[Feb 2026] How attackers are using Lovable for Multi-Stage Phishing Attacks
Vibe-Coding Platforms: The next frontier in phishing
Researchers at Ravenmail has discovered that attackers are no longer hosting phishing pages on obviously malicious infrastructure. Instead, they are abusing legitimate low-code and “vibe coding” platforms to build convincing, disposable redirectors that sit between the phishing email and the final credential-harvesting site.
In a recently observed campaign, attackers used Lovable, a popular vibe-coding platform, as a multi-stage routing layer to deliver Microsoft credential phishing pages - all while evading traditional email and URL defenses.
This blog breaks down how Lovable was used, why vibe-coding platforms are becoming the next phishing frontier, and what defenders must change to keep up.
The Evolution of Phishing Infrastructure
Phishing has evolved through several infrastructure phases:
What we are seeing now is Phishing-as-a-Service 2.0 — where attackers no longer care if their final phishing domain is burned. The email-visible URL is the asset, and that URL lives on a trusted platform.
What Is Vibe Coding and Why Attackers Love It
Vibe coding platforms (Lovable, Replit, Glide, etc.) are designed to:
Rapidly build functional web apps
Deploy instantly to shared domains
Abstract away infrastructure complexity
Encourage experimentation and iteration
From an attacker’s perspective, this provides:
Instant hosting
Implicit reputation trust
Fast rebuilds
No obvious “malicious” signals
In short: perfect phishing infrastructure.
The Observed Attack Chain (Real-World Case)
Stage 0: Authenticated Phishing Email
The attack began with a fully authenticated email:
Delivered via Postmark
SPF/DKIM passed
DMARC non-enforcing
The email impersonated an internal project collaboration invite, a workflow users are conditioned to trust.
Key detail:
The email did not contain a phishing domain.
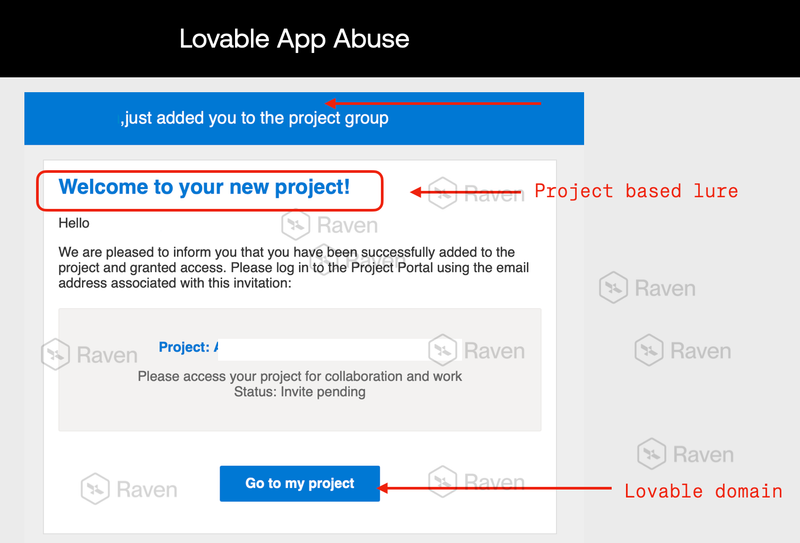
Stage 1: Lovable as the Redirector
The call-to-action linked to: https://<random-string>.lovable.app
At this stage:
No Microsoft branding
No credential prompt
No obvious malicious content
This page acted as:
A traffic broker
A logic layer
A trust buffer
Security scanners detonating the URL would often see nothing malicious.
Stage 2: Dynamic Redirection to Final Phish
After user interaction, the Lovable page redirected to:
https://<attacker-domain>.com/s/?<encoded-parameters>
This destination hosted a pixel-perfect Microsoft sign-in page designed to harvest credentials.
