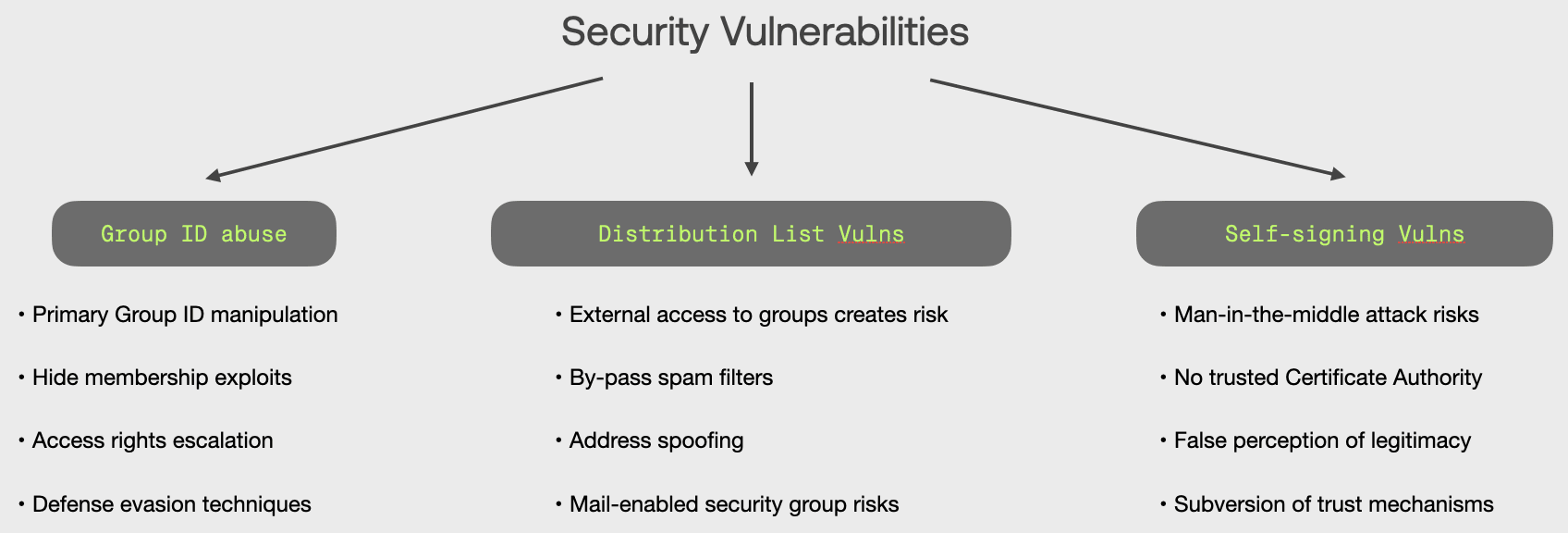
Why Group IDs Are a Goldmine for Attackers
Group IDs often:
Are publicly visible (on websites, WHOIS, vendor records)
Are monitored by multiple users—creating distributed responsibility
Accept external mail by default
Don’t enforce MFA or login hygiene (because they’re aliases, not inboxes)
That combination makes them ideal infiltration points—especially for impersonation, fraud, and credential harvesting.
Attack Vectors and Real-World Abuse Scenarios
1. Executive Impersonation to All-Hands Lists
Case: A mail from `[email protected]` (spoofed) to `[email protected]`:
“Quick request—can someone handle an urgent payment? Let’s chat on text.”
DMARC fails silently due to forwarding.
Appears internal, urgent, and credible.
One junior employee replies. Fraud chain begins.
2. Vendor Fraud via Payments Alias
Case: A spoofed `[email protected]` sends an invoice to `[email protected]` -“Please note our new bank details for this month’s settlement."
SPF/DKIM break due to forwarding.
Mail is routed internally with no red flags.
Funds are transferred to attacker-controlled account.
3. Credential Harvesting via IT Lists
Case: Phishing link sent to `[email protected]` claiming to be from IT. “Your Microsoft 365 password expires in 24 hours. Renew now.”
Group is monitored by rotating L1 staff.
Message is forwarded from ticketing system, breaking auth headers.
Phishing site collects real credentials.