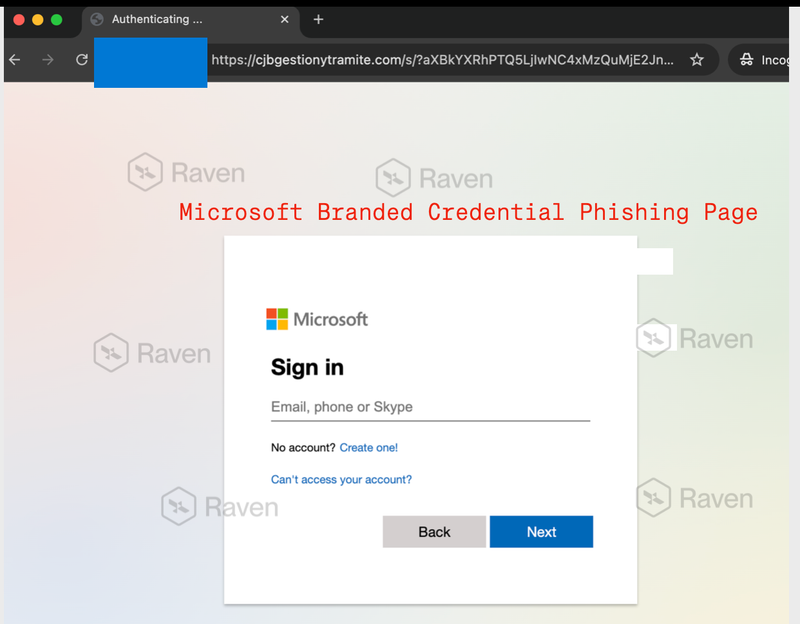
Key techniques observed:
Encoded URL parameters (tracking / session binding)
Browser-based conditional behavior
Clean Microsoft UI with no tenant branding
No microsoft.com domains involved
At this point, credential theft occurs.
Why Lovable Is the Perfect Phishing Middleman
Lovable (and similar platforms) provide attackers with several structural advantages:
1. Trust Inheritance
Security tools hesitate to aggressively block:
*.lovable.app
Low-code platforms
Developer ecosystems
Blocking them outright risks business disruption.
2. IOC Decoupling
The phishing email never references the final malicious domain.
This breaks:
URL reputation
Retroactive search
Threat intelligence sharing
By the time the final domain is blocked, the Lovable URL remains reusable.
3. Infinite Payload Rotation
Attackers can:
Swap redirect destinations
Change logic per region
Rotate credential harvesters
Reuse the same email template
All without changing the phishing email.
4. Scan Evasion by Design
Vibe-coded apps can:
Redirect only after clicks
Require JS execution
Delay payload delivery
Serve benign content to bots
This defeats static and sandbox-based detection.
5. The Content Did Not Trigger Strong NLP Signals
The email body:
Contained no threats
Contained no urgency language
Contained no financial lure
Contained no attachments
Looked like a normal project invite
It intentionally avoided:
“Verify your account
“Action required”
“Security alert”
“Password reset”
This weakens language-based phishing classifiers.
Why This Is Not Just a “Lovable Problem”
Lovable is not uniquely vulnerable - it is simply early in being abused.
This pattern applies to:
Any low-code platform
Any app builder with shared hosting
Any SaaS that allows arbitrary redirects
This is a systemic shift, not a single-platform flaw.
How Ravenmail caught this attack?
This attack was blind to Email Gateway and Microsoft Defender, Ravenmail was able to detect it using context-aware security that reasons out anomalies and provides a verdict. In this case
Project based domains come from either within org or closely related entities - this had none
Lovable domain is unrelated to the context of the email and suspicious in the project context
The subject has hash string which was unusual
Overall verdict on the unusual usage of the link in context to Project based content.
Overall Context-aware security is able to find better emerging patterns than signature based solutions.
To protect your organization from emerging zero-days, reach out to us for a free PoC.
Comments
Your comment has been submitted