4. Reconnaissance via Bounced Replies
Attackers send malformed emails to inactive or niche group IDs like
`vendor-onboarding@` They harvest:
NDRs (Non-delivery reports) for naming conventions
OOO replies for employee roles and tools
Auto-responses from connected systems
The Technical Quirk: Why Forwarding Breaks Email Trust
Security tools rely on three key protocols to verify sender legitimacy:
SPF: Validates the IP of the sender domain
DKIM: Cryptographic signature on the content
DMARC: Alignment and enforcement policy
But forwarding silently breaks this trust chain, let's understand the forwarding process in both Google & Microsoft
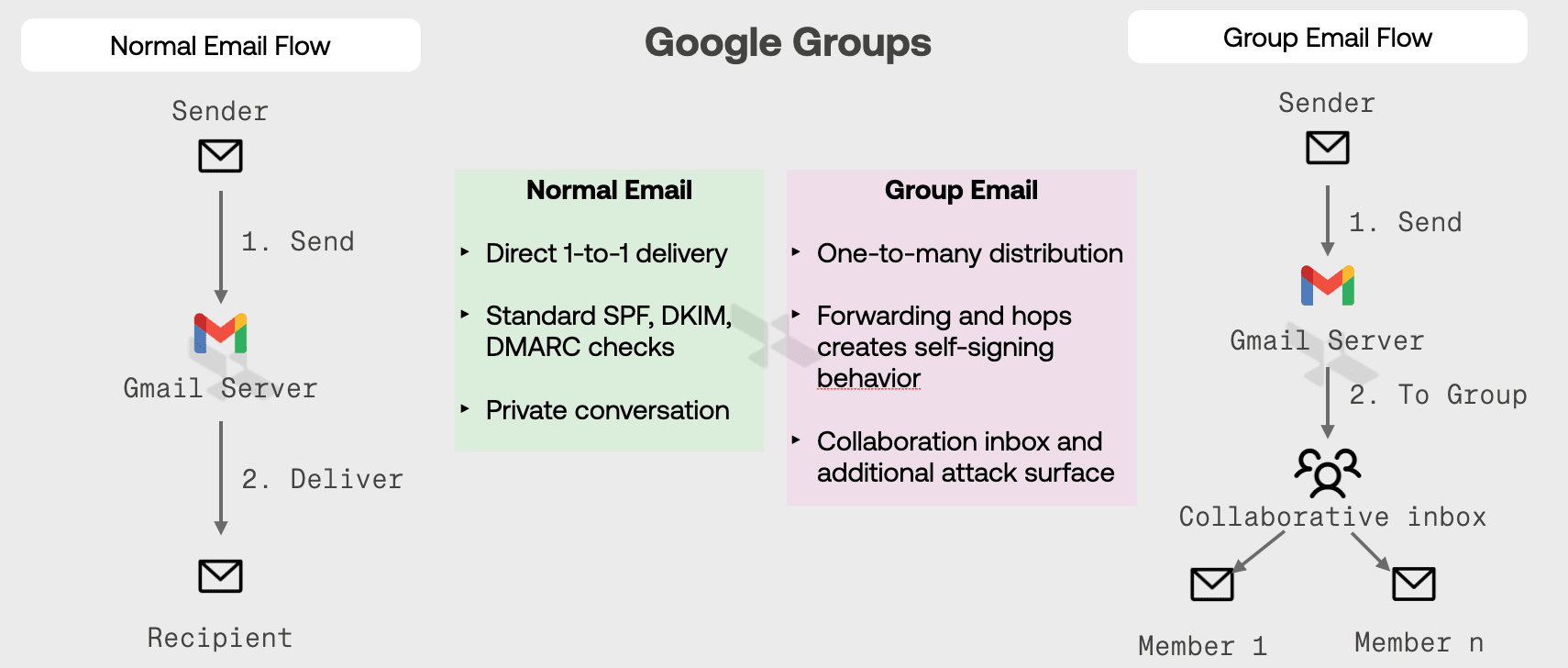
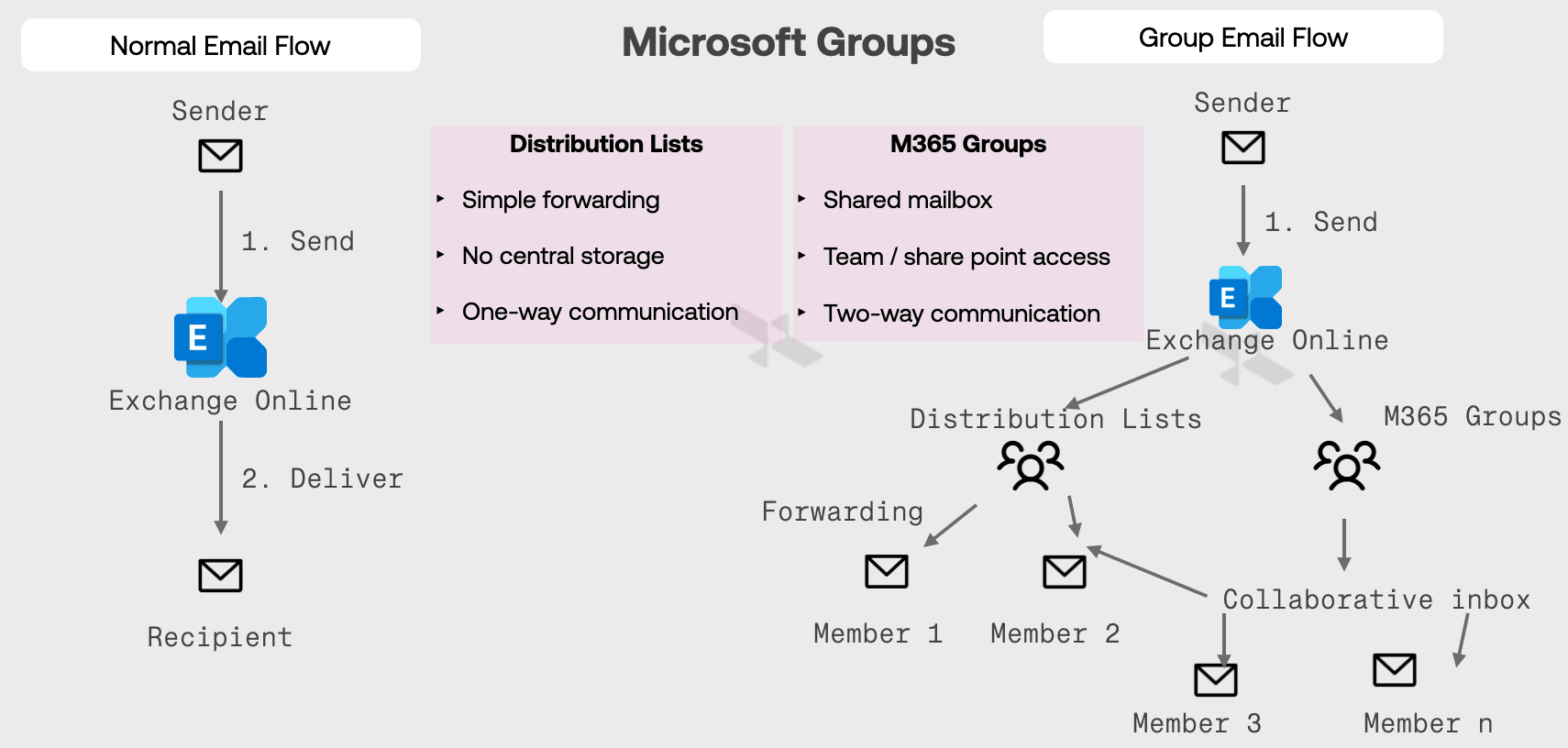
Email Type | SPF | DKIM | DMARC |
|---|---|---|---|
Direct mail | ✅ | ✅ | ✅ |
Forwarded via Group | ❌ | ❌ | ❌ |
Why this happens?
The group server becomes the new sender → SPF fails.
Any signature modification (e.g. banners, disclaimers) → DKIM breaks.
Without SPF or DKIM alignment → DMARC fails.
Yet, many tools treat these mails as “internal” simply because they’re from @company.com or routed internally. Attackers exploit this.
The “Self-Signed” Problem
Many internal tools (Jira, ticketing systems, bots) send from internal domains like '[email protected]' but without proper DKIM signatures or from external infra (e.g. AWS SES, Zapier).
This creates a false sense of legitimacy:
It looks internal.
But it’s not cryptographically verifiable.
It bypasses filters expecting signed or aligned headers.
Attackers mimic these patterns to slide through leading to many vulnerabilities.
Group ID Safe Configuration Practices Checklist
Disable External Mail by Default
Only enable external mail to group IDs when strictly needed. Whitelist trusted domains, not the internet.
Enforce ARC (Authenticated Received Chain)
ARC preserves authentication signals through forwarding, allowing downstream detection tools (like Raven) to evaluate origin risk accurately.
Sign All Outbound Mail with DKIM
This includes tools, bots, and internal notification systems. If they don’t support DKIM, route them through a domain-authenticated relay.
Block Catch-All Forwarding
Avoid configurations where all unknown or generic addresses forward to a shared team or person. It creates ambiguity, risk, and noise.
Monitor First-Time Senders
Raven flags when a group ID receives a mail from an unknown or first-time domain—especially if the request involves urgency, credentials, or money.
Apply Role-Aware Risk Scoring
Treat [email protected] and [email protected] differently. A spoofed mail to legal@ deserves higher scrutiny than a newsletter.
Final Word
Group emails are not just operational shortcuts. They are risk amplifiers if left unmonitored and misconfigured.
Attackers know they’re easy to reach and hard to police.
By addressing the forwarding flaws, enforcing modern email standards, and adopting adaptive detection tools, security teams can turn these backdoors into hardened front lines.
How Raven Detects Group ID Abuse Before It Spreads
At Raven, we treat group email IDs not just as shared inboxes—but as high-risk entities with outsized impact. Our platform continuously monitors who’s emailing these addresses, how those emails are routed, and whether the authentication signals survive forwarding. We use LLM-powered detection to flag unusual patterns—like a new sender spoofing a vendor to payments@, or a sudden spike in first-time contacts to legal@. Even when SPF, DKIM, or DMARC fail silently due to forwarding quirks, Raven traces header integrity, origin risk, and behavioral anomalies in real time. The result? Threats that would normally slip through group aliases are caught before they trigger a reply, a click, or a transfer.
Get a free 30-day trial with Raven by contacting us
Comments
Your comment has been submitted